Alerts about operations are disseminated through direct messages, WhatsApp, or posts on each page’s feed. In turn, it is possible…
A newly discovered remote access trojan (RAT) named CyberEye is making waves in the cybersecurity community for its sophisticated capabilities and its…
Forensic investigation has confirmed the use of Paragon’s Graphite spyware platform in zero-click attacks that targeted Apple iOS devices of…
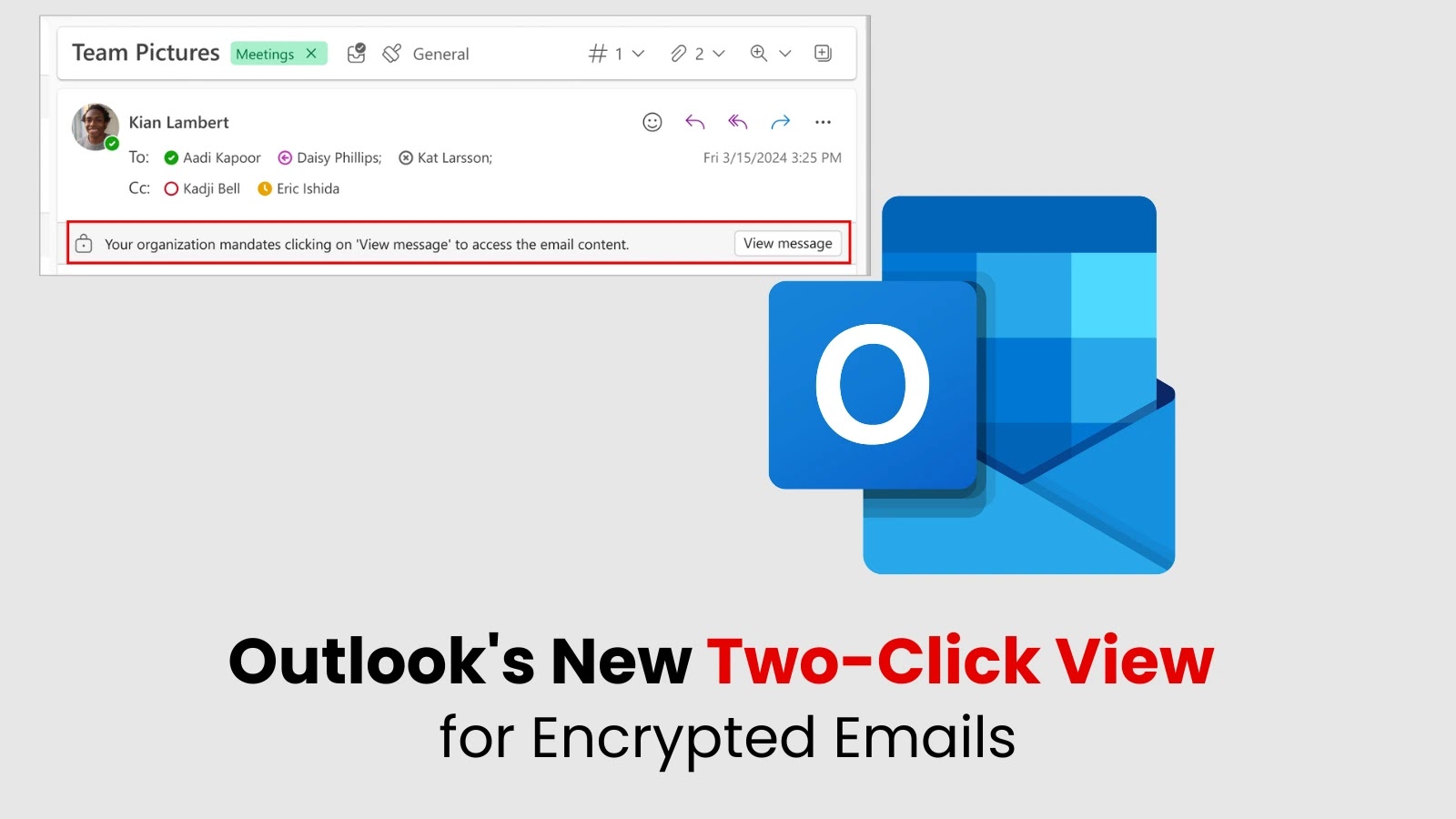
Microsoft is set to launch a significant security enhancement for Outlook users across multiple platforms. Starting April 2025, the company…
A dramatic escalation in phishing attacks leveraging Adversary-in-the-Middle (AiTM) techniques has swept across organizations worldwide in early 2025, fueled by…
Cybersecurity firm Cloudflare has issued a stark warning about the escalating threat landscape facing independent media organizations worldwide, revealing that…
