A cybersecurity hobbyist has built a compact, foldable mobile hacking rig that runs Kali NetHunter on a Google Pixel 3…
Nestled in a log cabin high in the Rocky Mountains, Rick Bohm starts his day the same way he’s approached…
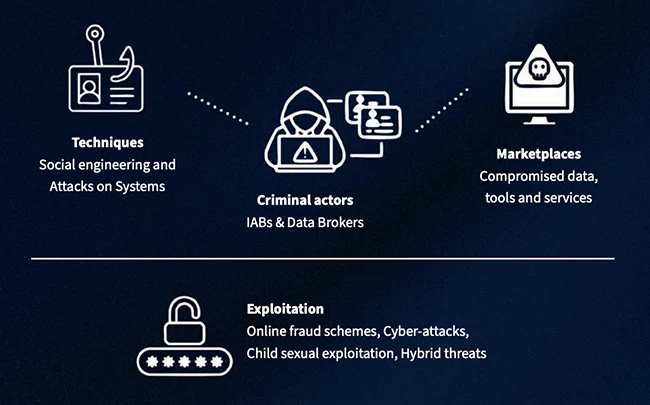
Cybercriminals are stealing data and running full-scale businesses around it. Europol’s latest Internet Organised Crime Threat Assessment (IOCTA) report reveals…
The Cybersecurity and Infrastructure Security Agency (CISA), in partnership with international cybersecurity authorities, announced the release of comprehensive guidance to…
CISOs understand that threat modeling helps teams identify risks early and build safer systems. But outside the security org, the…
Jun 12, 2025Ravie LakshmananEnterprise Security / Active Directory Cybersecurity researchers have uncovered a new account takeover (ATO) campaign that leverages…
98% of CISOs face challenges when using threat intelligence, according to Trellix. The biggest problems are keeping up with changing…
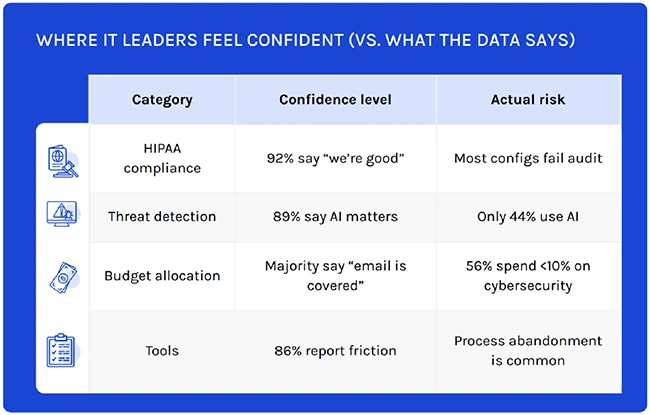
92% of healthcare IT leaders say they’re confident in their ability to prevent email-based data breaches, but according to Paubox,…
A critical zero-click vulnerability in Microsoft 365 Copilot, dubbed “EchoLeak,” enables attackers to automatically exfiltrate sensitive organizational data without requiring…
Nearly half of of mobile users encounter mobile scams daily, with people in the US and UK more likely to…
The Northern Beaches Women’s Shelter (NBWS) is seeking assistance on behalf of vulnerable women experiencing technology-enabled and cyber abuse, a…
Webjet Group has appointed Oonagh Flanagan as its first chief marketing officer in Australia as it enters a “new era…