Microsoft has confirmed that some Windows 10 and Windows 10 Enterprise LTSC 2021 systems will boot into BitLocker recovery after…
A newly discovered class of vulnerabilities in Intel processors, termed Branch Predictor Race Conditions (BPRC), allows attackers to systematically extract…
A newly identified ransomware campaign has emerged, seemingly targeting supporters of Elon Musk through a highly sophisticated phishing-based attack. Cybersecurity…
Coinbase responded to a security incident with combative measures Thursday after the company said cybercriminals bribed some of the cryptocurrency…
Security Operations Centers (SOCs) and Managed Security Service Providers (MSSPs) operate at the forefront of cybersecurity, tasked with defending organizations…
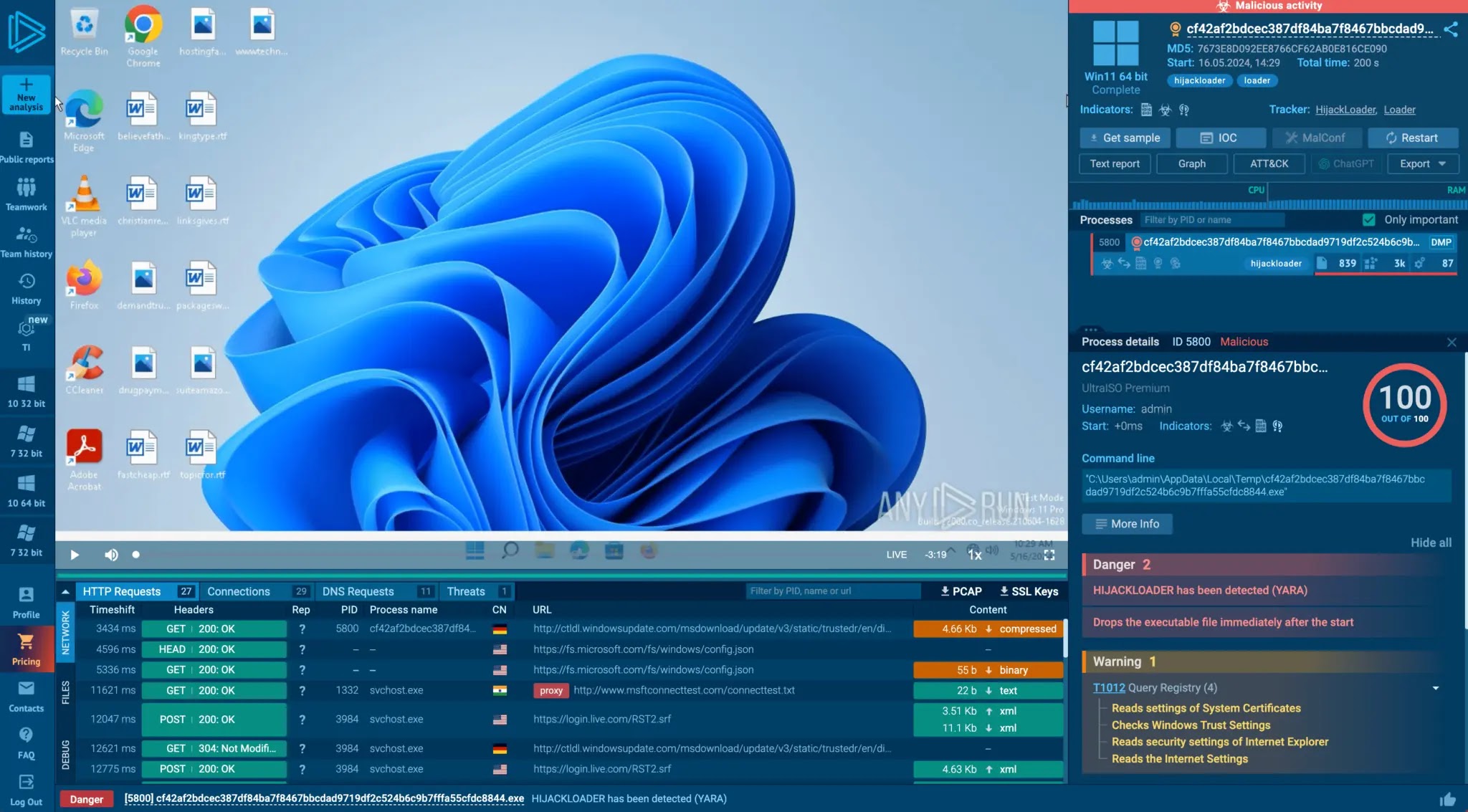
A startling discovery in the npm ecosystem has revealed a highly sophisticated malware campaign embedded within the seemingly innocuous package…
A recent breach of the LockBit ransomware group’s infrastructure resulted in the leak of an internal database, revealing significant intelligence…
When Donald Trump was on the campaign trail, he argued that coordination by the Biden administration and social media companies…
During the second day of Pwn2Own Berlin 2025, competitors earned $435,000 after exploiting zero-day bugs in multiple products, including Microsoft…
Apple’s macOS Gatekeeper, a cornerstone of the operating system’s defense against malicious software, has undergone significant macOS Sequoia (15.0) updates…
A serious security flaw affecting the Eventin plugin, a popular event management solution for WordPress, was recently discovered by Denver…
Ivanti EPMM users urgently need to patch against actively exploited 0day vulnerabilities (CVE-2025-4427, CVE-2025-4428) that enable pre-authenticated remote code execution,…