Hello Hackers Spring is in the air, and so is the sweet scent of freshly reported bugs. Intigriti’s blooming too—each…
The Russia-aligned threat actor TAG-110, also linked to UAC-0063 and APT28 (BlueDelta) with medium confidence by CERT-UA, has shifted tactics…
From zero-day exploits to large-scale bot attacks — the demand for a powerful, self-hosted, and user-friendly web application security solution…
The ongoing exploitation of a Commvault vulnerability that was targeted as a zero-day is likely part of a broader campaign…
Cybercriminals are using TikTok videos to trick users into infecting themselves with Vidar and StealC information-stealing malware in ClickFix attacks….
A severe authentication bypass vulnerability (CVE-2025-4978) has been uncovered in NETGEAR’s DGND3700v2 wireless routers, enabling unauthenticated attackers to gain full…
Cloudflare has alerted users of a security vulnerability—tracked as CVE-2025-4366—in the widely used Pingora OSS framework. This vulnerability, a request…
A China-linked threat actor exploited a Trimble Cityworks zero-day vulnerability in attacks against local government entities in the US, Cisco…
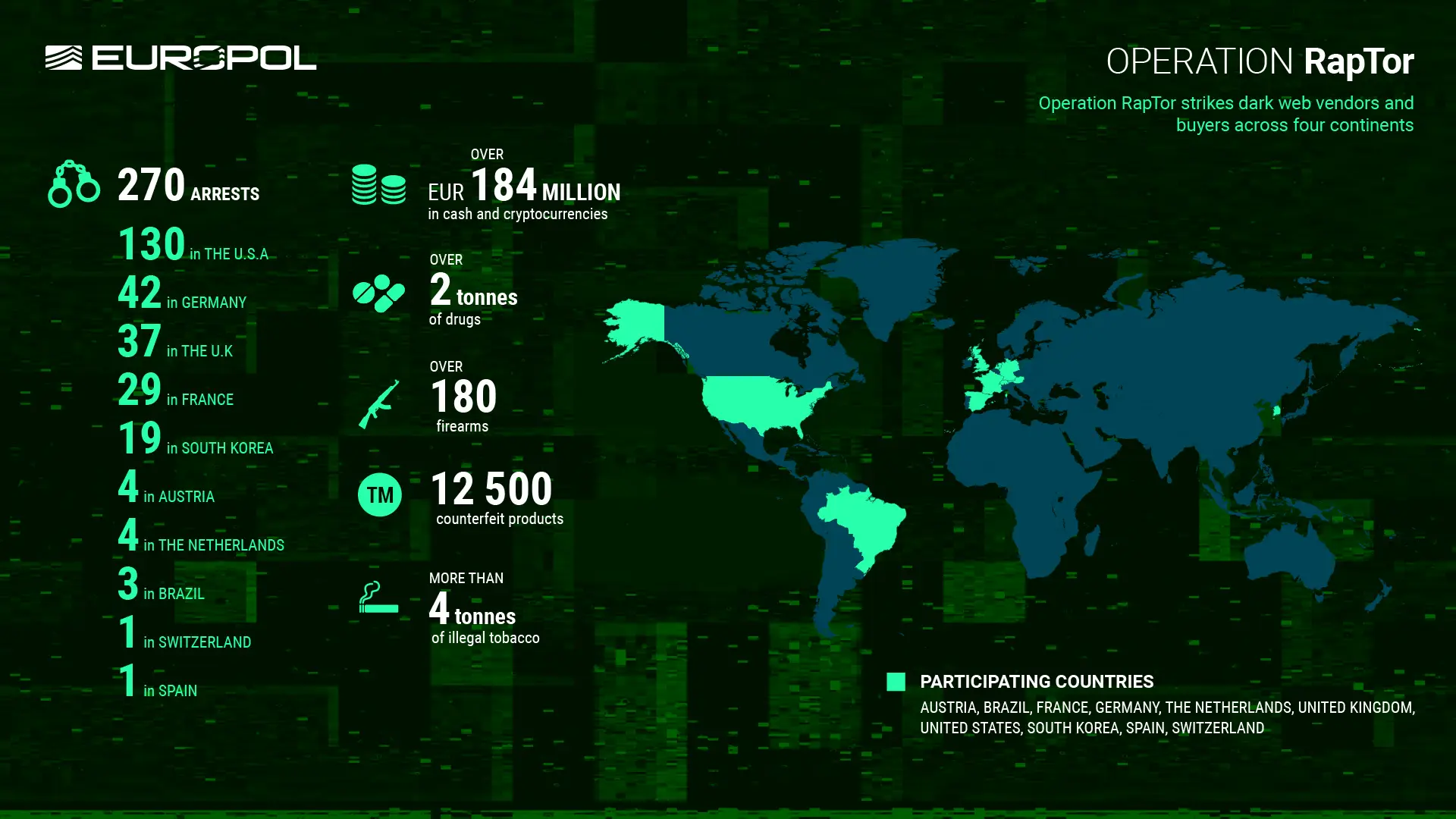
Operation RapTor led to the arrest of 270 dark web vendors and buyers Pierluigi Paganini May 23, 2025 Law enforcement…
Operation Endgame II has delivered a devastating strike against DanaBot, a notorious malware that has plagued systems since its emergence…
In an international law enforcement operation, 270 individuals involved in dark web criminal activity have been arrested across ten countries….
The notorious DanaBot botnet has been severely disrupted as part of an international law enforcement operation, which also involved charges…