A former information technology manager has filed a whistleblower lawsuit alleging a major security breach at Deutsche Bank’s Manhattan headquarters,…
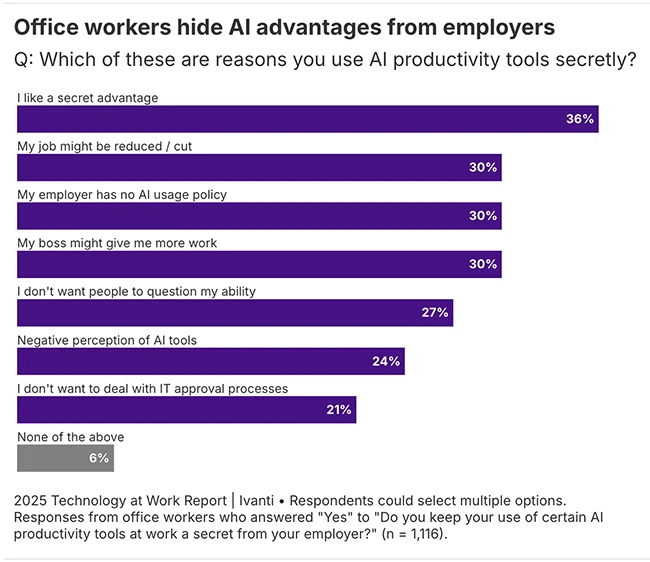
Employees are feeling heightened concerns around the use of technology to enhance productivity, as well as job dissatisfaction and a…
The California Privacy Protection Agency (CPPA) has announced that national clothing retailer Todd Snyder, Inc. must pay a $345,178 fine…
A federal jury in California has ordered Israeli spyware maker NSO Group to pay approximately $168 million in damages to…
Application security is changing fast. In this Help Net Security interview, Loris Gutic, Global CISO at Bright, talks about what…
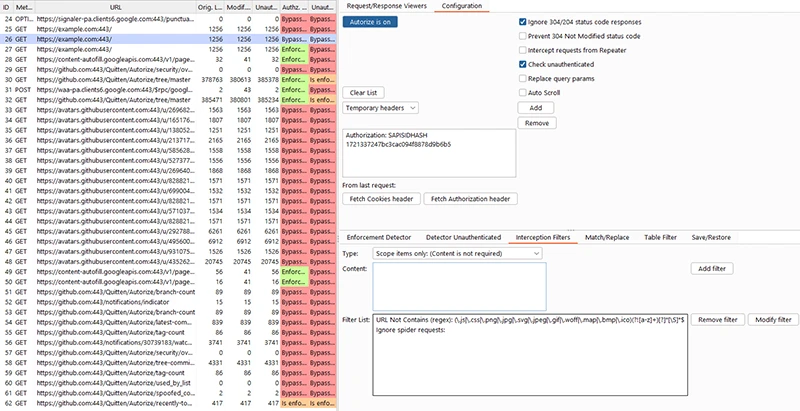
Autorize is an open-source Burp Suite extension that checks if users can access things they shouldn’t. It runs automatic tests…
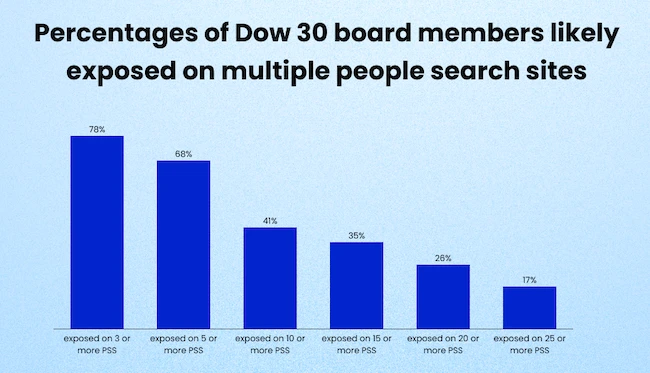
The personal information of 75% of corporate directors can be found on people search sites, according to Incogni. People search…
Football Australia is set to use AI camera technology and NBN connectivity at key venues to automatically capture and stream…
Cisco Systems showed a prototype chip for networking quantum computers together and said it is opening a new lab in…
Cybercriminals are using fake Social Security Administration emails to distribute the ScreenConnect RAT (Remote Access Trojan) and compromise user computers….
The government will prioritise cyber security and cyber technology in its forthcoming industrial strategy as it looks for ways to…
A federal jury decided Tuesday that NSO Group must pay WhatsApp approximately $168 million in damages after a judge ruled…