The UK’s patchwork approach to regulating biometric surveillance technologies is “inadequate”, placing fundamental rights at risk and ultimately undermining public…
Microsoft has released the KB5058499 preview cumulative update for Windows 11 24H2 with forty-eight new features or changes, with many gradually rolling…
The European Union has said it stands in solidarity with the Czech Republic after the country identified China as being…
Multiple attackers are raiding Ivanti customers’ systems again by exploiting a pair of closely intertwined vulnerabilities in Ivanti Endpoint Manager…
Mandiant Threat Defense has uncovered a malicious campaign orchestrated by the threat group UNC6032, which capitalizes on the global fascination…
The City of Sydney’s has “reinvigorated” its SAP SuccessFactors deployment, helping it drive a more personalised approach to its staff…
Zscaler Inc. announced on May 27, 2025, a definitive agreement to acquire Red Canary, a leading Managed Detection and Response…
Citrix has issued a high-severity security bulletin addressing multiple vulnerabilities—CVE-2025-27462, CVE-2025-27463, and CVE-2025-27464—affecting XenServer VM Tools for Windows. These vulnerabilities…
Cybersecurity researchers at BeyondTrust are warning about a little-known but dangerous issue within Microsoft’s Entra identity platform. The issue isn’t…
Westpac is piloting AI to help its scam and fraud support team process and analyse the information a customer is…
Dive Brief: A “highly targeted” spearphishing campaign is attempting to ensnare financial executives at banks, investment firms, energy utilities and…
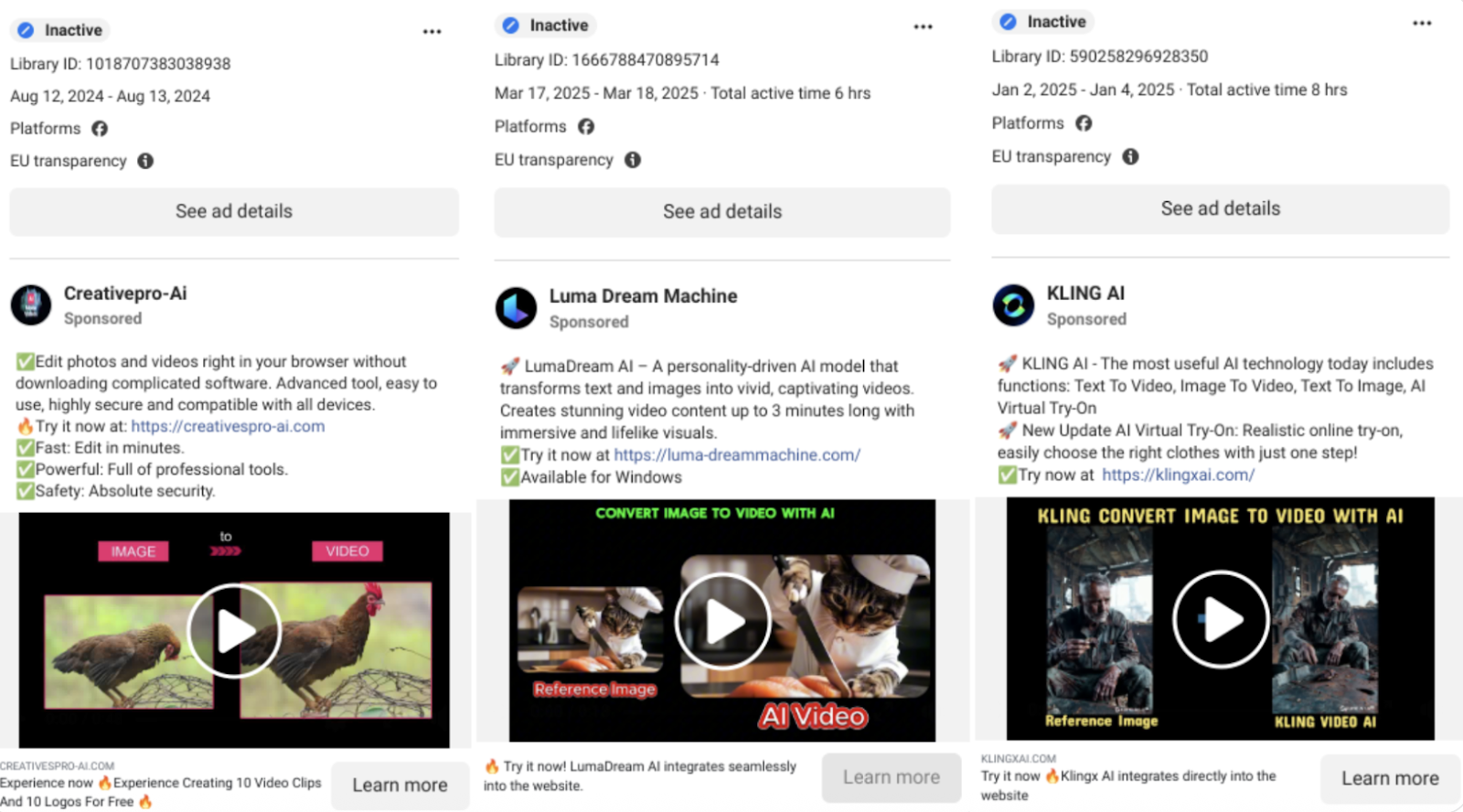
As the internet fills up with clips from AI-video generators, hacking groups are seeding the online landscape with malware-laced programs…