BadBox 2.0 botnet infects millions of IoT devices worldwide, FBI warns Pierluigi Paganini June 09, 2025 BadBox 2.0 malware has…
A sophisticated new malware attack vector that manipulates users through fake browser verification prompts designed to mimic legitimate CAPTCHA systems. …
June 6, 2025 – How to update Chrome on every Operating System (Windows, Mac, Linux, Chrome OS, Android, iOS) June…
The drumbeat of news around advances in artificial intelligence (AI) has become impossible to ignore. And yet it still doesn’t…
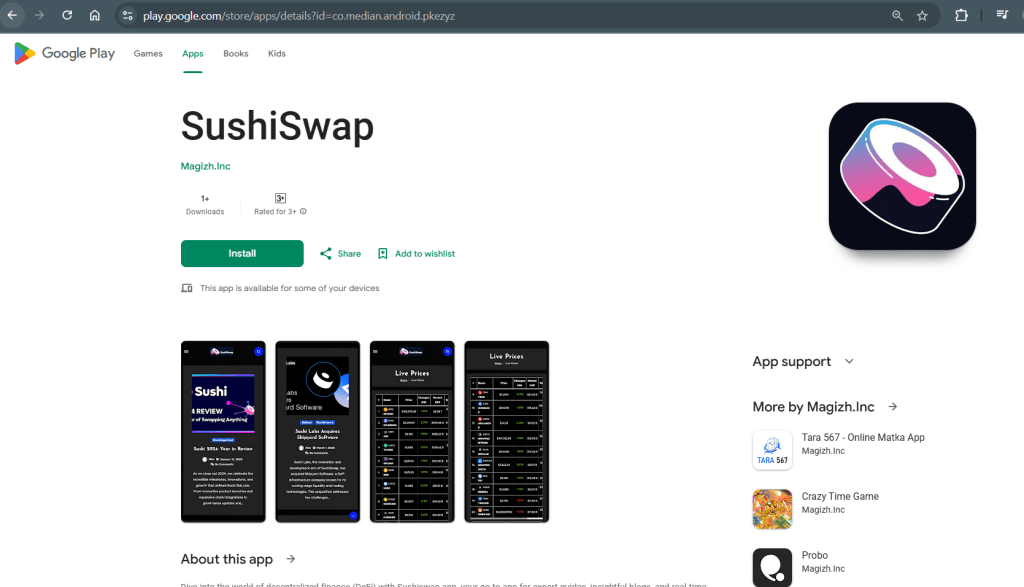
Cyble Research and Intelligence Labs (CRIL) has recently uncovered a malicious crypto phishing campaign where more than 20 malicious applications…
In the rapidly shifting digital world, cybersecurity professionals are constantly seeking innovative tools that not only streamline workflows but also…
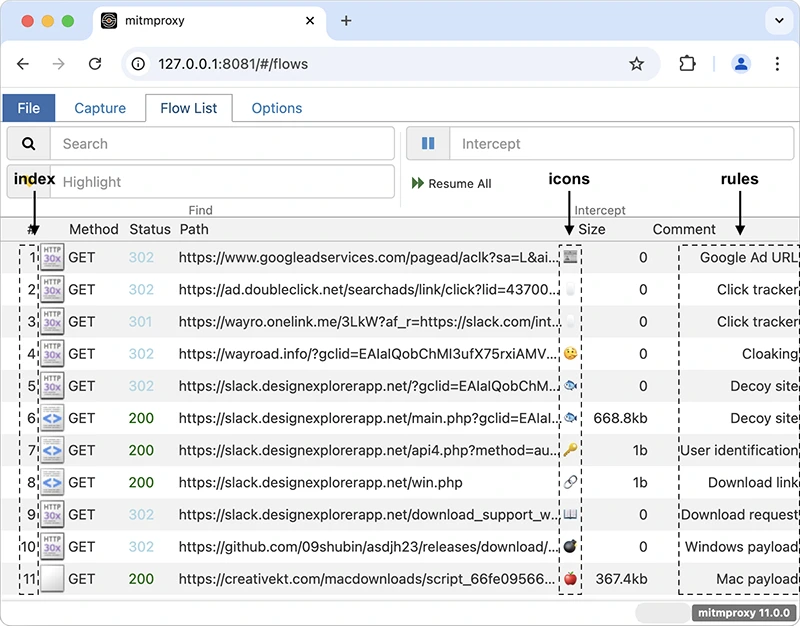
fiddleitm is an open-source tool built on top of mitmproxy that helps find malicious web traffic. It works by checking…
A recent investigation by Genians Security Center (GSC) has uncovered a highly sophisticated, multi-channel cyber espionage campaign attributed to the…
In this Help Net Security interview, Renana Friedlich-Barsky, EVP and CISO at LPL Financial, discusses how threat actors are targeting…
The threat landscape in the bioeconomy is different from what most CISOs are used to. It includes traditional risks like…
Using the MITRE ATT&CK framework as a baseline, organizations are generally improving year-over-year in understanding security information and event management…
In just 12 months, attackers attempted to steal more than $300 million via vendor email compromise (VEC), with 7% of…