Hello, security enthusiasts! Today, we’re diving into the exciting new features of OWASP Noir v0.18, particularly focusing on the PassiveScan…
Data Subject Access Requests (DSARs) have emerged as a critical compliance challenge for businesses worldwide as privacy regulations continue to…
Keeper Security has unveiled an update to its password management platform: Keeper’s upgraded One-Time Share. The new feature enables bidirectional,…
Cybersecurity firm Quorum Cyber has uncovered two new versions of malicious software known as NodeSnake. This discovery highlights a possible…
May 31, 2025Ravie LakshmananVulnerability / Linux Two information disclosure flaws have been identified in apport and systemd-coredump, the core dump…
Two Linux flaws can lead to the disclosure of sensitive data Pierluigi Paganini May 31, 2025 Qualys warns of two…
2025년 시작과 함께 ZAP 2.16이 릴리즈되었습니다 이번 업데이트는 기능적으로 추가된 부분들이 있어서 대표적인 기능 3가지 위주로 정리하면서 리뷰할까 합니다. Client…
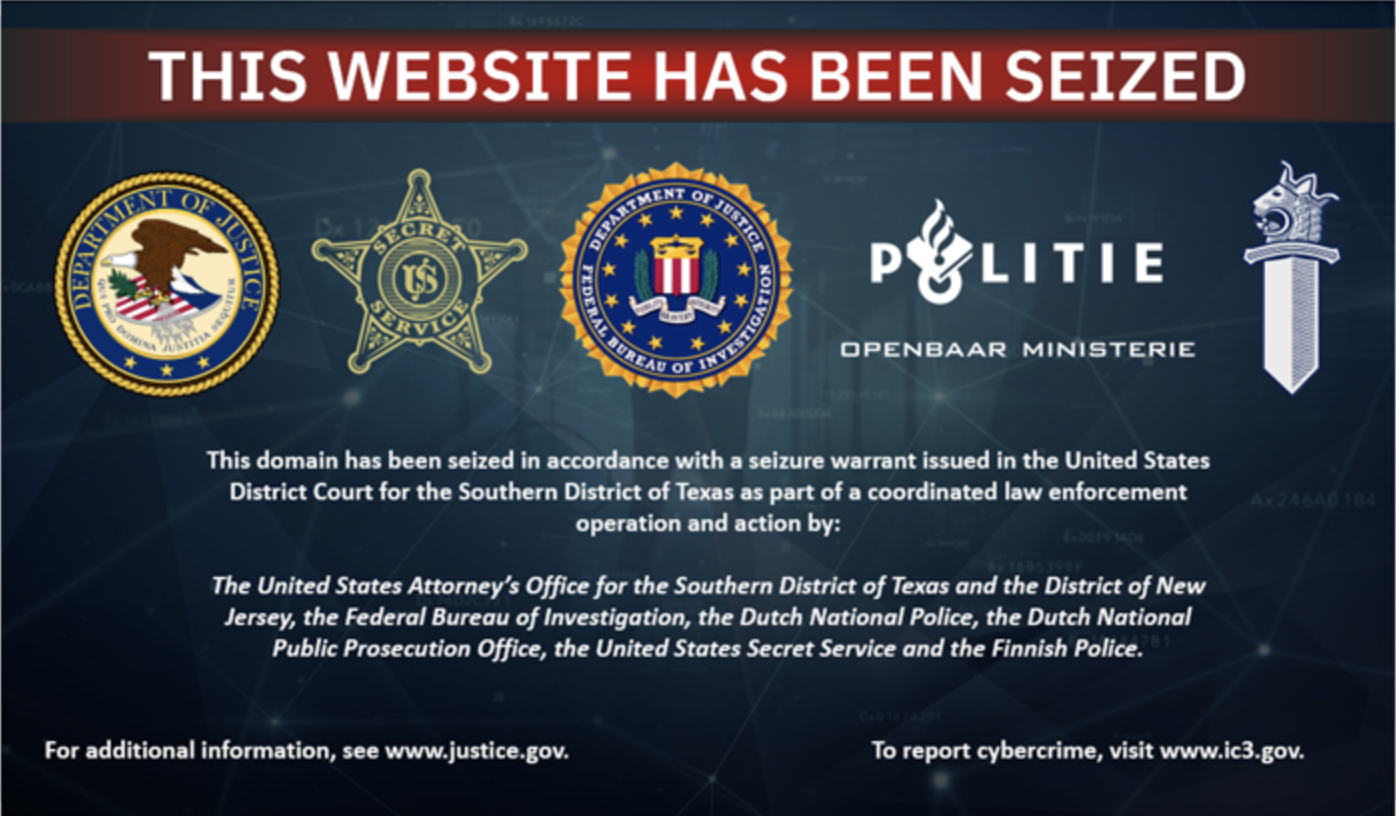
AVCheck, a large-scale service that cybercriminals use to check if their malware can be detected by various antivirus tools, was…
Cybercriminals have escalated their tactics by exploiting Google Apps Script, a trusted development platform, to host sophisticated phishing campaigns that…
Meta stopped covert operations from Iran, China, and Romania spreading propaganda Pierluigi Paganini May 30, 2025 Meta stopped three covert…
Enhancing Security Testing with AI Integration (LLM) Noir v0.19.0 introduces an exciting feature by integrating AI, specifically Large Language Models…
A recent Windows 11 security update, KB5058405, released on May 13, 2025, has caused significant boot failures for some users…