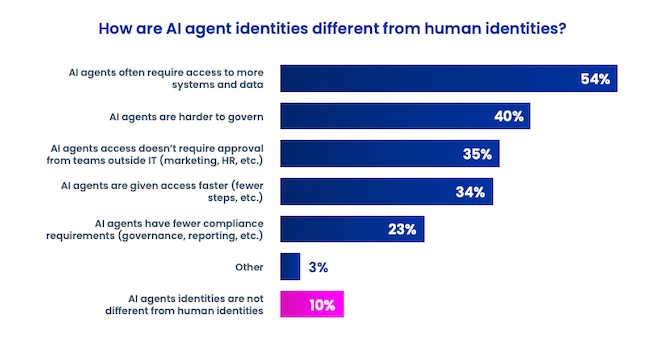
82% of organizations already use AI agents, but only 44% of organizations report having policies in place to secure them,…
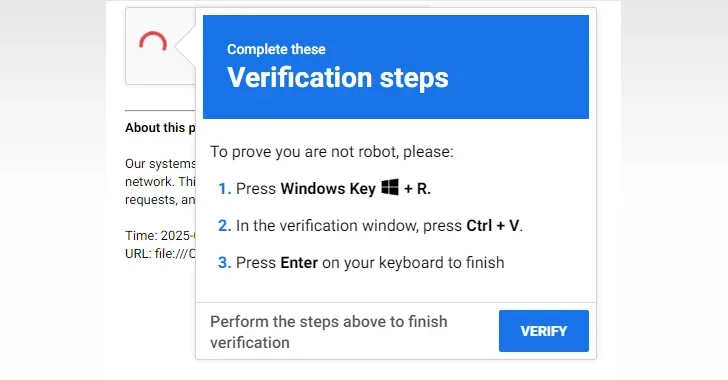
A new malware campaign is distributing a novel Rust-based information stealer dubbed EDDIESTEALER using the popular ClickFix social engineering tactic…
What does US retrenchment on Diversity, Equality and Inclusion, mean for tech companies in the UK, and could a similar…
Cybersecurity researchers are calling attention to two recently observed phishing campaigns caught abusing the legitimate services Firebase and Google Apps…
ConnectWise suffered a cyberattack carried out by a sophisticated nation state actor Pierluigi Paganini May 30, 2025 ConnectWise detected suspicious…
The Australian Academy of Technological Sciences and Engineering (ATSE) welcomed Melissa Price’s appointment as shadow minister for cybersecurity and the…
Today’s threat landscape, attack surfaces are expanding faster than most security teams can track. Every new cloud asset, exposed API,…
Companies want results fast, and low/no-code (LCNC) and Vibe Coding platforms promise just that: rapid application development with either no…
Pure Crypter, a well-known malware-as-a-service (MaaS) loader, has been recognized as a crucial tool for threat actors targeting Windows-based systems…
A newly emerged threat actor, going by the alias “Often9,” has posted on a prominent cybercrime and database trading forum,…
To understand the magnitude of the modern cybersecurity threat, it’s instructive to think of the global cybercrime industry as a…
Phishing scams used to be filled with awkward wording and obvious grammar mistakes. Not anymore. AI is now making it…