A new infrastructure linked to GrayAlpha, a cybercriminal entity overlapping with the notorious FIN7 group, has been exposed. This financially…
A sophisticated ransomware operation known as BERT has significantly expanded its capabilities by developing weaponized ELF (Executable and Linkable Format)…
In just a few months, Donald Trump’s second presidential term has drastically reshaped the United States federal government and moved…
Threat actors have exploited Discord’s invite system to distribute malicious links, ultimately delivering AsyncRAT and other harmful payloads. Discord, a…
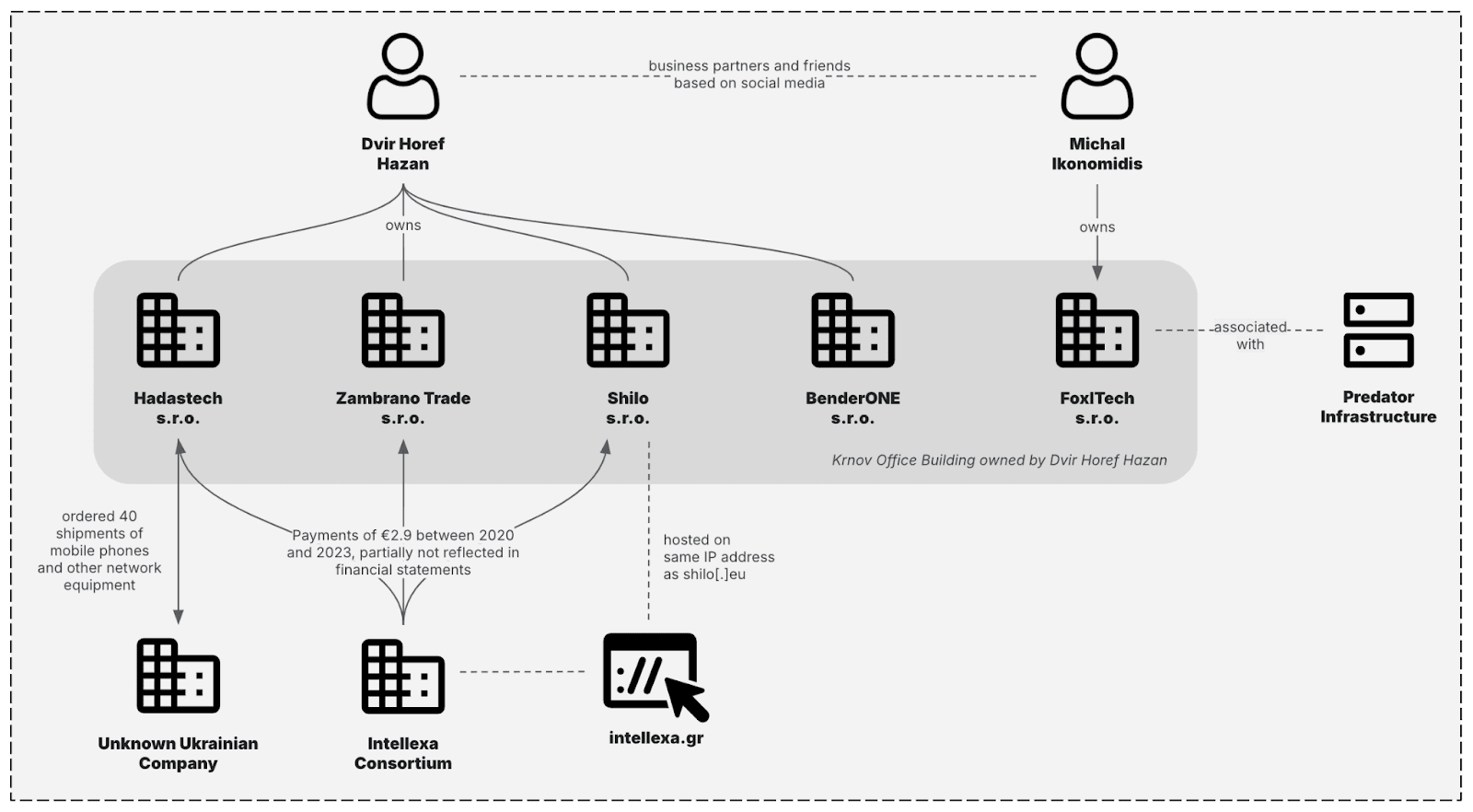
New Predator spyware infrastructure revealed activity in Mozambique for the first time Pierluigi Paganini June 16, 2025 Insik Group analyzed…
Microsoft acknowledged a new issue caused by the June 2025 security updates, causing the DHCP service to freeze on some…
I don’t think there’s anything quite so satisfying as winning a fight—especially when you land that victory with a resounding…
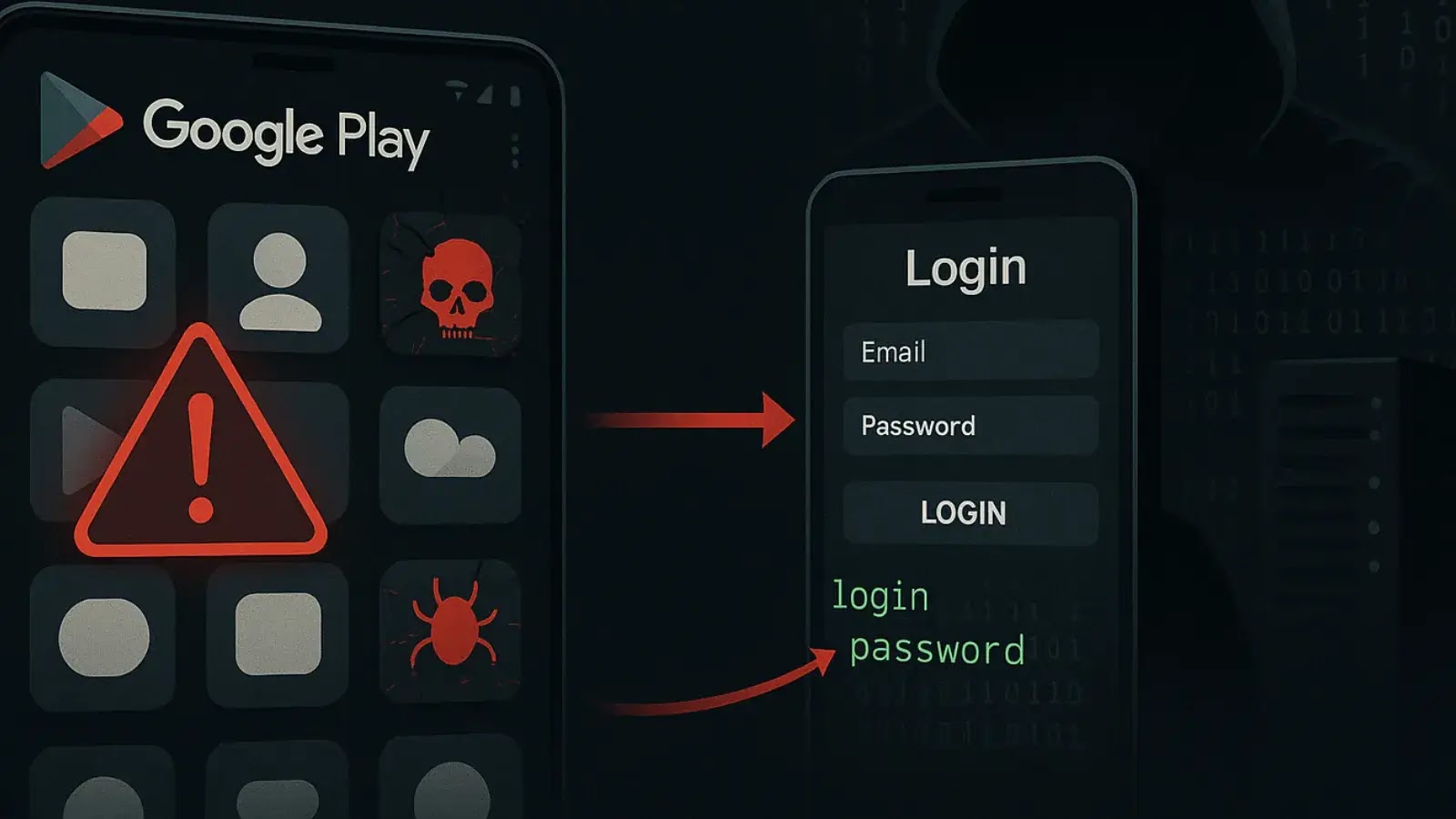
A major security alert has been issued for Android users after cybersecurity researchers uncovered more than 20 malicious applications on…
