Organizations worldwide are facing an unprecedented surge in sophisticated phishing attacks that specifically target Microsoft 365 and Google accounts through…
Palo Alto Networks disclosed a medium-severity command injection vulnerability on June 11, 2025, designated as CVE-2025-4231, affecting the management web…
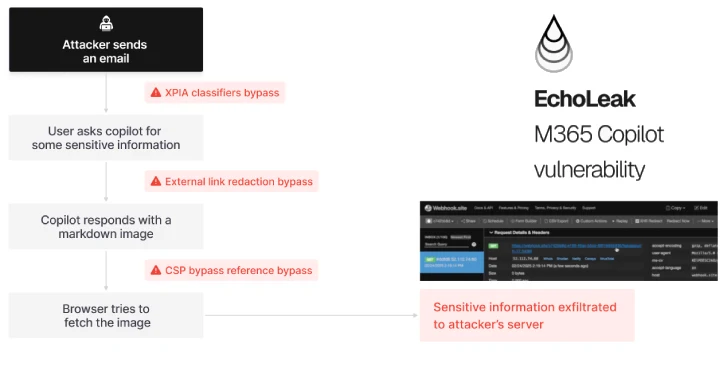
Cybersecurity firm Aim Labs has uncovered a serious new security problem, named EchoLeak, affecting Microsoft 365 (M365) Copilot, a popular…
Human identities management and control is pretty well done with its set of dedicated tools, frameworks, and best practices. This…
GitLab has released security updates to address multiple vulnerabilities in the company’s DevSecOps platform, including ones enabling attackers to take…
Threat actors are allegedly offering the complete source code of a sophisticated Malware-as-a-Service (MaaS) botnet for sale. This advanced malicious…
Trend Micro has issued an urgent security bulletin addressing five critical vulnerabilities in its Apex One endpoint security platform that…
A novel attack technique named EchoLeak has been characterized as a “zero-click” artificial intelligence (AI) vulnerability that allows bad actors…
Financiers picked up the pace of funding in artificial intelligence (AI) infrastructure in Sweden last month, after an urgent government…
SinoTrack GPS device flaws allow remote vehicle control and location tracking Pierluigi Paganini June 12, 2025 Two vulnerabilities in SinoTrack…
Multiple critical security vulnerabilities in the Trend Micro Apex One enterprise security platform could enable attackers to inject malicious code and escalate…
MPs are to investigate the risks and opportunities of digital identity in the UK, as Labour influencers increasingly call for…