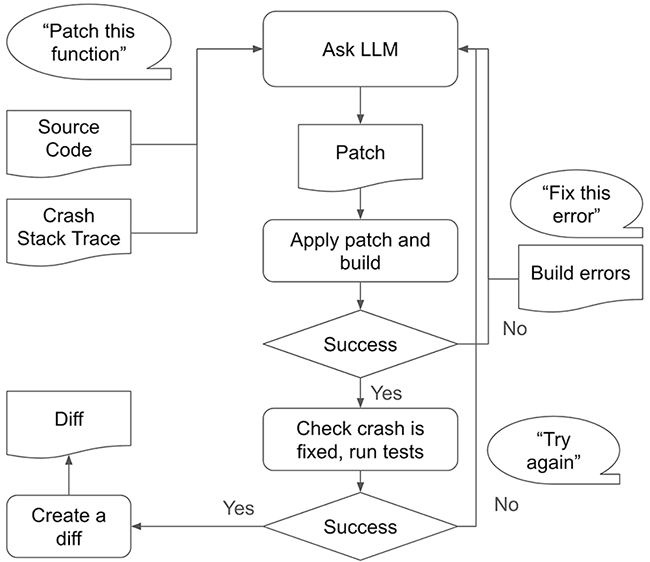
It sounds like an exercise in theory: what if a researcher could prompt an AI to reverse-engineer a vulnerability, locate…
In this Help Net Security interview, Anuj Goel, CEO of Cyware, discusses how threat intelligence is no longer a nice…
SK Telecom revealed that malware breach began in 2022 Pierluigi Paganini May 21, 2025 South Korean mobile network operator SK…
AI is truly making its way into every aspect of business operations, and rightly so. When we proactively test systems…
Database expert Dominik Tomicevic highlights the limitations of traditional cybersecurity defense methods and why knowledge graphs could be a better…
AutoPatchBench is a new benchmark that tests how well AI tools can fix code bugs. It focuses on C and…
WatchGuard® Technologies, a provider of unified cybersecurity for managed service providers (MSPs), today announced a planned leadership transition. After a…
Russian APT groups intensified attacks against Ukraine and the EU, exploiting zero-day vulnerabilities and deploying wipers, according to ESET. Ukraine…
Cloud adoption continues to rise, and with it comes increased complexity. Organizations use multiple cloud platforms, creating challenges that traditional…
Described as revolutionary and disruptive, AI agents are the new cornerstone of innovation in 2025. But as with any technology…
When Radhika started her Bachelor of Data Engineering degree at UTS, she didn’t yet see herself working in cyber security….
The European Union Agency for Cybersecurity (ENISA) has unveiled the European Vulnerability Database (EUVD), a strategic move designed to enhance…