Tenable, a prominent cybersecurity provider, has released version 10.8.5 of its Agent software to address three critical security vulnerabilities affecting…
OffSec has released Kali Linux 2025.2, the most up-to-date version of the widely used penetration testing and digital forensics platform….
The coding paradigm is rapidly changing with AI. I’ve heard the term ‘Vibe Coding’ being thrown around, but honestly, I’m…
The cryptocurrency and blockchain development ecosystem is facing an unprecedented surge in sophisticated malware campaigns targeting the open source supply…
Unusual toolset used in recent Fog Ransomware attack Pierluigi Paganini June 14, 2025 Fog ransomware operators used in a May…
A new malware campaign is exploiting a weakness in Discord’s invitation system to deliver an information stealer called Skuld and…
A cyberattack on United Natural Foods caused bread shortages and bare shelves Pierluigi Paganini June 13, 2025 Cyberattack on United…
As protests continue to swell across the United States in response to aggressive Immigration and Customs Enforcement actions, civilians are…
Cybersecurity professionals and business leaders are on high alert following a confirmed breach of a utility billing software provider, traced…
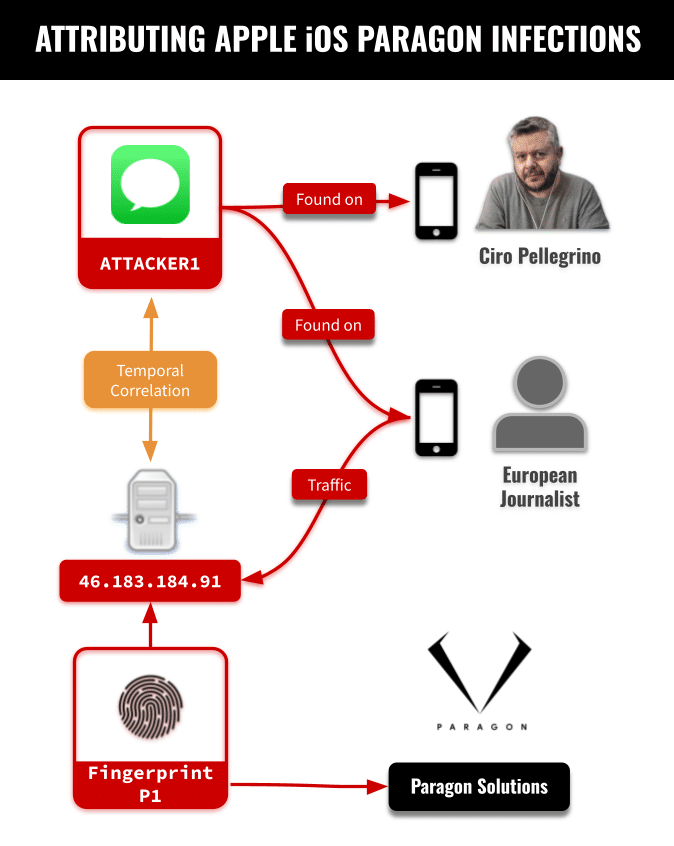
Apple has fixed a vulnerability that was used in zero-click attacks that installed Paragon Graphite spyware on the iPhones of…
Paraguay Suffered Data Breach: 7.4 Million Citizen Records Leaked on Dark Web Pierluigi Paganini June 13, 2025 Resecurity researchers found…
Google says an API management issue is behind Thursday’s massive Google Cloud outage, which disrupted or brought down its services…