In an era where cybercriminals are becoming increasingly sophisticated, waiting for security alerts to sound the alarm is no longer…
As cybersecurity threats intensify and regulatory scrutiny increases, Chief Information Security Officers (CISOs) face mounting pressure to communicate complex technical…
Supply chain cyberattacks have exploded by a staggering 431% between 2021 and 2023, transforming what was once a manageable risk…
As cybersecurity threats continue to escalate, organizations worldwide are turning to automated patch management solutions to combat an alarming statistic:…
By default AI will magnify gaps between good and bad students June 1, 2025 I’ve got a one-liner for what…
I have two groups of very smart cybersecurity friends, and they see AI completely differently. The first group thinks AI…
As cybersecurity threats intensify across global markets, organizations grapple with a stark reality: data breach costs have reached unprecedented levels…
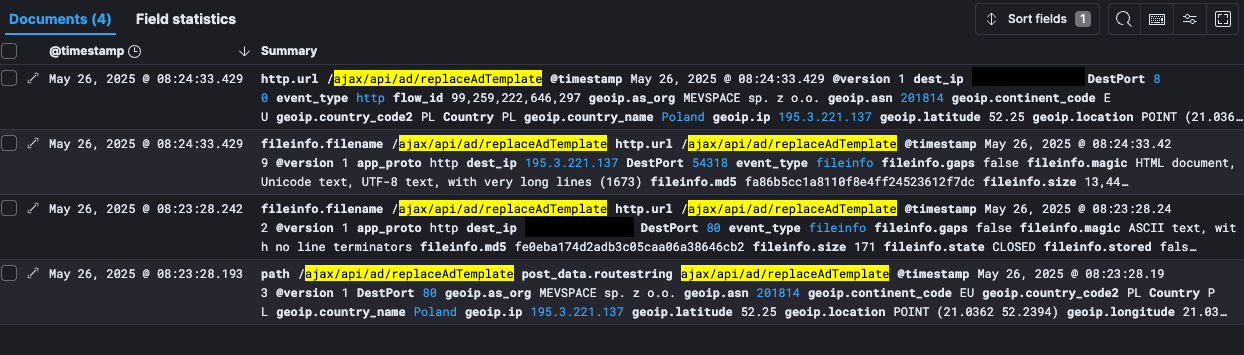
Two flaws in vBulletin forum software are under attack Pierluigi Paganini June 01, 2025 Experts found two vulnerabilities in the…
The cybersecurity landscape has reached a pivotal moment where Chief Information Security Officers (CISOs) are fundamentally reshaping their approach to…
The cybersecurity industry is fundamentally transforming as organizations shift from traditional endpoint protection to advanced threat detection with Endpoint Security…
Organizations worldwide grapple with an unprecedented challenge: achieving continuous compliance in threat environments while defending against rapidly evolving cyber risks….
Organizations worldwide are grappling with an unprecedented escalation in insider threats. The latest research reveals that companies now spend an…