Critical zero-day vulnerability in Microsoft’s Scripting Engine (CVE-2025-30397) has been confirmed to enable remote code execution (RCE) attacks over networks,…
The fall of two of the most dominant ransomware syndicates, LockBit and AlphV, triggered a power vacuum across the cybercriminal…
Microsoft has disclosed a significant security vulnerability (CVE-2025-30400) affecting the Windows Desktop Window Manager (DWM) that is actively being exploited…
Google, the global leader in the tech world, is gearing up to roll out a major security update for users…
Insider risk is not just about bad actors. Most of the time, it’s about mistakes. Someone sends a sensitive file…
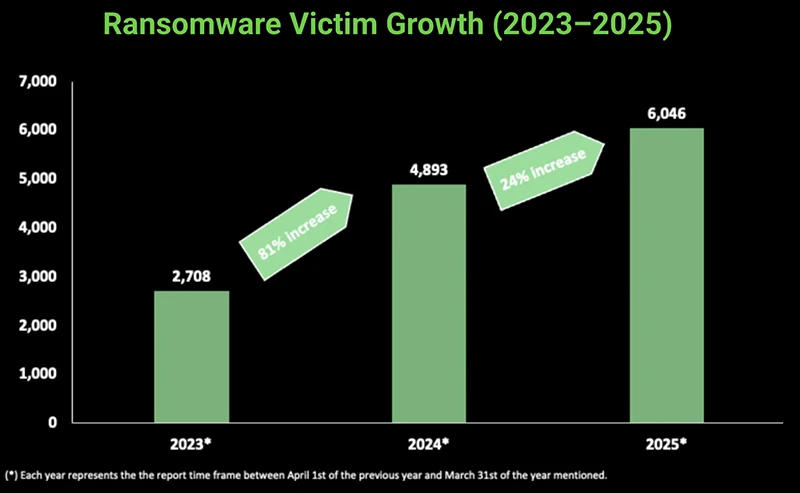
In today’s sophistication driven world, ransomware attacks have become one of the most pervasive and damaging forms of cybercrime. These…
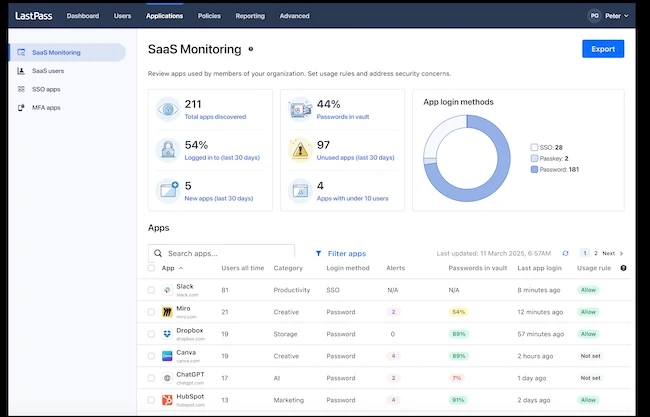
LastPass has announced the general availability of SaaS Monitoring. This new capability empowers organizations of all sizes to gain visibility…
May 14, 2025Ravie LakshmananVulnerability / Endpoint Security Ivanti has released security updates to address two security flaws in Endpoint Manager…
Microsoft has disclosed a significant security vulnerability (CVE-2025-30400) affecting the Windows Desktop Window Manager (DWM) that is actively being exploited…
It’s been impossible to avoid the buzz around generative AI, especially since ChatGPT took the world by storm. And while…
In this Help Net Security interview, Carrie Mills, VP and CISO, Southwest Airlines talks about the cybersecurity challenges facing the…
May 14, 2025Ravie LakshmananVulnerability / Network Security Fortinet has patched a critical security flaw that it said has been exploited…