An international law enforcement action codenamed “Operation Secure” targeted infostealer malware infrastructure in a massive crackdown across 26 countries, resulting…
A critical elevation of privilege vulnerability has been identified in the Windows Task Scheduler service, tracked as CVE-2025-33067. Officially published…
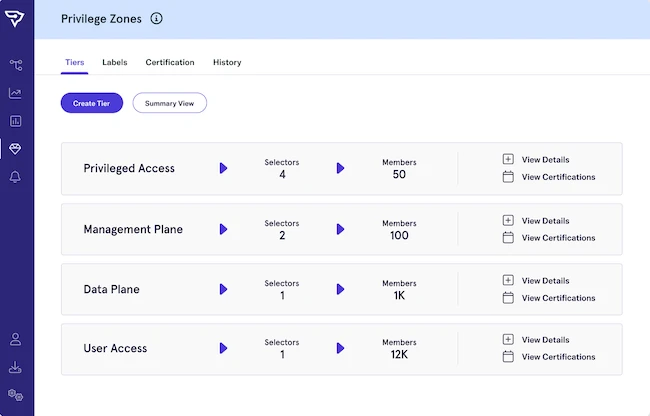
SpecterOps introduced Privilege Zones, a new addition to its flagship BloodHound Enterprise platform. Privilege Zones enable teams to define custom…
The government is using national security as a “smokescreen” to refuse to disclose how many technical capability notices (TCNs) it…
Microsoft has resolved a known issue that caused some Windows Server 2025 domain controllers to become unreachable after a restart…
Ransomware attacks are no longer just a cybersecurity concern – they are a direct threat to national security. A recent study found…
Microsoft has disclosed four critical remote code execution (RCE) vulnerabilities in its Office suite as part of the June 2025…
An international cybercrime operation coordinated by INTERPOL has led to the takedown of more than 20,000 malicious IPs and domains…
Cybersecurity Ventures predicts that by 2031, ransomware could potentially cause a business (or consumer) to fall victim every two seconds. This…
In today’s cybersecurity landscape, much of the focus is placed on firewalls, antivirus software, and endpoint detection. While these tools…
Over half of cyber security professionals lose sleep due to work-related stress, according to research by the Chartered Institute of…
Microsoft has fixed a known issue causing authentication problems on Windows Server domain controllers after installing the April 2025 security…