The Brussels Court of Appeal ruled on May 14, 2025, that the consent model used in tracking-based advertising by major…
“Alright. Now we’ve got a gun,” PSR says. “Just make sure you don’t point it at anyone.” The finished and…
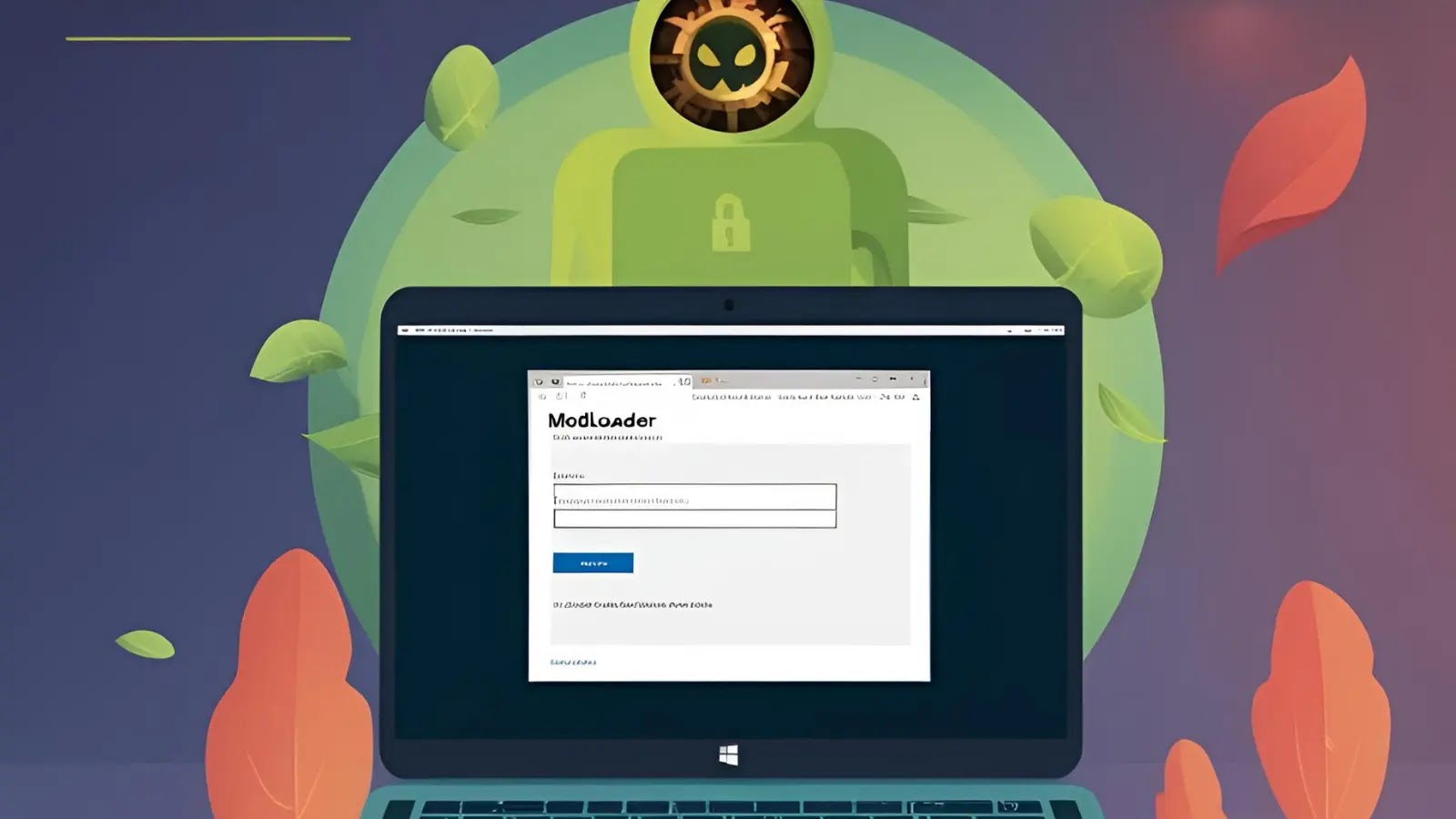
AhnLab Security Intelligence Center (ASEC) has recently uncovered a malicious campaign distributing ModiLoader (also known as DBatLoader) malware through phishing…
Continuous Threat Exposure Management (CTEM) has moved from concept to cornerstone, solidifying its role as a strategic enabler for CISOs….
Cyber threats have been real and present for a long time – but the evidence suggests that there has been…
Cybersecurity is the frontline of our national security. President Donald Trump and his adviser, Elon Musk, are doing more damage…
Amber Scorah knows only too well that powerful stories can change society—and that powerful organizations will try to undermine those…
Threat actors exploited a known vulnerability, CVE-2023-22527, a template injection flaw in Atlassian Confluence servers exposed to the internet. This…
Disciplined, well-trained, and well-equipped, AI agents are digital soldiers. They operate independently to carry out their orders, working tirelessly to…
Denmark-based SaaS backup provider Keepit is adding to functionality in June and July that includes support for Atlassian dev workflow…
As soon as Format Boy answers the phone, I recognize his booming voice. I’ve spent weeks immersed in the influencer’s…
A reliable VMware environment reporting tool, RVTools, was momentarily infiltrated earlier this week on May 13, 2025, to disseminate the…