On May 15, 2025, Coinbase, the largest U.S. cryptocurrency exchange, publicly disclosed a major security breach that exposed the sensitive…
India, China and the US were the top DDoS attacks targets in Q1 2025, with APAC facing over half of…
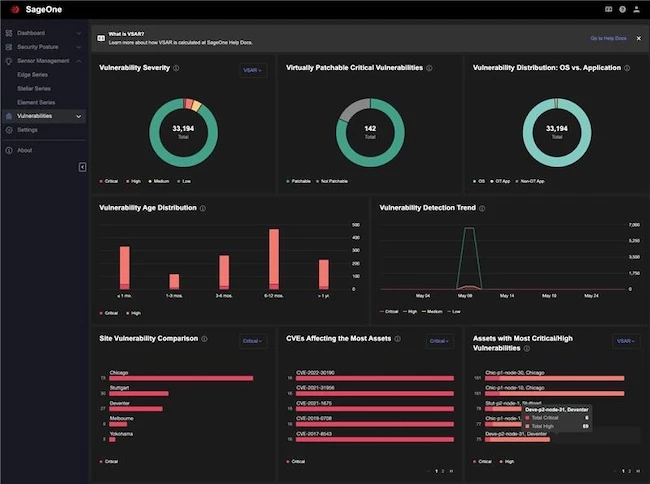
TXOne Networks announced an expanded new version of its SageOne OT Cybersecurity Governance Platform. Already relied upon by many industrial…
Small and medium-sized enterprises (SMEs) employ a staggering number of people in the UK, and are especially vulnerable to cyber…
$500m from UAE’s Castle Investments Demonstrates worldwide AI growth Data centres could empower startups Turkey’s data centre industry is experiencing…
Threat actors have been found exploiting the ubiquitous “Prove You Are Human” verification systems to distribute malicious software. Specifically, this…
TXOne Networks announced an expanded new version of its SageOne OT Cybersecurity Governance Platform. Already relied upon by many industrial…
One of the most significant conundrums faced by any organisation that plans a cloud migration is that there are many…
An analysis conducted recently by researchers at cybersecurity firm Forescout showed that roughly 35,000 solar power systems are exposed to…
Cartier disclosed a data breach following a cyber attack Pierluigi Paganini June 04, 2025 Luxury-goods conglomerate Cartier disclosed a data…
Researchers have unearthed a sophisticated supply chain attack targeting Ruby Gems, a popular package manager for the Ruby programming language….
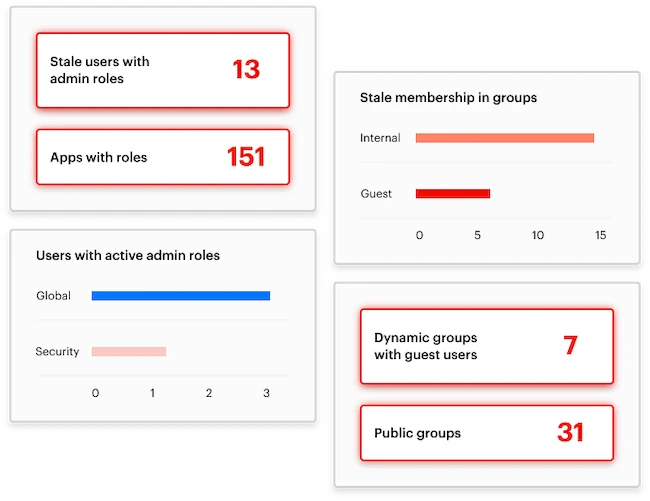
Varonis announced Varonis Identity Protection, the latest enhancement to its Data Security Platform that gives organizations visibility and control of…