Microsoft confirmed on Tuesday that it’s pushing a revised security update targeting some Windows 11 24H2 systems incompatible with the…
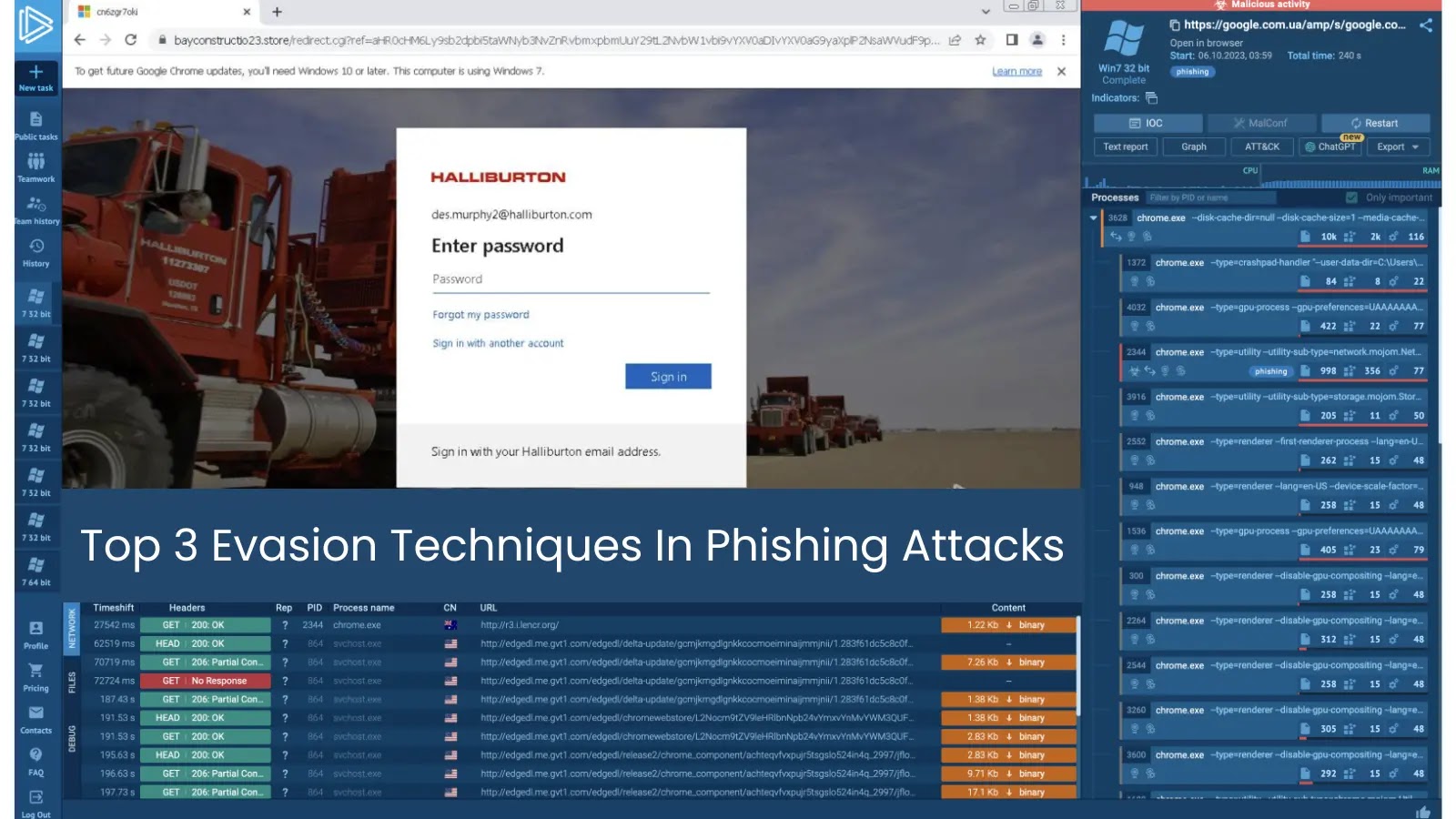
Phishing attacks aren’t what they used to be. Hackers no longer rely on crude misspellings or sketchy email addresses. Instead,…
Microsoft’s Patch Tuesday updates for June 2025 include fixes for an actively exploited zero-day vulnerability and nine additional flaws at…
A recently fixed critical vulnerability in Microsoft’s Copilot AI tool could have let a remote attacker steal sensitive data from…
An APT hacking group known as ‘Stealth Falcon’ exploited a Windows WebDav RCE vulnerability in zero-day attacks since March 2025 against…
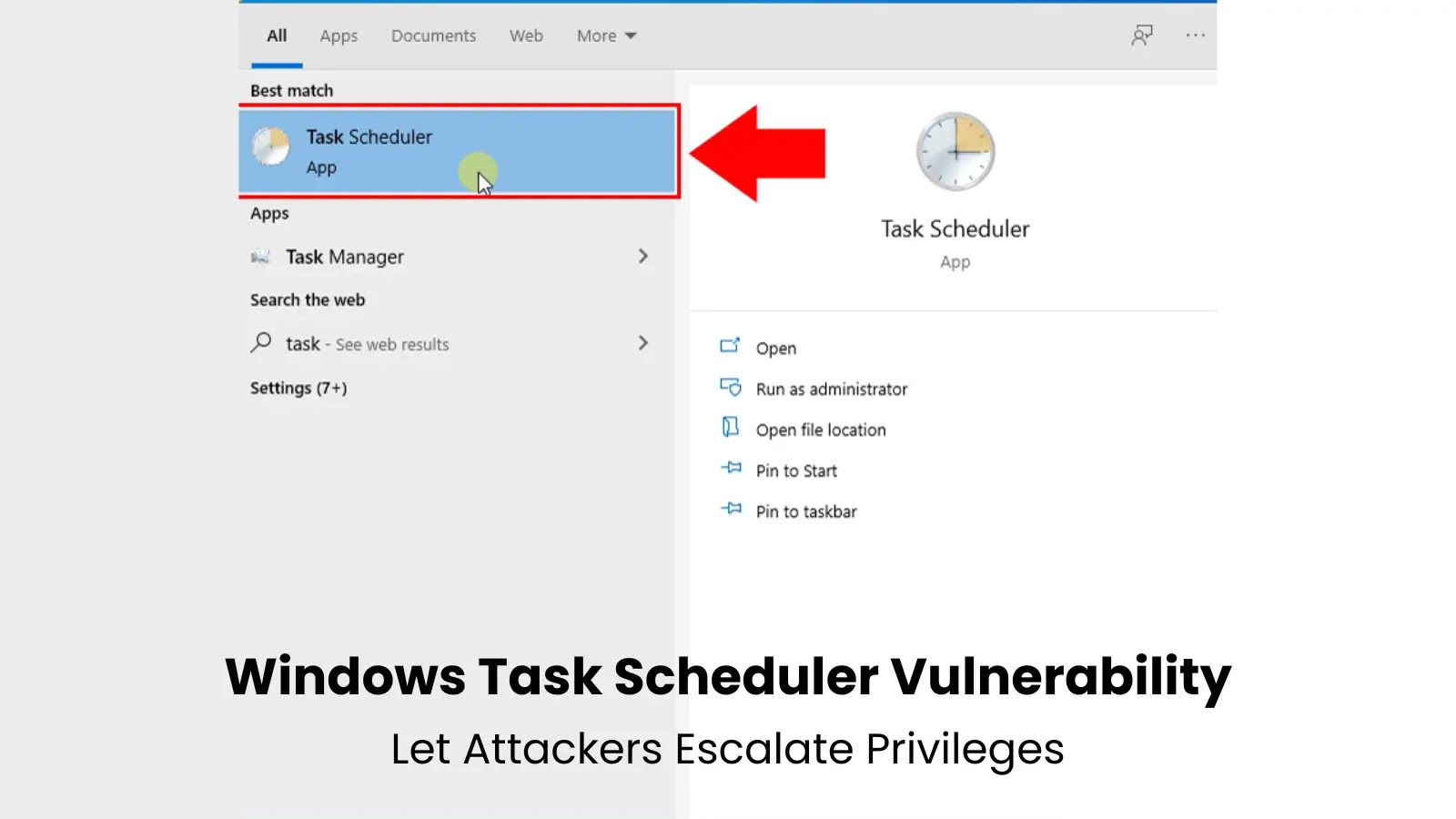
A significant security vulnerability in Windows Task Scheduler could allow attackers to escalate their privileges to SYSTEM level access without…
Jun 11, 2025Ravie LakshmananNetwork Security / Threat Intelligence Threat intelligence firm GreyNoise has warned of a “coordinated brute-force activity” targeting…
A coordinated campaign of brute-force attacks using hundreds of unique IP addresses targets Apache Tomcat Manager interfaces exposed online. Tomcat…
Microsoft addressed a critical security flaw (CVE-2025-32713) in the Windows Common Log File System (CLFS) driver during its June 2025…
Connectwise customers who use the company’s ScreenConnect, Automate, and ConnectWise RMM solutions are urged to update all agents and/or validate…
West Brom Building Society is embarking on a three-stage project to build the digital capabilities its customers want. The organisation,…
Listen to the article 8 min This audio is auto-generated. Please let us know if you have feedback. NATIONAL HARBOR,…