Anthropic is secretly working on new models called Claude Sonnet 4 and Opus 4, which are believed to be the company’s…
Microsoft’s Digital Crimes Unit (DCU) has filed a legal action against Lumma Stealer, after it found nearly 400,000 Windows computers…
ChatGPT’s Operator, which is still in research preview, will soon become a “very useful tool,” according to Jerry Tworek, VP…
OpenAI is buying Jony Ive’s startup io Products in a US$6.5 billion ($10 billion) deal and will bring the chief…
A cyberattack was responsible for the week-long outage affecting Cellcom wireless network Pierluigi Paganini May 21, 2025 Cellcom, a regional…
In today’s digital workplaces, more employees are building their own applications by generating code using Low Code No Code (LCNC),…
Marks & Spencer said hackers broke into its systems by tricking employees at a third-party contractor, skirting its digital defences…
An appeals court on Wednesday rejected a bid by the widow of murdered Washington Post journalist Jamal Khashoggi to revive…
A Russian state-sponsored cyberespionage campaign attributed to APT28 (Fancy Bear/Forest Blizzard) hackers has been targeting and compromising international organizations since…
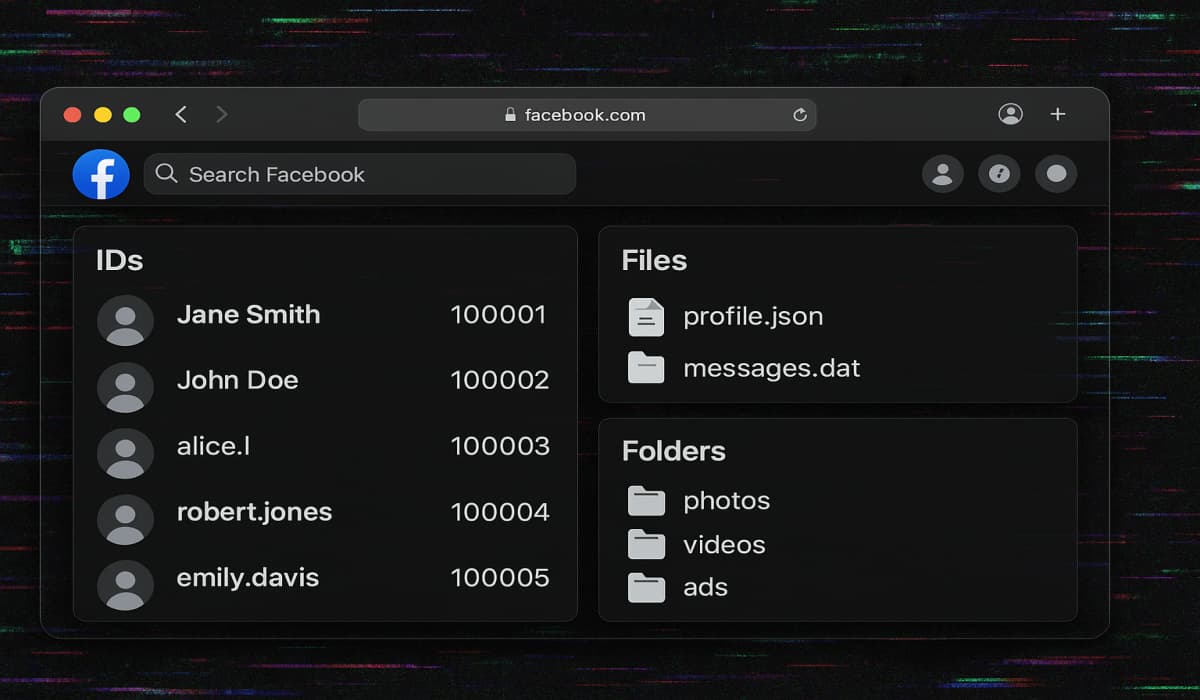
A threat actor using the alias “ByteBreaker” is claiming to have abused the Facebook API and scraped 1.2 billion account…
BHP is taking the next step in an enterprise-wide AI transformation, creating new practice lead roles to architect and scale…
The US government’s cybersecurity agency CISA is sounding the alarm over what it calls an “elevated threat” from Russia’s military-intelligence…