Patching vulnerabilities is one of the most basic principles of cybersecurity — and one of the hardest to execute consistently…
Massachusetts college student stands accused of orchestrating a sweeping cyberattack on PowerSchool, a widely used educational software provider, resulting in…
Fujitsu was paid £80m by HM Revenue & Customs (HMRC) in March alone as its public sector business continues unabated,…
Update 5/20/25 4:40 PM EST: In response to our questions about the attack, Dell states that the malicious RVTools installer was not…
IBM X-Force’s 2024 cybersecurity report, nearly one-third of cyber intrusions now rely on identity-based attacks, exploiting valid login credentials to…
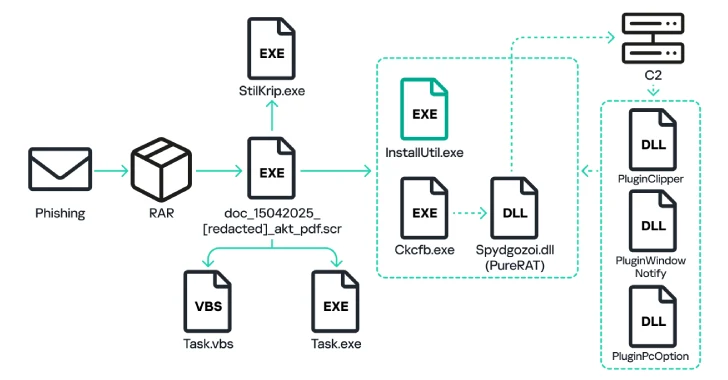
May 21, 2025Ravie LakshmananMalware / Windows Security Russian organizations have become the target of a phishing campaign that distributes malware…
Earlier this month the House of Lords had its first debate on the Public Authorities (Fraud, Error and Recovery) Bill. …
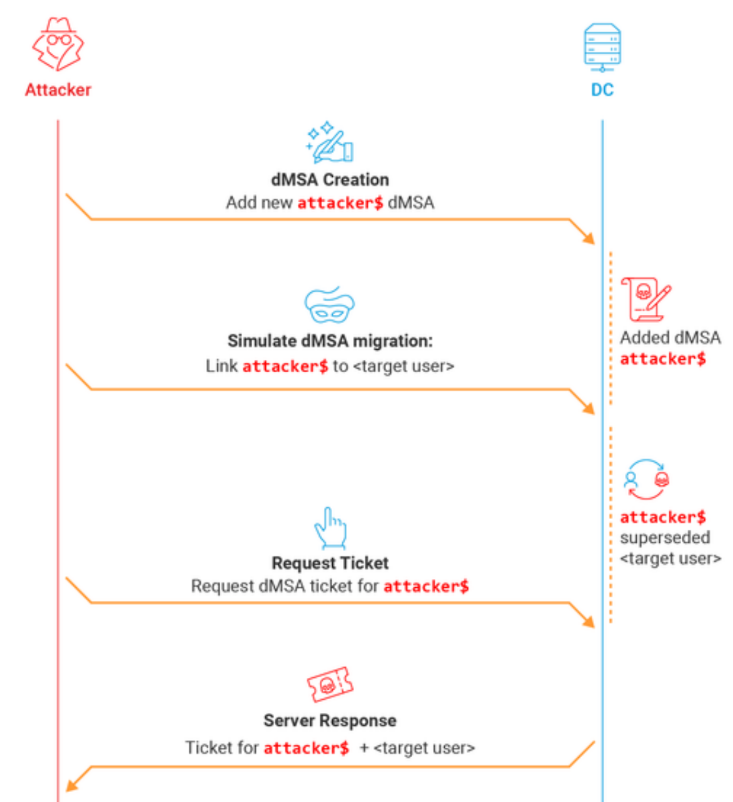
The delegated Managed Service Account (dMSA) feature was introduced in Windows Server 2025 as a secure replacement for legacy service…
When Coinbase said last week that it had refused to pay a $20 million ransom tied to an insider leak,…
Coinbase data breach impacted 69,461 individuals Pierluigi Paganini May 21, 2025 Cryptocurrency exchange Coinbase announced that the recent data breach…
The European Union has imposed strict sanctions against web-hosting provider Stark Industries and the two individuals running it, CEO Iurie…
The cybersecurity landscape reveal that the VanHelsing ransomware operation has experienced a significant security breach with its source code being…