Google Cloud experienced one of its most significant outages in recent years, disrupting a vast array of services and impacting…
Getting a call saying a family member has been kidnapped is terrifying. Fear and panic take over, making it hard…
Cybersecurity researchers have discovered a malicious package on the Python Package Index (PyPI) repository that’s capable of harvesting sensitive developer-related…
In this Help Net Security interview, Rich Friedberg, CISO at Live Oak Bank, discusses how banks can better align cybersecurity…
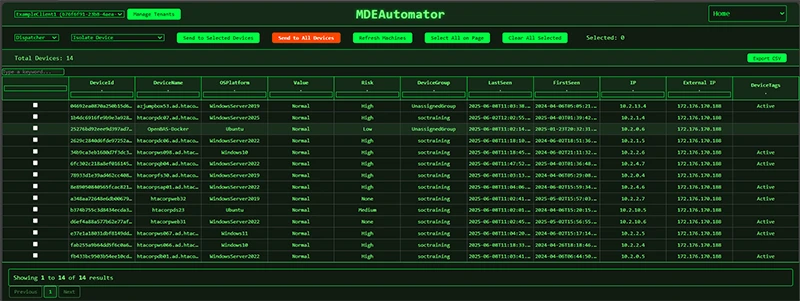
Managing endpoints and responding to security incidents in Microsoft Defender for Endpoint (MDE) can be time-consuming and complex. MDEAutomator is…
Kali Linux has long been the go-to operating system for penetration testers and security professionals, and Learning Kali Linux, 2nd…
Australian organisations are vulnerable to cybersecurity attackers taking advantage of single points of failure, lack of continuous monitoring and insufficient…
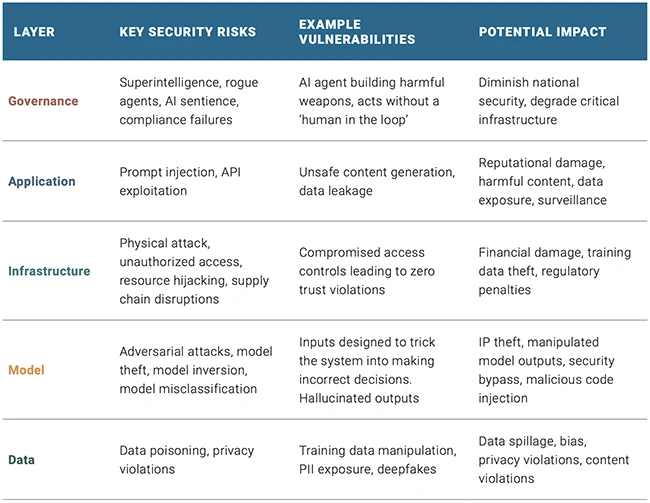
As AI spreads, so do the risks. Security leaders are being asked to protect systems they don’t fully understand yet,…
Australian organisations previously overwhelmed by cybersecurity alerts are finding significant time savings thanks to Quorum’s AI-driven approach. By integrating Microsoft’s…
Amazon will spend $20 billion between now and 2029 on data centres and related support infrastructure, such as renewable energy….
Governance, risk and compliance (GRC) frameworks are now crucial in helping businesses prioritise cybersecurity investments, said Canary IT at the…
ANZ Banking Group is migrating its entire non-financial risk portfolio to ServiceNow, in a move to strengthen operational resilience across…