Microsoft’s latest Patch Tuesday update landed on schedule around teatime on 10 June, with admins facing a much lighter load…
In a twist on typical hiring-related social engineering attacks, the FIN6 hacking group impersonates job seekers to target recruiters, using…
Fortinet has released security updates addressing multiple vulnerabilities across its product portfolio, including FortiOS, FortiAnalyzer, FortiProxy, and FortiWeb systems. The…
Microsoft has released its June 2025 Patch Tuesday security updates, addressing a total of 66 vulnerabilities across its software ecosystem….
Jun 10, 2025Ravie LakshmananVulnerability / Cloud Security Adobe on Tuesday pushed security updates to address a total of 254 security…
A House panel approved a fiscal 2026 funding bill Monday that would cut the Cybersecurity and Infrastructure Security Agency by…
Microsoft has released the KB5060533 cumulative update for Windows 10 22H2 and Windows 10 21H2, with seven fixes or changes,…
Microsoft has released its monthly Patch Tuesday updates, addressing a total of 66 vulnerabilities in its product suite. This release…
ESET, a leading cybersecurity firm, has shed light on the intricate nature of digital footprints the data trails left by…
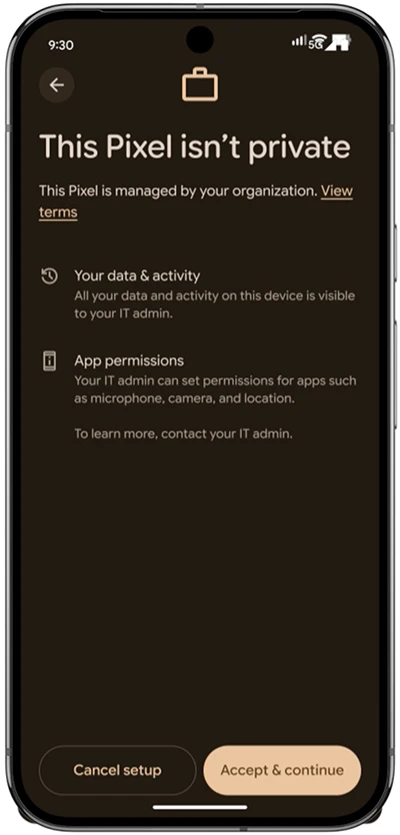
Google is rolling out new Android Enterprise features aimed at improving mobile security, IT management, and employee productivity. According to…
SAP June 2025 Security Patch Day fixed critical NetWeaver bug Pierluigi Paganini June 10, 2025 SAP fixed a critical NetWeaver…
Microsoft has released Windows 11 KB5060842 and KB5060999 cumulative updates for versions 24H2 and 23H2 to fix security vulnerabilities and issues, including 66 flaws. Today’s…