One almost feels a little nostalgic for the days of old-school phishing attacks, those poorly worded, spray-and-pray emails that most…
Google fixed actively exploited Android flaw CVE-2025-27363 Pierluigi Paganini May 06, 2025 Google addressed 46 Android security vulnerabilities, including one…
CISA has added a critical Langflow vulnerability to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation in…
Hackers are leveraging a sophisticated social engineering technique dubbed “ClickFix” to trick Windows users into executing malicious scripts on their…
An easily and remotely exploitable vulnerability (CVE-2024-7399) affecting Samsung MagicINFO, a platform for managing content on Samsung commercial displays, is…
As global chief innovation officer (CIO) at EY, Joe Depa helps his firm embrace new ideas that boost service delivery…
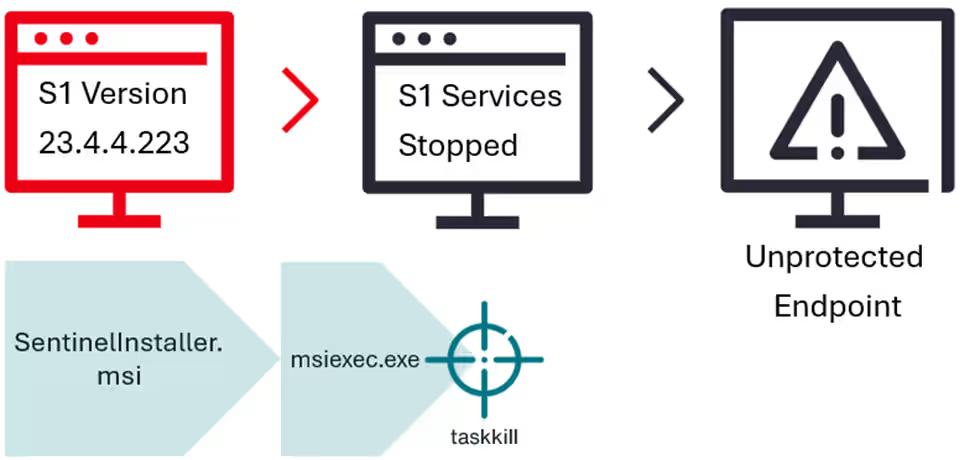
New ‘Bring Your Own Installer (BYOI)’ technique allows to bypass EDR Pierluigi Paganini May 06, 2025 A new BYOI technique…
A supply-chain attack targets Linux servers with disk-wiping malware hidden in Golang modules published on GitHub. The campaign was detected…
A newly discovered vulnerability in Microsoft’s Windows Deployment Services (WDS) allows attackers to remotely crash servers with zero user interaction…
United States Customs and Border Protection is asking tech companies to send pitches for a real-time facial recognition tool that…
A newly identified cyberattack campaign has surfaced, leveraging the recognizable branding of India’s Ministry of Defence to distribute cross-platform malware…
In today’s world, more employees work from home, coffee shops, or satellite offices than ever before. While remote access tools…