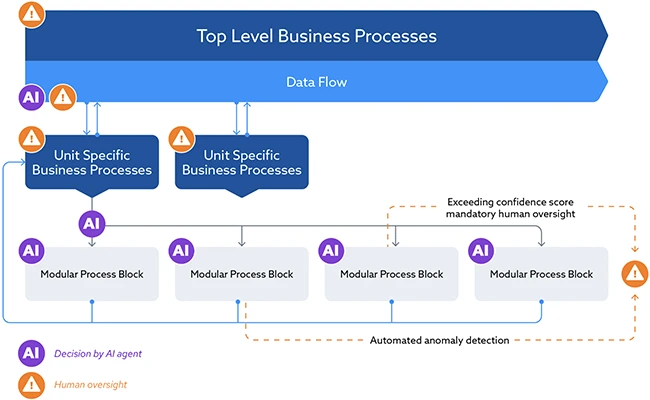
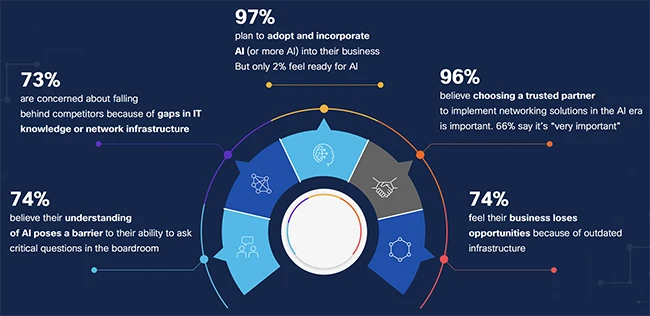
Twenty years ago, could anyone have predicted that we would be relying on artificial intelligence (AI) to make critical business…
A critical vulnerability (CVE-2025-4275) in Insyde H2O UEFI firmware allows attackers to bypass Secure Boot protections by injecting malicious digital…
In cybersecurity, there’s an urge to collect as much data as possible. Logs, alerts, metrics, everything. But more data doesn’t…
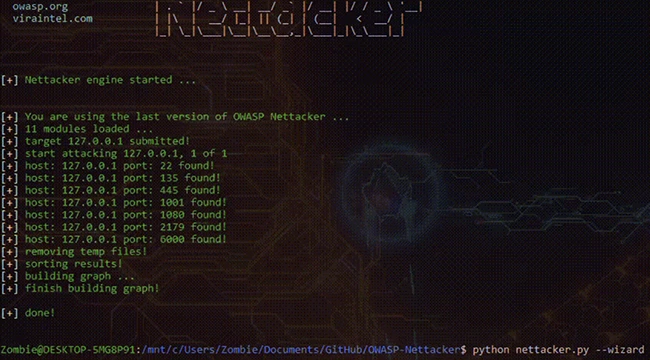
OWASP Nettacker is a free, open-source tool designed for network scanning, information gathering, and basic vulnerability assessment. Built and maintained…
The board of directors have announced the winding up of the Australian Cyber Network. The ACN was established to serve…
AI is supposed to make businesses faster, smarter, and more competitive, but most projects fall short. The Cloud Security Alliance…
As AI assistants, agents, and data-driven workloads reshape how work gets done, they’re creating more latency-sensitive, and more complex network…
In the age of rapidly advancing artificial intelligence, where powerful algorithms can predict human behaviour and model global patterns, we…
SentinelOne has announced the Australian winners of its 2025 APJ PartnerOne Awards, recognising their outstanding contributions to innovation in security…
Microsoft today released security updates to fix at least 67 vulnerabilities in its Windows operating systems and software. Redmond warns…
As Apple’s Worldwide Developers Conference keynote concluded on Monday, market watchers couldn’t help but notice that the company’s stock price was…
Microsoft’s June Patch Tuesday update has landed, bringing security fixes for 66 vulnerabilities across its product line. Among the patched…