Domino’s Pizza Enterprises is a year into using an internal developer platform (IDP) to simplify how software components are supported…
The communication app TeleMessage Signal, used by at least one top Trump administration official to archive messages, has already reportedly…
Amazon.com’s self-driving unit Zoox agreed to recall 270 driverless vehicles after an unoccupied robotaxi was involved in an April 8…
President Donald Trump is calling on Colorado state officials to release Tina Peters, the former Mesa County clerk serving a…
Tulsi Gabbard, the director of national intelligence, used the same easily cracked password for different online accounts over a period…
A major cyberattack on the Coweta County School System’s computer network occurred late Friday night, which is a worrying development for New Mexico’s educational institutions. The unauthorized intrusion, detected around 7:00 p.m., prompted immediate action from the school system’s IT department and external…
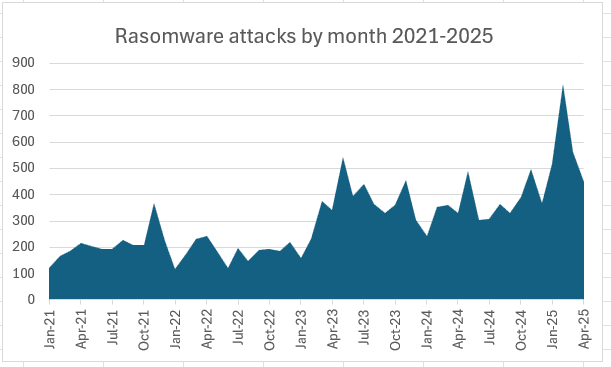
Qilin became the top ransomware group in April amid uncertainty over the status of RansomHub, according to a Cyble blog…
Qilin became the top ransomware group in April amid uncertainty over the status of RansomHub, according to a Cyble blog…
House appropriators on Tuesday challenged proposed budget cuts for the Cybersecurity and Infrastructure Security Agency, with Democrats saying the Trump…
Microsoft announced a major update aimed at bolstering the cybersecurity of its flagship AI-powered productivity assistant, Microsoft 365 Copilot, and…
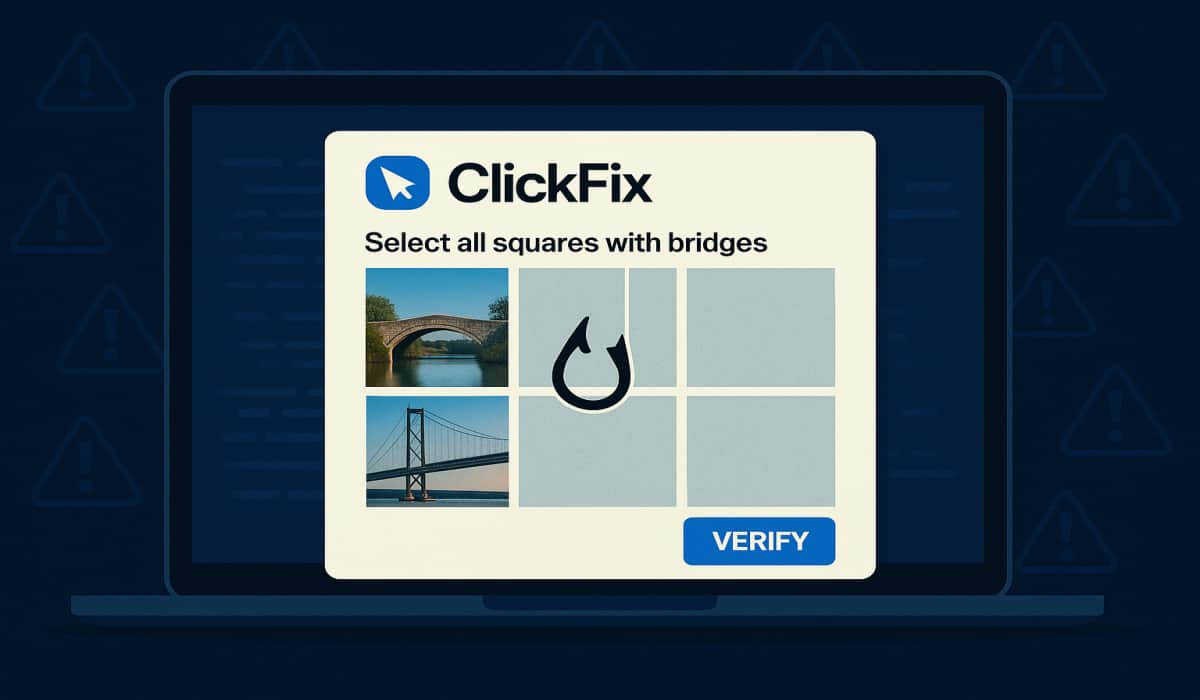
Cybercriminals aren’t always loud and obvious. Sometimes, they play it quiet and smart. One of the tricks of making the…
Samsung MagicINFO flaw exploited days after PoC exploit publication Pierluigi Paganini May 06, 2025 Threat actors started exploiting a vulnerability…