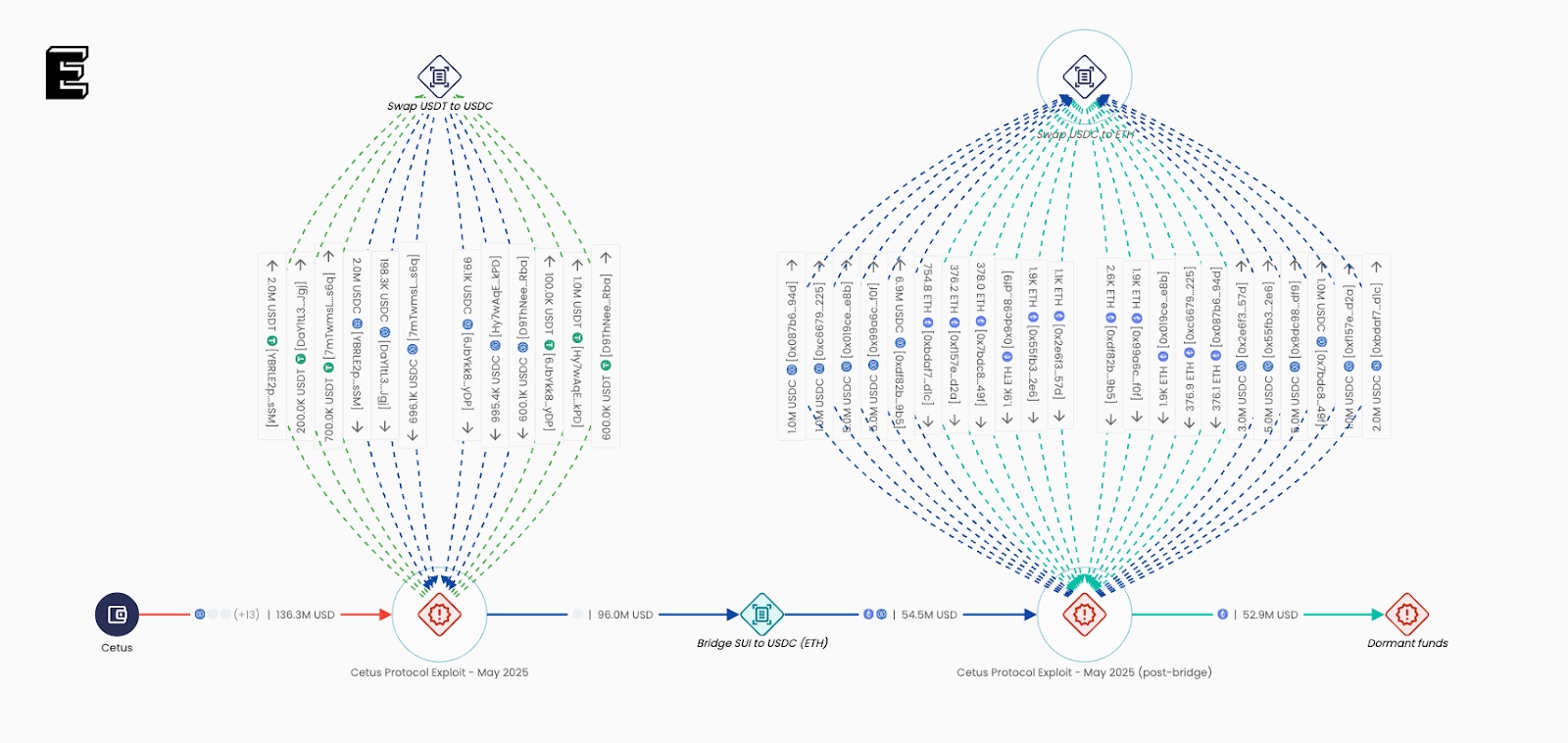
Crooks stole over $200 million from crypto exchange Cetus Protocol Pierluigi Paganini May 27, 2025 Cetus Protocol reported a $223…
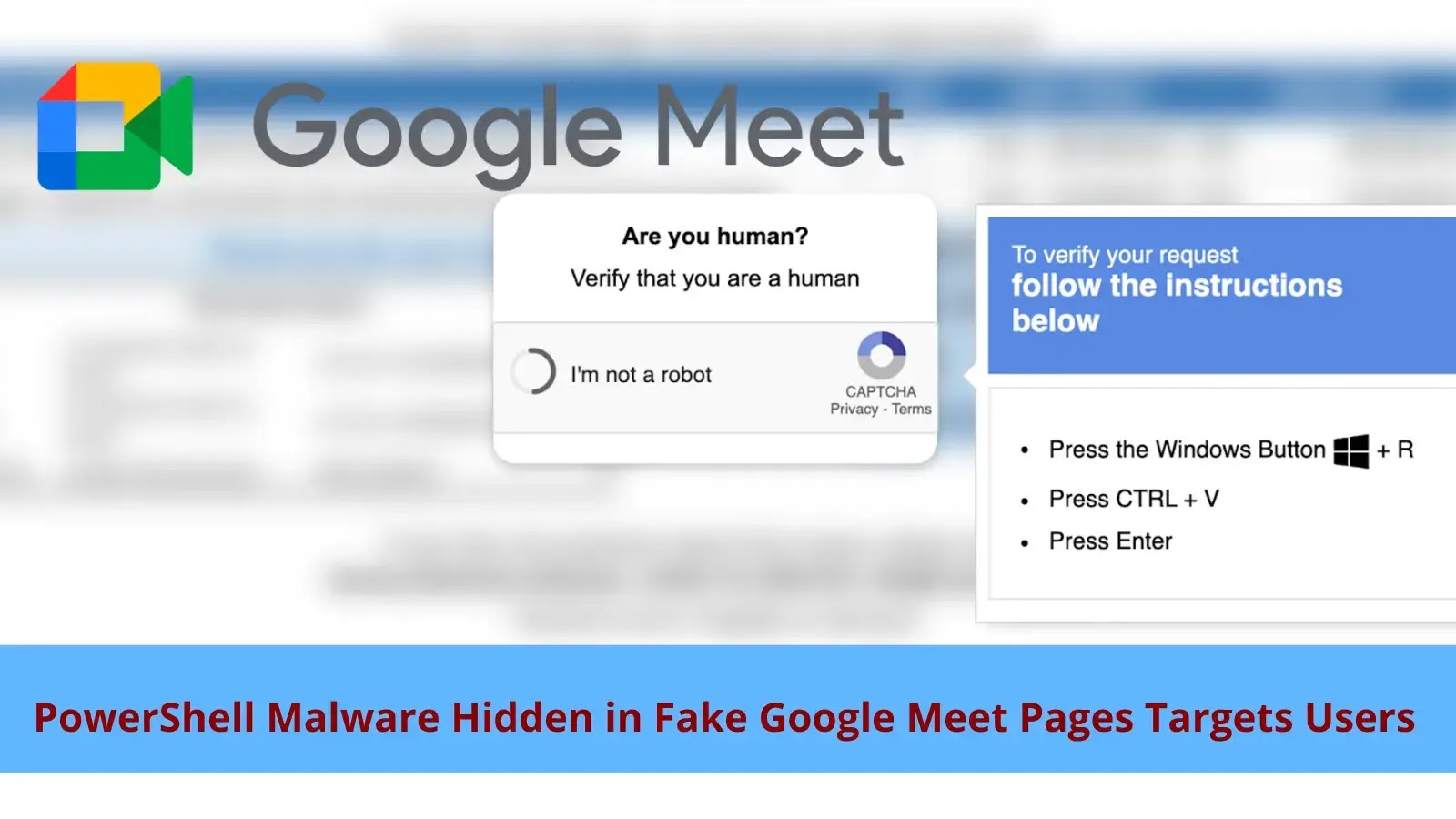
A new wave of cyberattacks exploits user trust in Google Meet by deploying meticulously crafted fake meeting pages that trick…
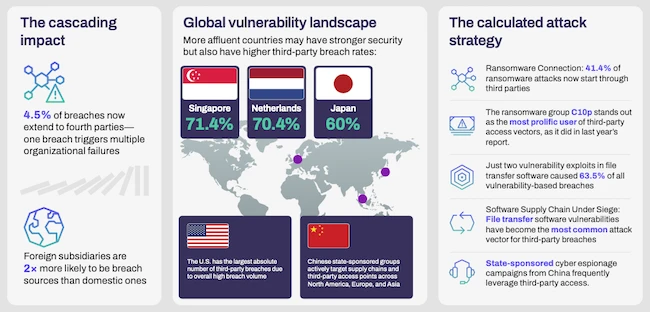
Security teams can no longer afford to treat third-party security as a compliance checkbox, according to SecurityScorecard. Traditional vendor risk…
In this Help Net Security interview, Michael Metzler, Vice President Horizontal Management Cybersecurity for Digital Industries at Siemens, discusses the…
Is the remote IT worker you recently hired really who he says he is? Fake IT workers are slipping into…
Application Security Engineer, SDO AppSec Amazon | EMEA | Hybrid – View job details As an Application Security Engineer, SDO…
Cybersecurity experts have noted an increase in data breaches where threat actors are directly querying internal databases to steal sensitive…
Katz Stealer has emerged as a potent credential-stealing malware-as-a-service, targeting popular web browsers such as Chrome, Edge, Brave, and Firefox….
Services Australia is wary of how external AI tools are consuming and referencing its information, with targeted adjustments being made…
Threat actors have been exploiting the trust in India’s digital public infrastructure by setting up a deceptive phishing site, digiyatra[.]in,…
The Australian Army is trialling technology that generates fake radio communications in order to mislead adversaries and protect frontline personnel….
The Federal Bureau of Investigation (FBI) has issued a critical alert regarding the escalating activities of the cyber threat actor…