Although companies may embrace emerging technologies to remain competitive, they can be risk averse, especially when it comes to changing…
Quantum computing is on the verge of revolutionizing the technology landscape, much like AI did in 2024. By the end…
Operation RoundPress targets webmail software to steal secrets from email accounts belonging mainly to governmental organizations in Ukraine and defense…
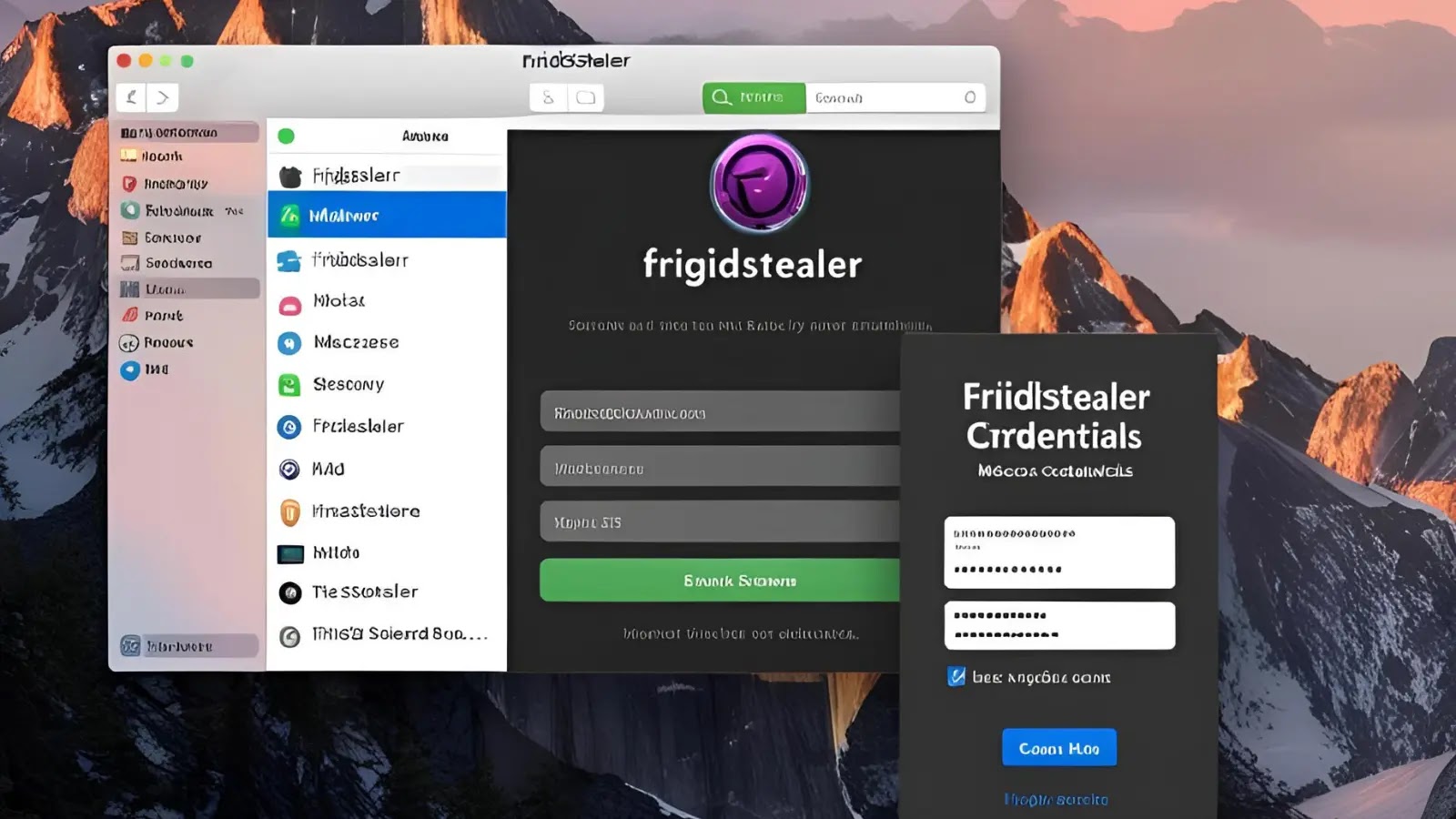
An macOS users, a new information-stealing malware dubbed FrigidStealer has emerged as a formidable threat since January 2025. This insidious…
EU privacy advocacy group NOYB has clapped back at Meta over its plans to start training its AI model on…
May 16, 2025Ravie LakshmananUnited States Cybersecurity researchers are calling attention to a new botnet malware called HTTPBot that has been…
External security tests on the government’s flagship digital identity system, Gov.uk One Login, have found serious vulnerabilities in the live…
Alkem Laboratories Ltd has revealed that its wholly owned subsidiary, Enzene Biosciences, was the target of a cyberattack affecting its…
Federal Bureau of Investigation has issued a warning about an ongoing malicious messaging campaign targeting current and former senior US…
A high-severity Chrome vulnerability (CVE-2025-4664) that Google has fixed on Wednesday is being leveraged by attackers, CISA has confirmed by…
Data is the lifeblood of productivity, and protecting sensitive data is more critical than ever. With cyber threats evolving rapidly…
Meta plans to train AI on EU user data from May 27 without consent Pierluigi Paganini May 16, 2025 Meta…