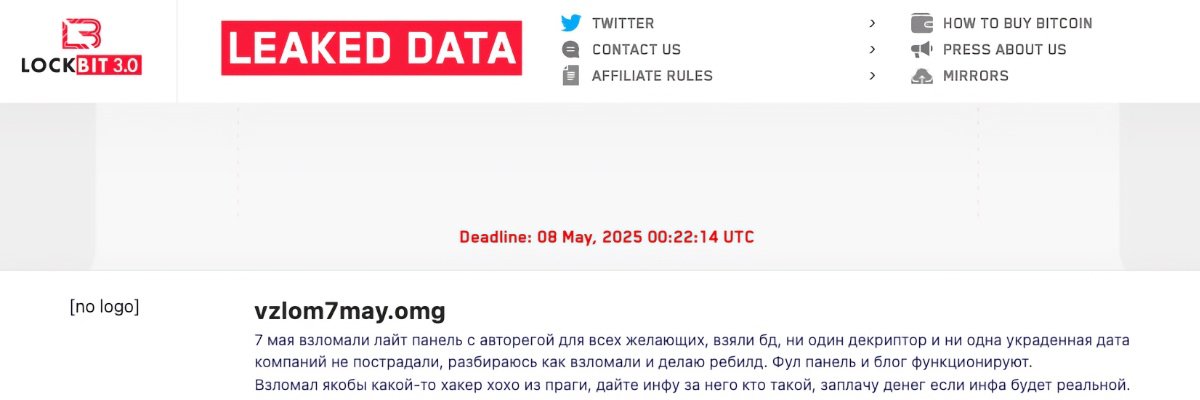
On 7 May 2024, the presumed identity of the operator of the LockBit 3.0 franchise, also known as LockBitSupp, was…
The Federal police in Germany (BKA) seized the server infrastructure and shut down the ‘eXch’ cryptocurrency exchange platform for alleged money…
Cybersecurity researchers are raising the alarm about a newly discovered commodity ransomware strain dubbed Mamona, which is rapidly spreading across Windows…
Amanda Stent was researching natural language processing (NLP) at a time when there were only around 20 people in the…
A critical remote code execution (RCE) vulnerability, identified as CVE-2025-31324, in SAP NetWeaver Visual Composer 7.x is being actively exploited…
Cybercriminals are increasingly targeting IT administrators through sophisticated Search Engine Optimization (SEO) poisoning techniques. By leveraging SEO tactics typically used…
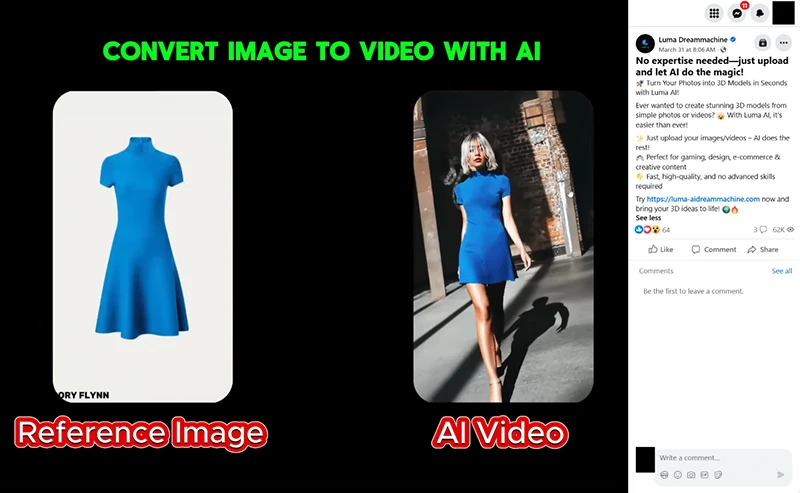
A clever malware campaign delivering the novel Noodlophile malware is targeting creators and small businesses looking to enhance their productivity…
May 09, 2025Ravie LakshmananSupply Chain Attack / Malware Cybersecurity researchers have flagged three malicious npm packages that are designed to…
Companies are sitting on a wealth of valuable data that could be used to share relevant information with employees to…
A recent discovery by the FortiMail Incident Response team has revealed a highly sophisticated email campaign targeting organizations in Spain,…
Cybercrime Magazine caught up with Dr. Taher Elgamal, Partner at Evolution Equity Partners, at the recent RSA Conference 2025 in San Francisco. The tech…
May 09, 2025The Hacker NewsArtificial Intelligence / Software Security AI agents are changing the way businesses work. They can answer…