Browse by Chapters Click on the tiles below to navigate the practical realities of the cloud ecosystem. Cloud Covered Champion…
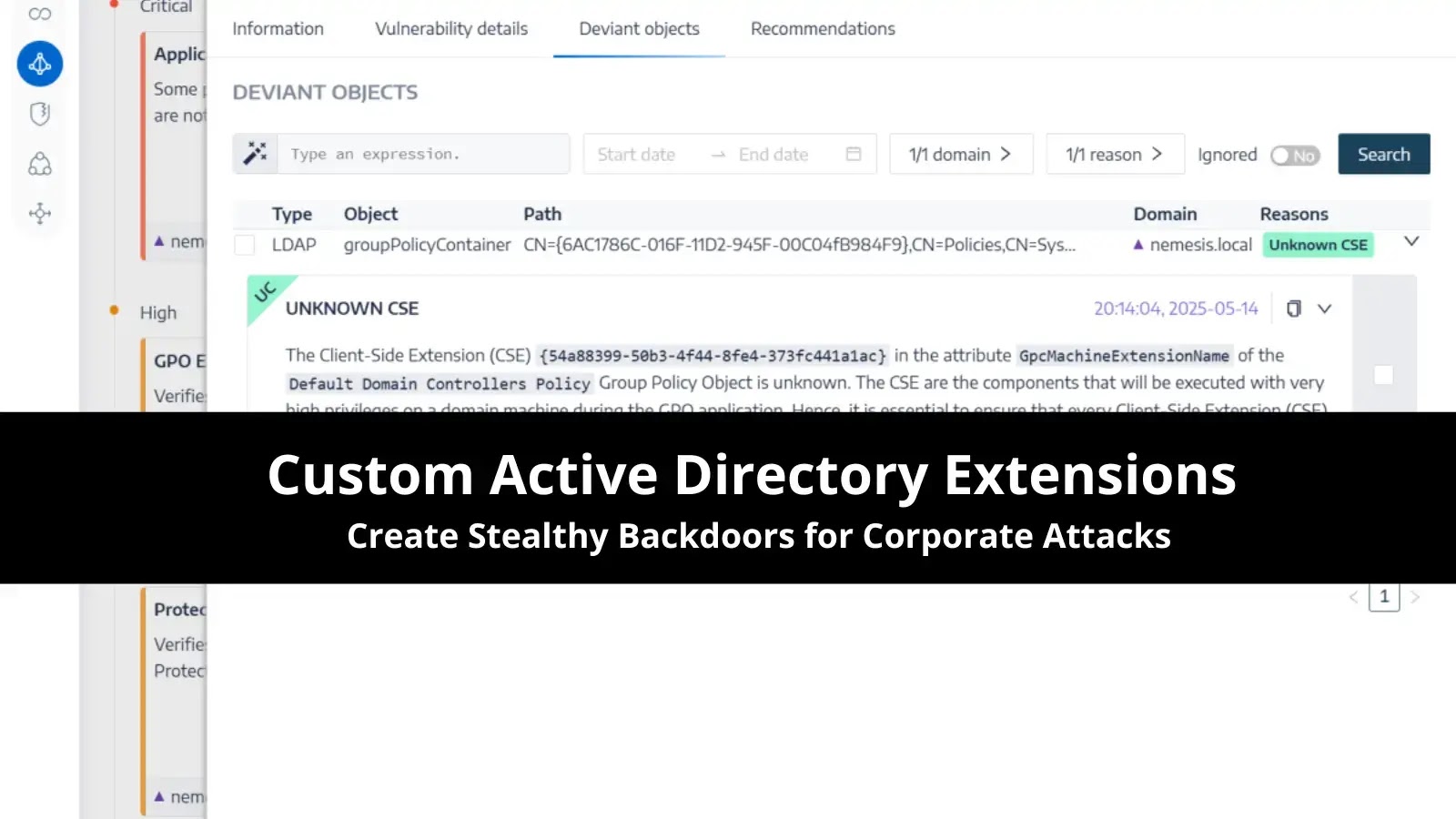
Active Directory (AD) Group Policy Objects (GPOs) are a cornerstone of centralized management for Windows environments, enabling administrators to configure…
Browse by Chapters Click on the tiles below to navigate the practical realities of the cloud ecosystem. Cloud Covered Champion…
Since 2016, the “DollyWay World Domination” campaign has quietly compromised more than 20,000 WordPress websites worldwide, exploiting vulnerabilities in plugins…
According to research, 62% of organizations said their attack surface grew over the past year. It’s no coincidence that 76%…
Decentralized identity (DID) is gaining traction, and for CISOs, it’s becoming a part of long-term planning around data protection, privacy,…
Jun 04, 2025The Hacker NewsVulnerability / DevOps Hewlett Packard Enterprise (HPE) has released security updates to address as many as…
In this Help Net Security interview, Thomas Squeo, CTO for the Americas at Thoughtworks, discusses why traditional security architectures often…
Email security startup Trustifi on Tuesday announced raising $25 million in a Series A funding round led by Camber Partners,…
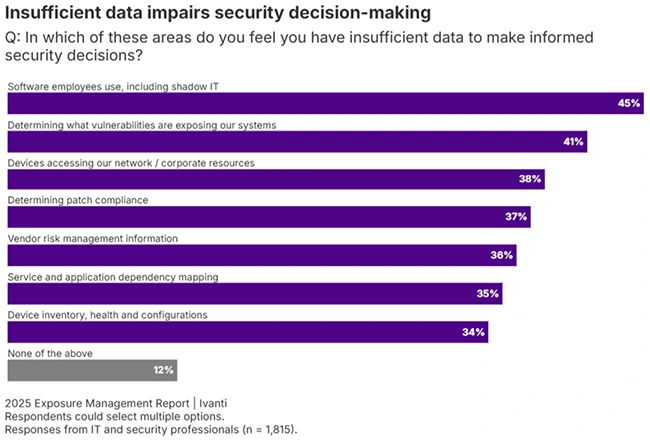
Many organizations are overwhelmed by the complexity of their IT systems, making it difficult to manage cybersecurity risks, according to…
Victoria Police has upgraded its online reporting function for non-emergency crimes as its seven-year contract with provider Serco reaches expiry….
A comprehensive new study has exposed significant vulnerabilities and inconsistencies in the security mechanisms protecting major cloud-based large language model…