It’s easy to drown in a sea of data where every vulnerability or misconfiguration is deemed important. If everything is…
Microsoft has confirmed that some Windows 11 systems might fail to start after installing the KB5058405 cumulative update released during…
A sophisticated malware campaign designated UTG-Q-015 has emerged as a significant threat to government infrastructure, targeting web servers through coordinated…
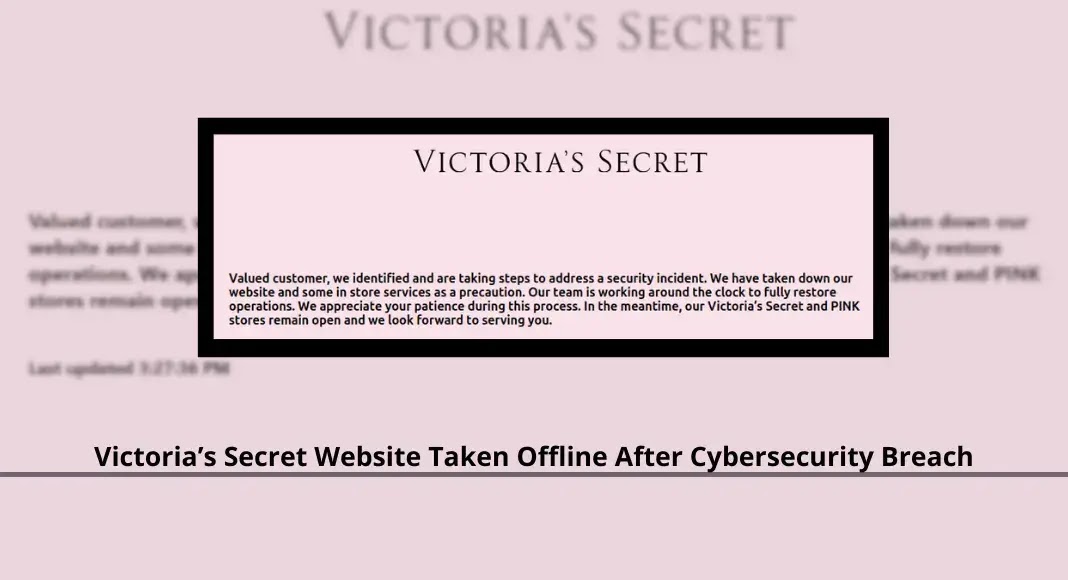
Victoria’s Secret, the iconic lingerie retailer, has taken its US website offline and suspended some in-store services following a major…
Having just returned from the RSA Conference 2025, without a doubt the word on everyone’s lips and the dominant theme…
Andrzej Matykiewicz | 29 May 2025 at 09:29 UTC We recently hosted a webinar to introduce Burp Suite DAST, the…
Recent cybersecurity research has revealed sophisticated patterns within TCP SYN segments that cybercriminals are exploiting to establish covert communication channels…
Trellix’s email security systems detected a highly targeted spear-phishing campaign aimed at CFOs and finance executives across industries like banking,…
During the earnings call for its latest financial results, Nvidia revealed it has taken “a multibillion-dollar write-off” due to US…
Data broker giant LexisNexis Risk Solutions, a Georgia-based American data analytics company, has revealed that attackers stole the personal information…
In 2025, the exploitation of supply chain vulnerabilities by Advanced Persistent Threats (APTs) has emerged as one of the most…
Operant AI has announced the release of Woodpecker, an open-source automated red teaming engine designed to make advanced security testing…