ChatGPT, launched in 2022, began making a significant impact on the market by late 2023, according to Synergy Research Group….
The Federal Bureau of Investigation (FBI) in a new warning cautioned a sharp increase in ATM jackpotting incidents across the…
Google Suspends OpenClaw Users Google has suspended access to its Antigravity AI platform for numerous users of the open-source tool…
Samsung will add Perplexity to its next generation of Galaxy devices as part of the expansion of its Galaxy AI…
Last week on Malwarebytes Labs: Stay safe! We don’t just report on privacy—we offer you the option to use it….
X (formerly Twitter) has filed an appeal against the €120 million penalty imposed by the European Commission under the Digital…
February 21, 2026, marks one year since North Korea (DPRK)-linked operators stole approximately $1.46 billion in cryptoassets from Dubai-based exchange…
Fake and expired IDs keep showing up in routine customer transactions, from alcohol purchases to credit card applications. The problem…
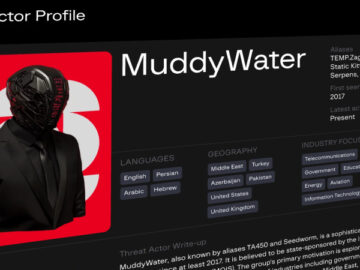
Ravie LakshmananFeb 23, 2026Threat Intelligence / Artificial Intelligence The Iranian hacking group known as MuddyWater (aka Earth Vetala, Mango Sandstorm,…
The cybersecurity community recently witnessed the emergence of targeted malware campaigns linked to the Silver Fox threat group. This operation…
Anthropic brings Claude Code Security to Claude Code on the web through a limited research preview. Claude Code Security (Source:…
North Korean state-backed hackers are running large-scale fake IT worker and “Contagious Interview” campaigns that abuse developer hiring workflows to…