Aembit, the workload identity and access management (IAM) company, today announced a major expansion of its platform to support Microsoft…
Silver Spring, Maryland, June 3rd, 2025, CyberNewsWire Aembit, the workload identity and access management (IAM) company, today announced a major…
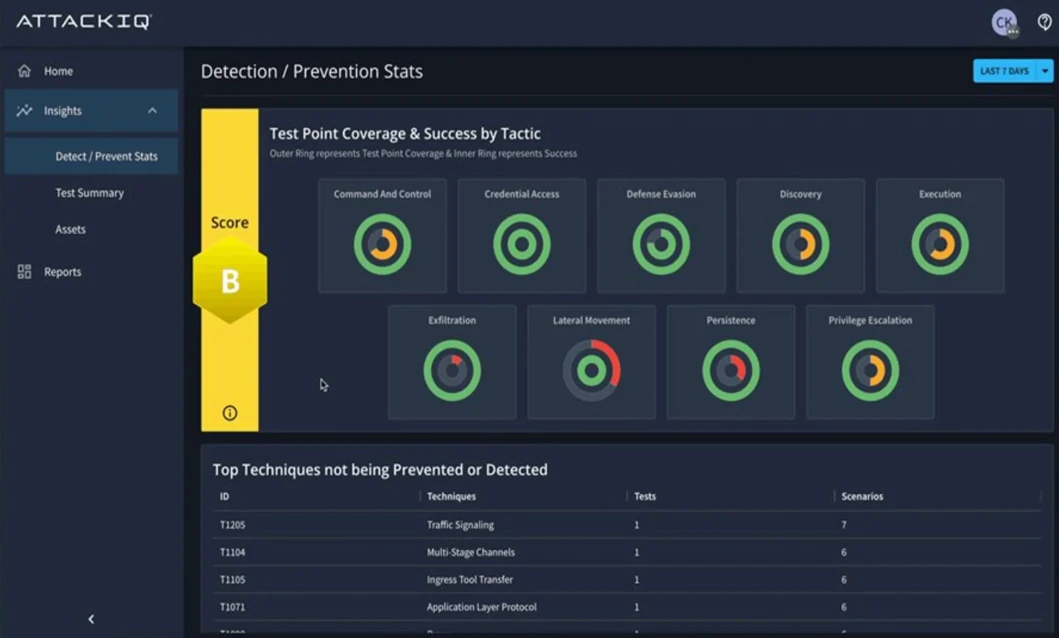
AttackIQ releaseed AttackIQ Ready3. With expanded discovery capabilities, Ready3 maps both internal and external attack surfaces. By correlating asset discovery…
As generative AI (GenAI) tools become embedded in the fabric of enterprise operations, they bring transformative promise, but also considerable…
Over 1,000 industrial monitoring devices made by Canada-based Instantel may be exposed to remote hacking due to a critical vulnerability….
Fashion retail giant Victoria’s Secret has delayed its first quarter 2025 earnings release because of ongoing corporate system restoration efforts…
A high-severity vulnerability was uncovered in Splunk Universal Forwarder for Windows that compromises directory access controls. The flaw, designated CVE-2025-20298…
A severe vulnerability in Apple’s iOS activation infrastructure has been uncovered, posing a significant risk to device security during the…
There are an estimated 3.5 million unfilled cybersecurity roles worldwide as of 2025. That figure has remained steady since 2021, according…
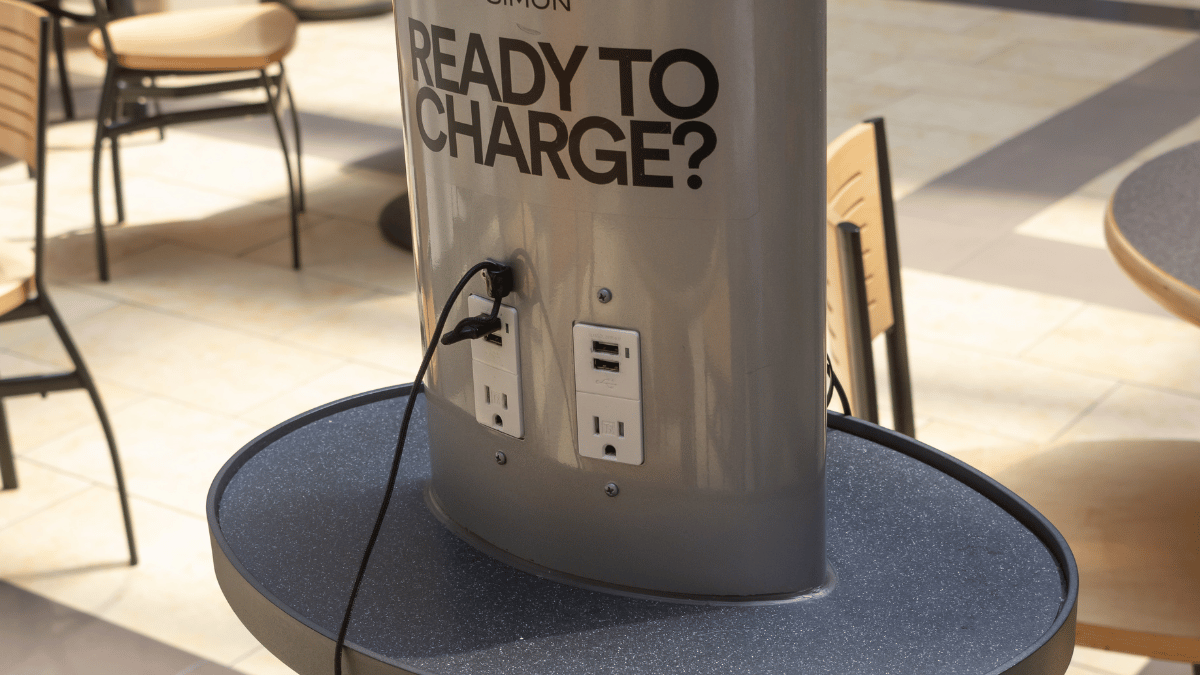
Remember juice jacking? It’s a term that crops up every couple of years to worry travelers. This spring has seen…
Microsegmentation firm Zero Networks today announced raising $55 million in Series C funding, which brings the total raised by the…
A new cross-site scripting (XSS) vulnerability in Safari that exploits the browser’s TypeError exception handling mechanism to execute arbitrary JavaScript…