The Black Hat USA 2025 two-day main conference on Aug. 6 and 7 will feature more than 100 selected Briefings. Some of the…
Microsoft is investigating an ongoing incident that is causing users to experience errors with some Microsoft 365 authentication features. As…
A sophisticated new attack method called “SmartAttack” that can breach supposedly secure air-gapped computer systems using smartwatches as covert data…
A critical vulnerability (CVE-2025-6031) has been identified in Amazon Cloud Cam devices, which reached end-of-life (EOL) status in December 2022….
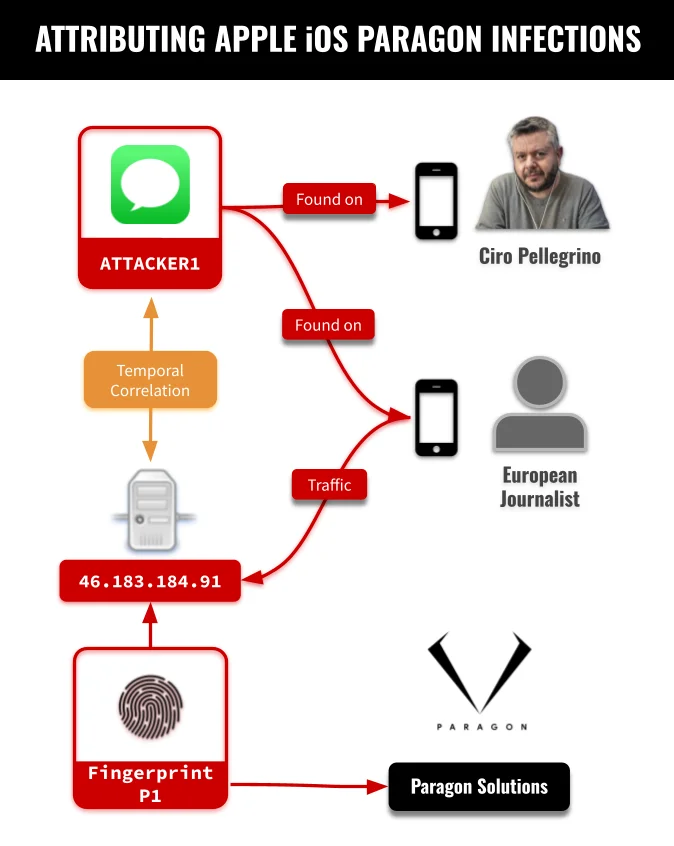
A zero-click attack leveraging a freshly disclosed Messages vulnerability (CVE-2025-43200) has infected the iPhones of two European journalists with Paragon’s…
Introduction: Security at a Tipping Point Security Operations Centers (SOCs) were built for a different era, one defined by perimeter-based…
Victoria’s Secret has restored all critical systems impacted by a May 24 security incident that forced it to shut down…
Cybersecurity researchers have identified a sophisticated new phishing campaign that exploits GitHub’s OAuth2 device authorization flow to compromise developer accounts…
A newly disclosed spoofing vulnerability (CVE-2025-26685) in Microsoft Defender for Identity (MDI) enables unauthenticated attackers to capture Net-NTLM hashes of…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday disclosed that ransomware actors are targeting unpatched SimpleHelp Remote Monitoring…
A significant security vulnerability in HashiCorp Nomad workload orchestrator that allows attackers to escalate privileges by exploiting the Access Control…
Apple confirmed that Messages app flaw was actively exploited in the wild Pierluigi Paganini June 13, 2025 Apple confirmed that…