May 30, 2025Ravie LakshmananVulnerability / Threat Intelligence The China-linked threat actor behind the recent in-the-wild exploitation of a critical security…
With millions of businesses now using Amazon Web Services (AWS) for their cloud computing needs, it’s become a vital consideration…
A newly disclosed vulnerability, tracked as CVE-2025-27522, has been discovered in Apache InLong, a widely used real-time data streaming platform….
Chinese state-sponsored threat actor APT41 has targeted government entities with malware that uses Google Calendar for command-and-control (C&C), Google warns….
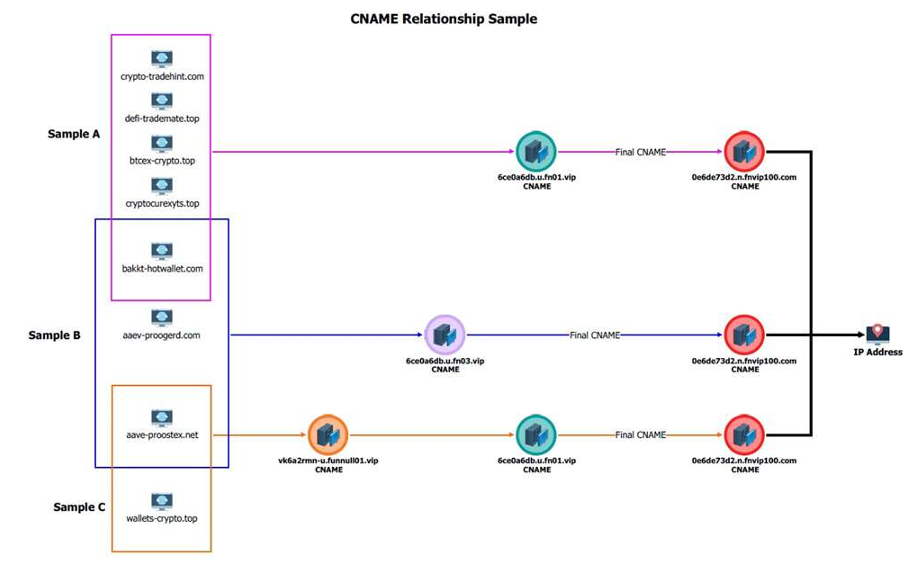
US Treasury sanctioned the firm Funnull Technology as major cyber scam facilitator Pierluigi Paganini May 30, 2025 The U.S. sanctioned…
Amelia Coen | 30 May 2025 at 09:38 UTC We’re proud to announce that PortSwigger has been awarded the prestigious…
This weekend, Microsoft will start turning off password management functionality in its Authenticator app. If you use the app, from…
Threat actors linked to lesser-known ransomware and malware projects now use AI tools as lures to infect unsuspecting victims with…
Image: Shutterstock, ArtHead. The U.S. government today imposed economic sanctions on Funnull Technology Inc., a Philippines-based company that provides computer…
Several cybersecurity researchers who have tracked Trickbot extensively tell WIRED they were unaware of the announcement. An anonymous account on…
A critical vulnerability (CVE-2025-48057) has been discovered in Icinga 2, the widely used open-source monitoring platform. The flaw, affecting installations…
CrowdStrike and Australia’s Academic and Research Network (AARNet) today announced an expanded partnership to deliver CrowdStrike Falcon Complete Next-Gen MDR…