In recent years, manufacturing has dramatically modernized, particularly with the implementation of new tools such as generative AI. Contemporary production…
Fog ransomware hackers are using an uncommon toolset, which includes open-source pentesting utilities and a legitimate employee monitoring software called Syteca. The…
Proofpoint Threat Intelligence has uncovered a large-scale Account Takeover (ATO) campaign, internally tracked as UNK_SneakyStrike, that leverages the open-source penetration…
Salesforce has released survey data that says 78% of UK organisations are using agentic artificial intelligence (AI). The findings, provided…
CISA and international cybersecurity partners have released a comprehensive suite of guidance documents aimed at protecting critical network edge devices…
A newly disclosed vulnerability, CVE-2025-33073, dubbed the “Reflective Kerberos Relay Attack,” has shaken the Windows security landscape. Discovered by RedTeam…
Jun 12, 2025Ravie LakshmananVulnerability / Software Security ConnectWise has disclosed that it’s planning to rotate the digital code signing certificates…
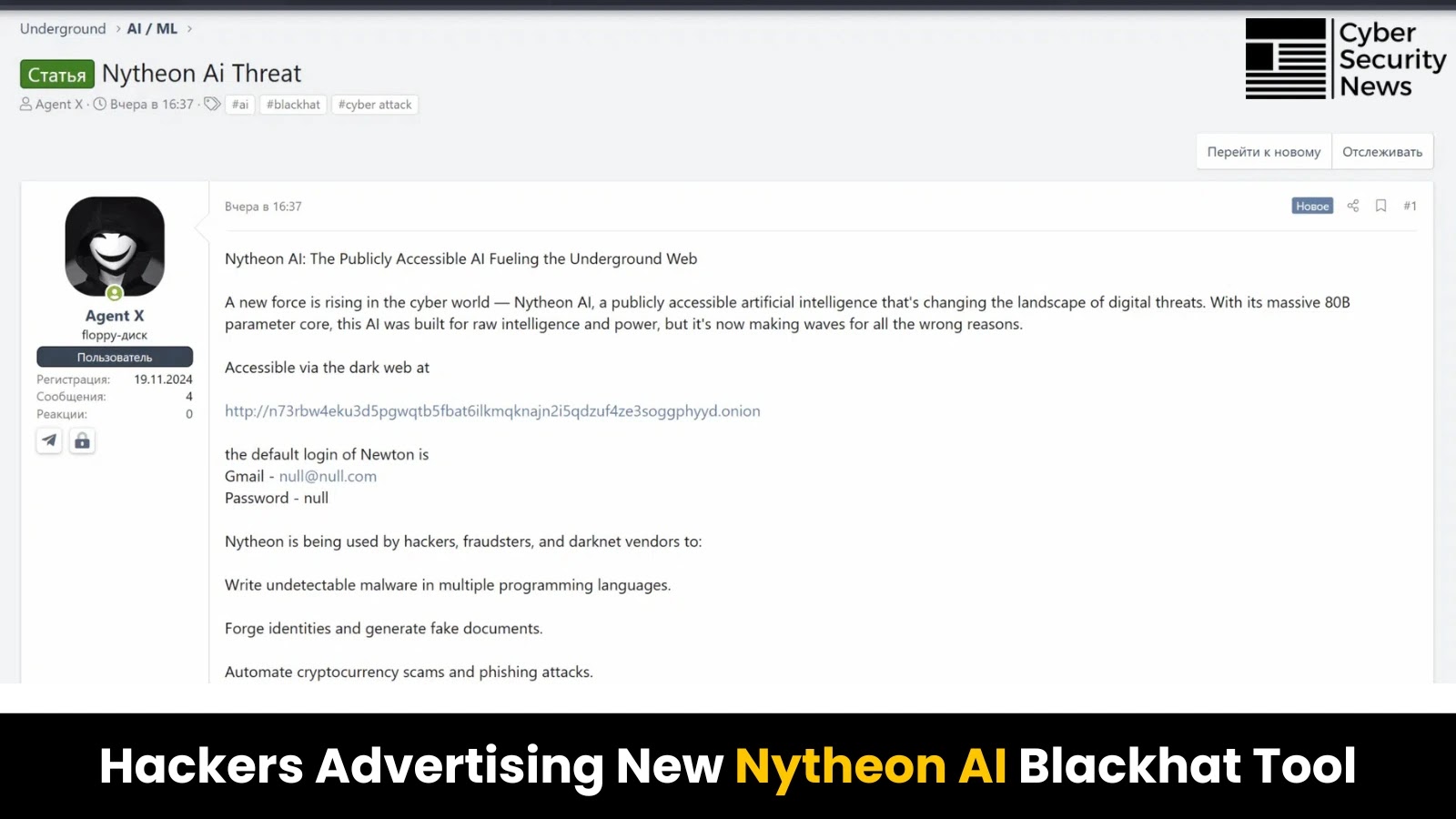
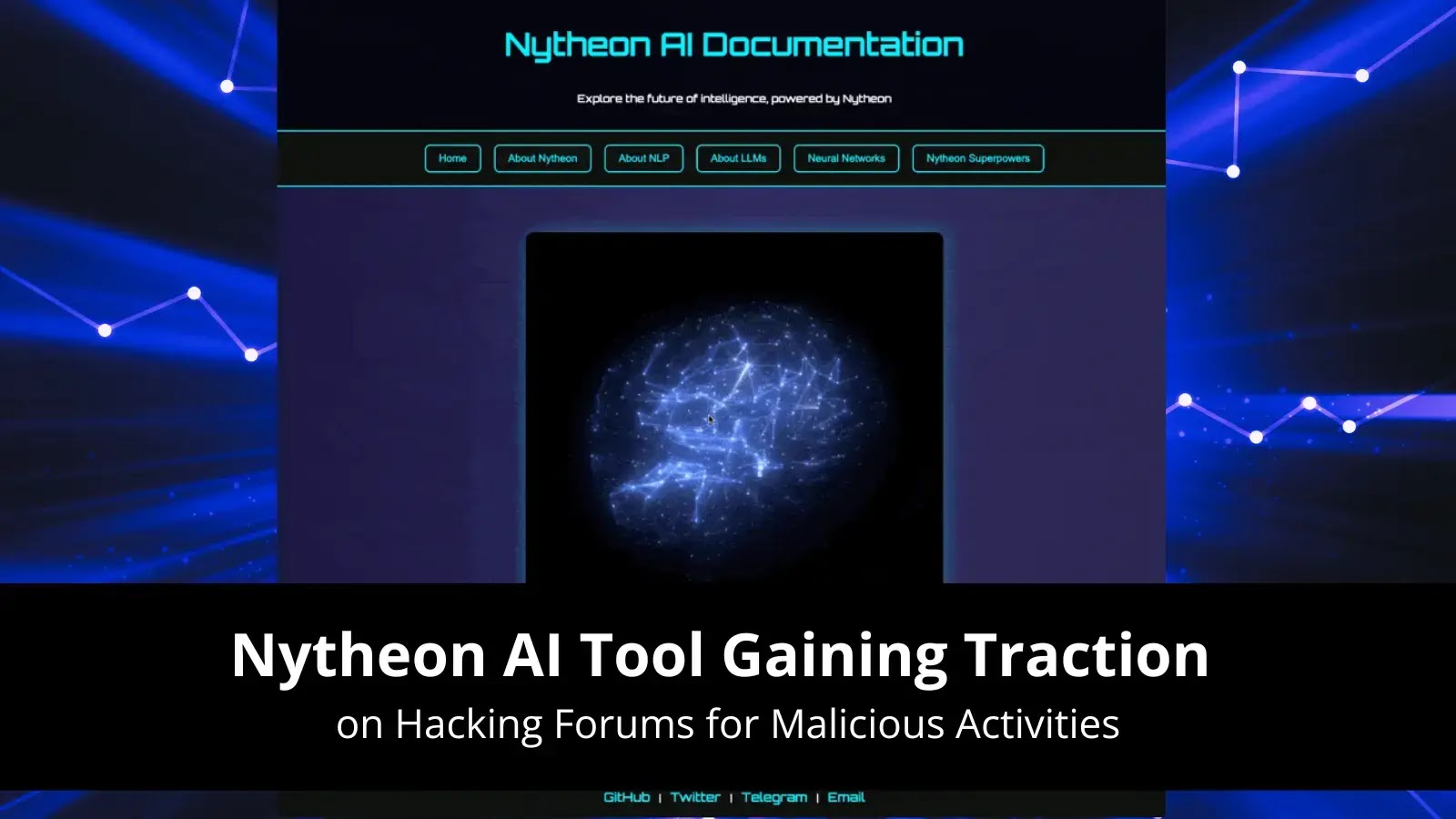
A sophisticated new threat platform, Nytheon AI, has emerged, which combines multiple uncensored large language models (LLMs) built specifically for…
Security researchers have uncovered the first-ever zero-click vulnerability in an AI agent, targeting Microsoft 365 Copilot and potentially exposing sensitive…
Lemony announced its on-premise artificial intelligence solution that is redefining how organizations deploy generative AI. Lemony’s secure, hardware-based node offers…
Exposed eyes: 40,000 security cameras vulnerable to remote hacking Pierluigi Paganini June 12, 2025 Over 40,000 internet-exposed security cameras worldwide…
The emergence of Nytheon AI marks a significant escalation in the landscape of uncensored large language model (LLM) platforms. Unlike…