Over 14,000 Queensland public service workers have adopted the state government’s generative AI tool, QChat, nearly a year after it…
The Darcula phishing-as-a-service (PhaaS) platform stole 884,000 credit cards from 13 million clicks on malicious links sent via text messages…
Transport for NSW is expanding its SAP Ariba service to improve supplier vetting in its procurement activities. The transport department…
Dive Brief: The Department of Defense is streamlining its software-procurement approval process. The Pentagon on Monday announced that its “Software…
A new “Bring Your Own Installer” EDR bypass technique is exploited in attacks to bypass SentinelOne’s tamper protection feature, allowing threat…
Why Application Security is Non-Negotiable The resilience of your digital infrastructure directly impacts your ability to scale. And yet, application…
Microsoft warns about the security risks posed by default configurations in Kubernetes deployments, particularly those using out-of-the-box Helm charts, which…
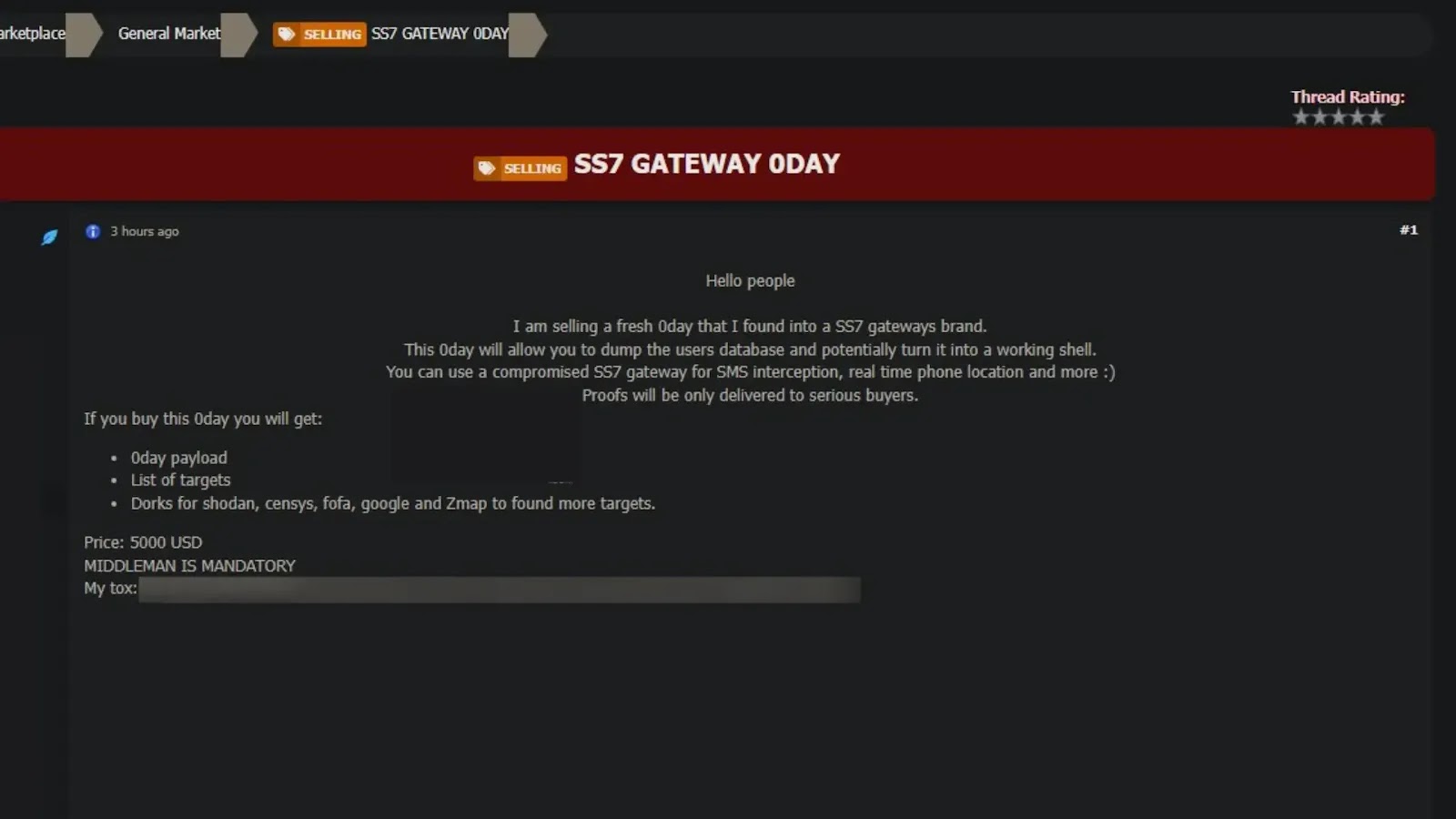
A newly discovered dark web listing claims to sell a critical SS7 protocol exploit for $5,000, raising alarms about global…
TeleMessage, an Israeli company that sells an unofficial Signal message archiving tool used by some U.S. government officials, has suspended…
The LUMMAC.V2 infostealer malware, also known as Lumma or Lummastealer, has emerged as a significant threat, employing the cunning “ClickFix”…
May 05, 2025Ravie LakshmananVulnerability / Zero-Day The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a maximum-severity security flaw…
The Seqrite Labs APT team has uncovered a sophisticated cyber campaign by the Pakistan-linked Transparent Tribe (APT36) targeting Indian Government…