Education giant Pearson suffered a cyberattack, allowing threat actors to steal corporate data and customer information, BleepingComputer has learned. Pearson…
ESET, a leading cybersecurity firm, has shed light on one particularly insidious scheme: fake calls purportedly from government officials demanding…
PowerSchool paid ransom after a major data breach; now hackers are targeting teachers and schools with direct extortion threats for…
As tensions flare and the possibility of full blown armed conflict between India and Pakistan grows, there is a need…
Microsoft has announced its support for the Agent2Agent (A2A) protocol, an open standard developed in collaboration with industry partners including…
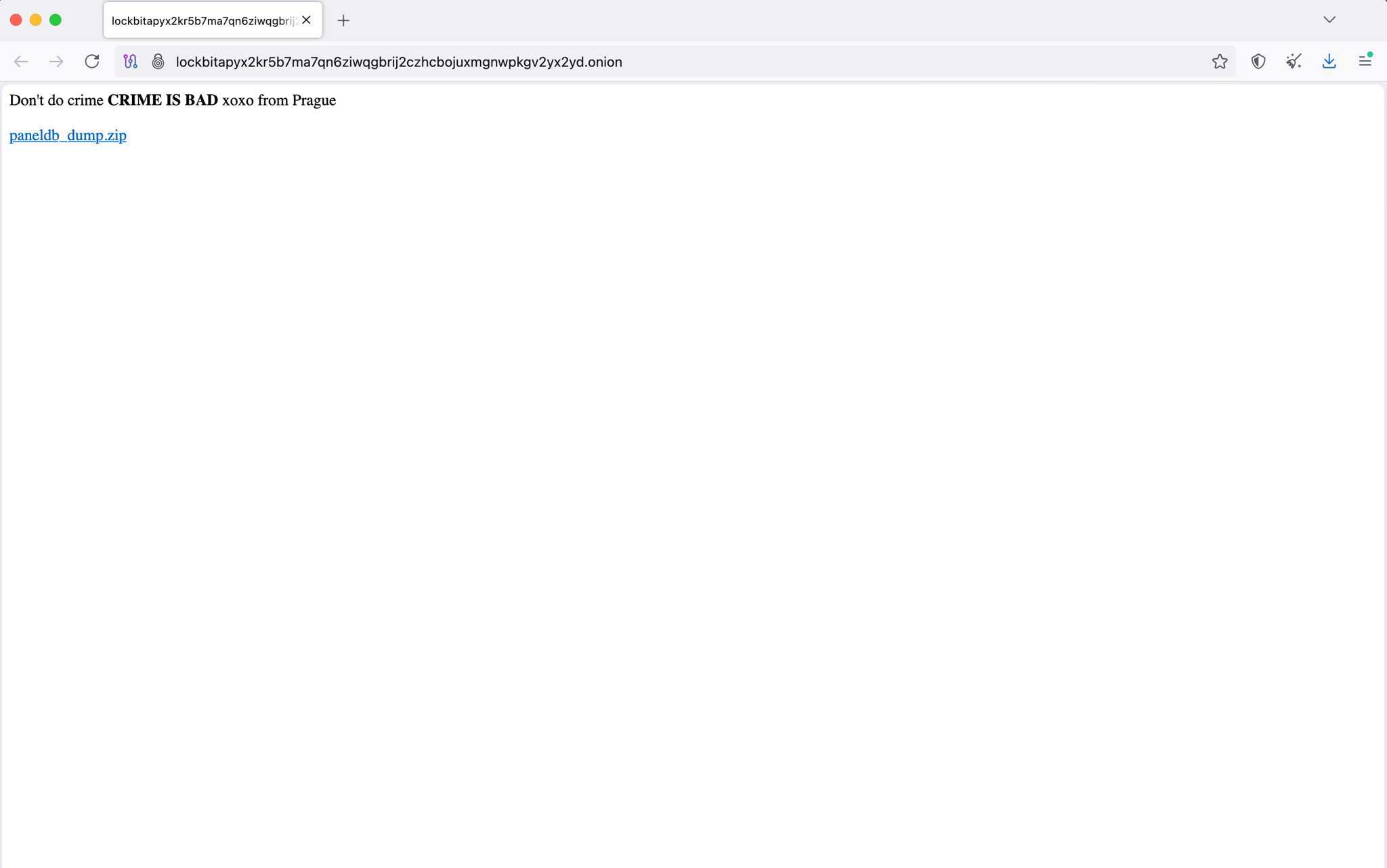
The LockBit ransomware site was breached, database dump was leaked online Pierluigi Paganini May 08, 2025 Lockbit ransomware group has…
A malicious Python package targeting Discord developers with remote access trojan (RAT) malware was spotted on the Python Package Index (PyPI)…
Cisco has released security updates addressing a critical vulnerability in the Switch Integrated Security Features (SISF) of multiple software platforms…
In its second international trade deal in the space of a week, the UK government has secured a major trade…
A critical security vulnerability in IXON’s widely used VPN client has exposed Windows, Linux, and macOS systems to local privilege…
The relentless battle against online fraud is a constant evolution, a digital chase where security teams and malicious actors continually…
The US authorities have released new guidance for owners of critical national infrastructure in the face of an undisclosed number…