The Com doesn’t fit into a traditional definition of cybercrime. While the majority of groups tend to either be financially-motivated…
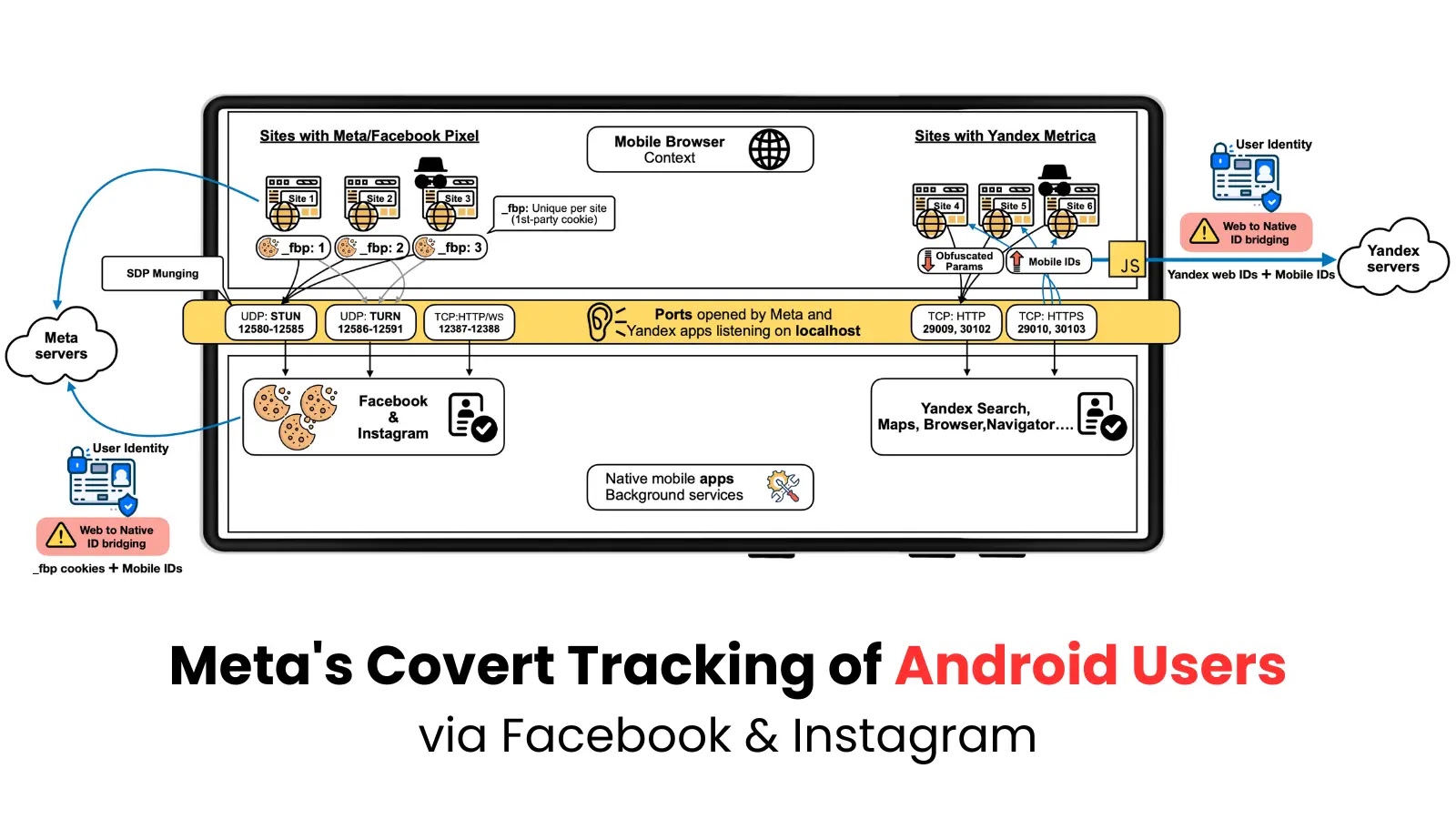
A sophisticated tracking method employed by Meta (Facebook) and Yandex that potentially affected billions of Android users through covert web-to-app…
Google has highlighted a significant uptick in cyberattacks and scams targeting US consumers, with a particular focus on stealing login…
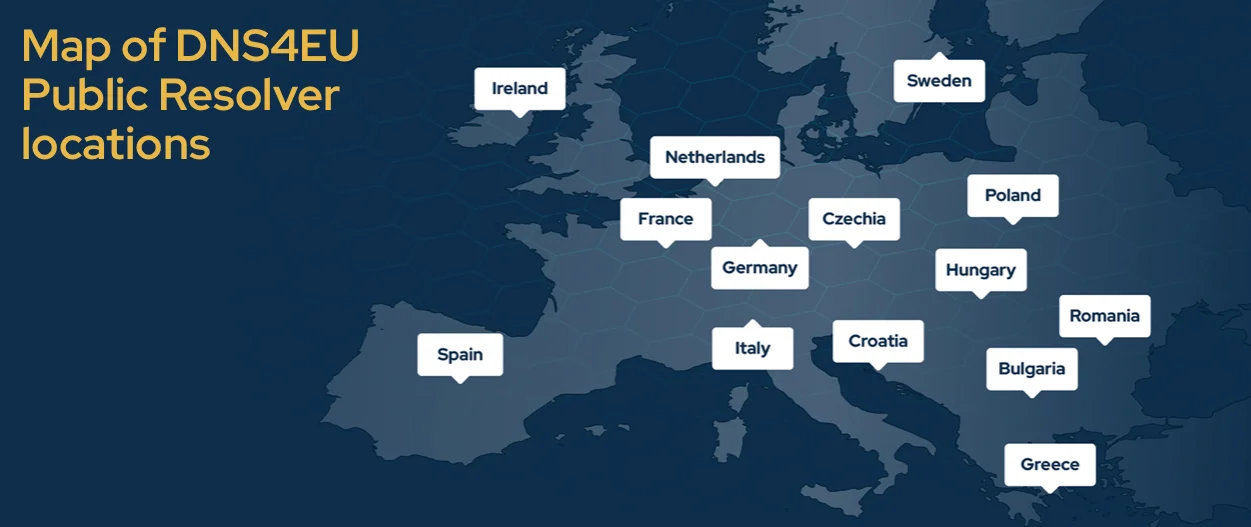
DNS4EU, an EU-based DNS resolution service created to strengthen European Union’s digital sovereignty, has become reality. What is DNS? The…
In cybersecurity, Blue Teams are responsible for defending an organization’s IT environment, including networks, endpoints, applications, and data against various…
A sophisticated scam operation dubbed “GhostVendors” that exploits over 4,000 fraudulent domains to impersonate dozens of major brands and defraud…
A cybersecurity researcher was able to figure out the phone number linked to any Google account, information that is usually…
A new Windows-based malware named Blitz has been identified in 2024, with an updated version detected in early 2025. This…
A vast array of student information is collected under protective measures in secondary schools and colleges, yet the pupils are…
United Natural Foods (UNFI), North America’s largest publicly traded wholesale distributor, was forced to shut down some systems following a…
Tel Aviv, Israel, June 9th, 2025, CyberNewsWire Available to the public and debuting at the Gartner Security & Risk Management…
A critical phishing campaign targeting Windows users has been uncovered by FortiGuard Labs, leveraging malicious Excel attachments to exploit a…