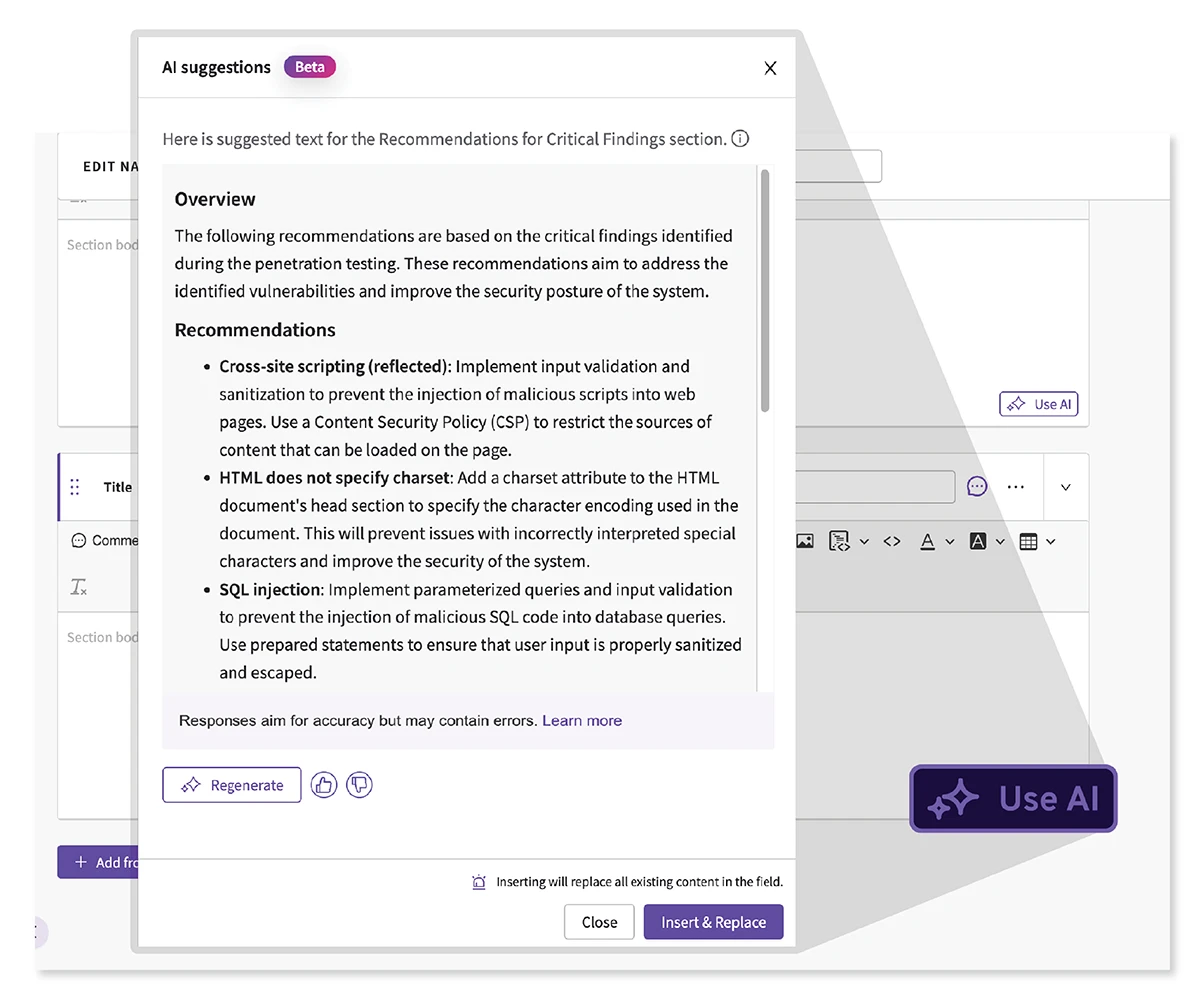
The threat landscape is evolving faster than ever. Staying ahead means going beyond automated scans and check-the-box assessments. It demands…
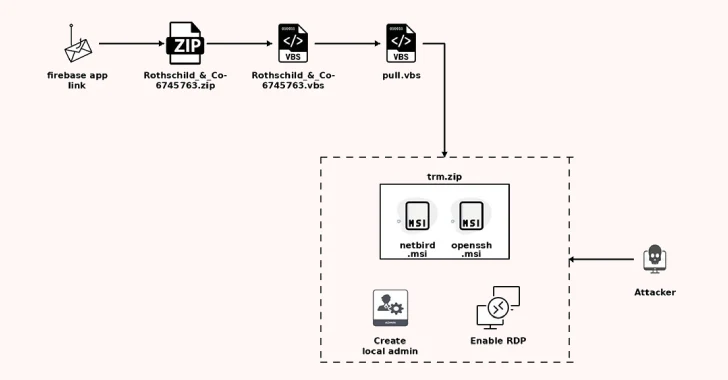
Cybersecurity researchers have warned of a new spear-phishing campaign that uses a legitimate remote access tool called Netbird to target…
Companies across industries are discovering that well-executed risk assessments do far more than check regulatory boxes—they’re becoming powerful engines for…
In this Help Net Security interview, Aaron McCray, Field CISO at CDW, discusses how AI is transforming the CISO role…
Taipei, Taiwan – May 22, 2025 – Synology is showcasing its latest lineup of innovations at COMPUTEX 2025, presenting a…
As cybercrime costs the global economy an estimated $445 billion annually, blockchain technology is emerging as a powerful cybersecurity weapon…
We are very pleased to announce the Best Paper Awards from the Journal of Cyber Security and Mobility! The Journal…
If you’ve spent any time in penetration testing, chances are you’ve crossed paths with Metasploit. The second edition of Metasploit…
The cybersecurity landscape witnessed an unprecedented escalation in distributed denial of service (DDoS) attacks during the first quarter of 2025….
32% of security professionals think they can deliver zero-vulnerability software despite rising threats and compliance regulations, according to Lineaje. Meanwhile,…
Two critical local information-disclosure vulnerabilities affecting millions of Linux systems worldwide, potentially allowing attackers to extract sensitive password data through…
A growing crisis is emerging in corporate cybersecurity operations, where organizational silos between IT and security teams are creating dangerous…