Penetration Testing as a Service (PTaaS) must align with core industry standards, regulations, and certifications. This is usually done to…
A critical security vulnerability has been identified in IBM’s Backup, Recovery, and Media Services (BRMS) for IBM i, potentially exposing…
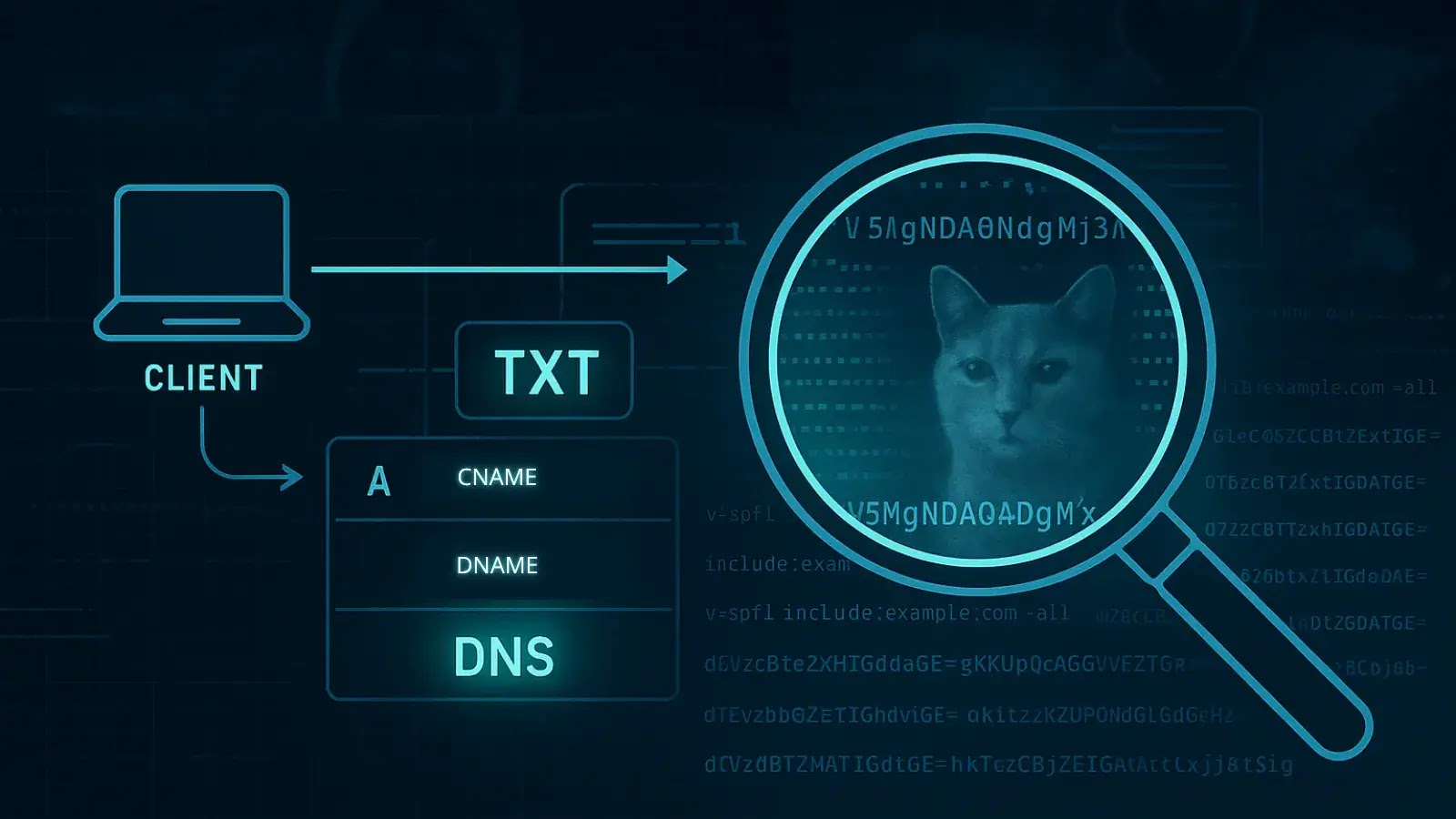
A curious technique has emerged: hiding images inside DNS TXT records. This approach, which at first glance seems unorthodox, leverages the…
A curious technique has emerged: hiding images inside DNS TXT records. This approach, which at first glance seems unorthodox, leverages the…