The cyber security team at Broadcom has acknowledged that during the Pwn2Own hacking contest in Berlin in March, there were…
Listen to the article 4 min This audio is auto-generated. Please let us know if you have feedback. Dive Brief:…
Service desk agents are here to help, and we all prefer to talk to an understanding person than a chatbot…
A new research report released today by Progressive International, Expose Accenture, and the Movement Research Unit uncovers the sprawling influence…
Infoblox reveals Hazy Hawk, a new threat exploiting abandoned cloud resources (S3, Azure) and DNS gaps since Dec 2023. Learn…
May 20, 2025Ravie LakshmananCredential Theft / Browser Security An unknown threat actor has been attributed to creating several malicious Chrome…
As the government hands the Post Office £400m in public funds to replace its controversial Horizon system, details emerge of…
The official website for the RVTools VMware management tool was taken offline in what appears to be a supply chain…
Apple’s Lockdown Mode offers an extreme security level for users who may be targeted by sophisticated cyberattacks. While most iPhone…
The More_Eggs malware, operated by the financially motivated Venom Spider group (also known as Golden Chickens), continues to exploit human…
The Irish government has unveiled a semiconductor strategy in alignment with the European Chip Act. Silicon island: A national semiconductor…
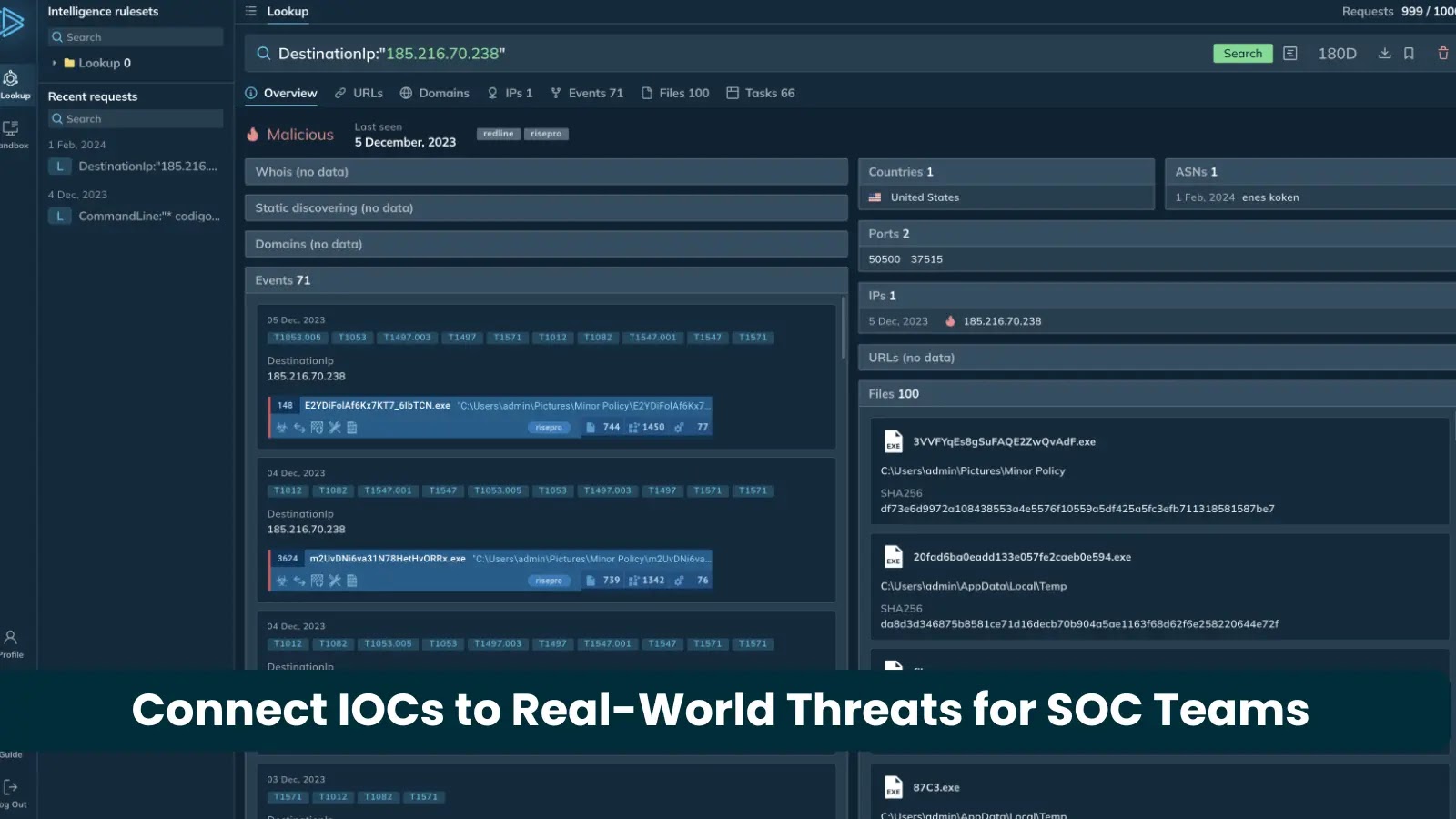
When it comes to cyber threats, data alone isn’t enough. Security Operations Center (SOC) teams are flooded with indicators of…