The government has plans to increase the number of girls taking maths at A-level in a bid to encourage more…
Cybercriminal services target end-of-life routers, FBI warns Pierluigi Paganini May 09, 2025 The FBI warns that attackers are using end-of-life…
Cybersecurity researchers at Kaspersky have identified a new supply chain vulnerability emerging from the widespread adoption of AI-generated code. As…
A flaw in Microsoft Entra ID’s legacy login allowed attackers to bypass MFA, targeting admin accounts across finance, healthcare, and…
The affiliate panel of the infamous LockBit Ransomware-as-a-Service (RaaS) group has been hacked and defaced, showing a link to a…
May 09, 2025Ravie LakshmananMalware / Email Security Cybersecurity researchers are warning of a new campaign that’s targeting Portuguese-speaking users in…
Danish engineers are drawing up plans to connect an Apple datacentre to a district heating network in Denmark that will…
First came the bullets, then came the bots. In the wake of India’s April 22 terror attack in Pahalgam and…
Critical vulnerability in Apache ActiveMQ (CVE-2024-XXXX) exposes brokers to denial-of-service (DoS) attacks by allowing malicious actors to exhaust system memory…
A new wave of cyberattacks is targeting Active Directory (AD) environments by abusing Windows Remote Management (WinRM), a legitimate administrative…
QR codes have quietly become a part of everyday business workflows. From authentication to employee onboarding, marketing, and resource sharing,…
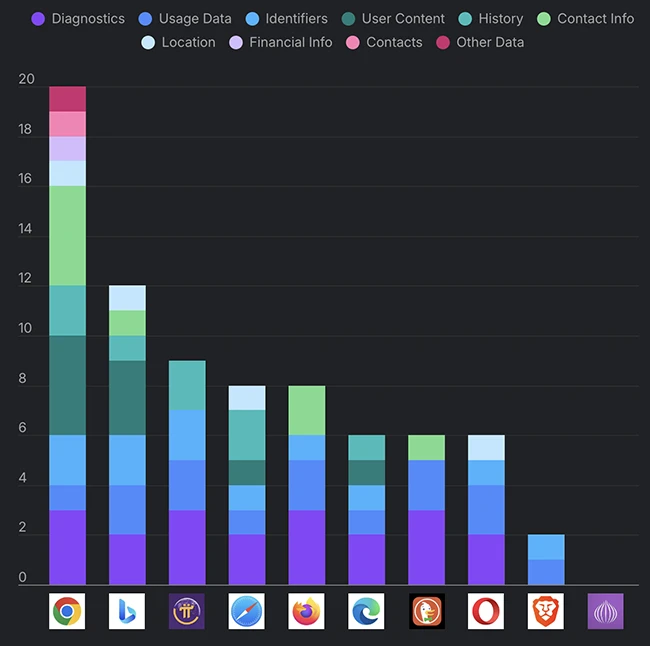
Chrome and Safari are the most popular browser apps, accounting for 90% of the mobile browsers market share, according to…