A critical security vulnerability in OneLogin’s Active Directory (AD) Connector service has exposed enterprise authentication systems to significant risk The…
Attackers are using the TeamFiltration pentesting framework to brute-force their way into Microsoft Entra ID (formerly Azure AD) accounts, Proofpoint…
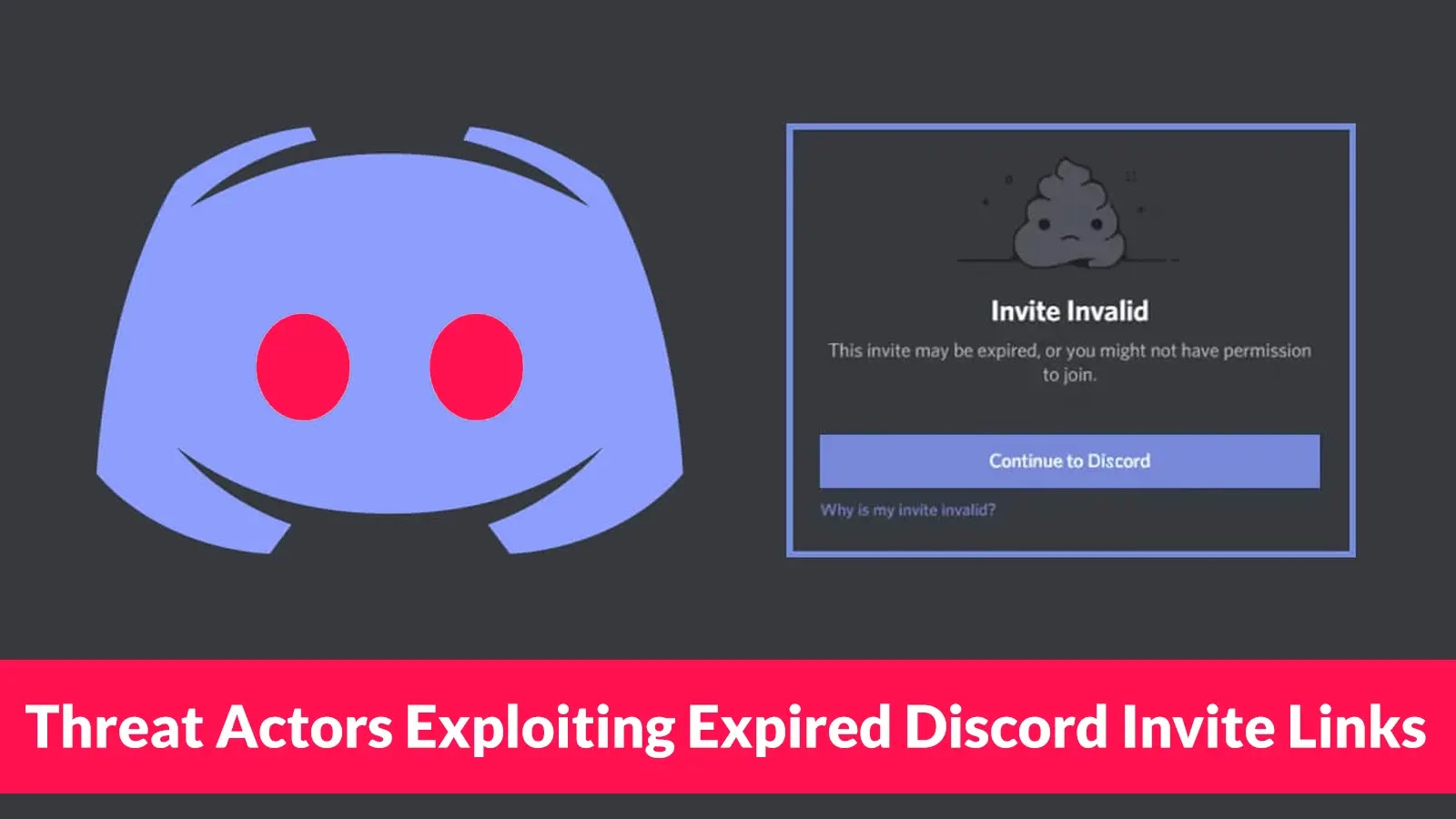
Cybercriminals have discovered a sophisticated new attack vector that exploits a critical flaw in Discord’s invitation system, allowing them to…
The cybersecurity landscape has witnessed the emergence of increasingly sophisticated ransomware operations, with DragonForce standing out as a particularly concerning…
The theme of this year’s RSAC is “Many Voices. One Community.” While our field can rightly claim “many voices”, portraying…
Microsoft has addressed multiple critical issues affecting Windows Server 2025 domain controllers through its June 2025 Patch Tuesday updates, resolving…