Security researchers have uncovered a series of critical vulnerabilities in the Tenda RX2 Pro Dual-Band Gigabit Wi-Fi 6 Router (Firmware…
The industry treats API security like a checklist—patch a few issues, enforce some rules, and move on. But these risks…
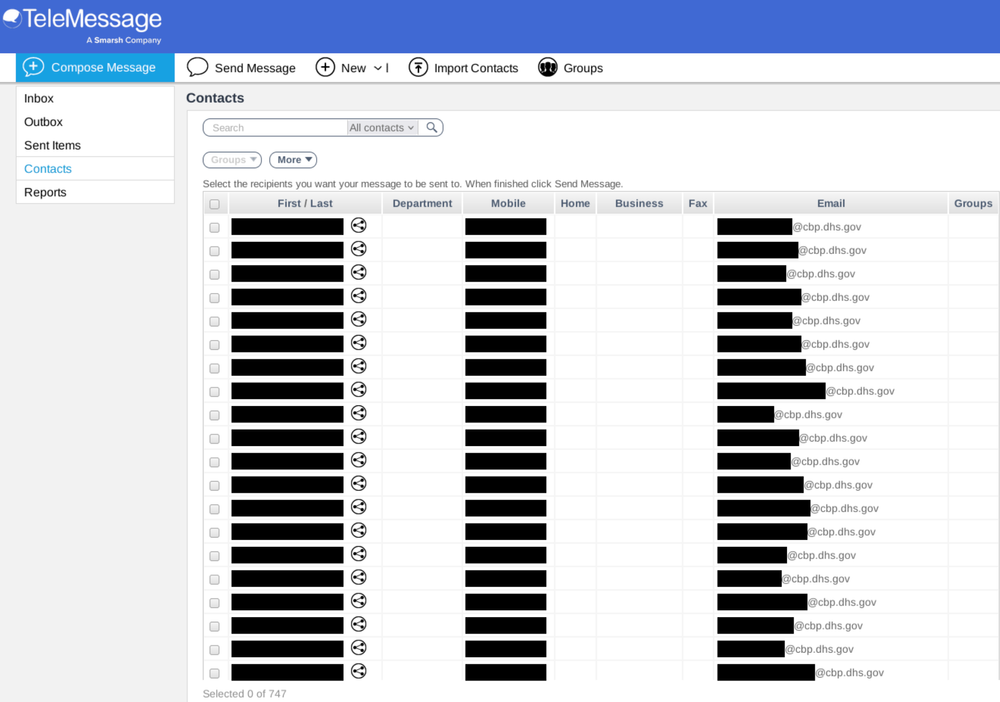
A hacker stole data from TeleMessage, the firm that sells modified versions of Signal to the U.S. gov Pierluigi Paganini May…
Leading cryptocurrency exchange Kraken has disclosed that it recently thwarted an infiltration attempt by a suspected North Korean hacker posing…
UK-based retailers Marks & Spencer, Co-op, and Harrods have been targeted by cyber attackers in the last few weeks. Whether…
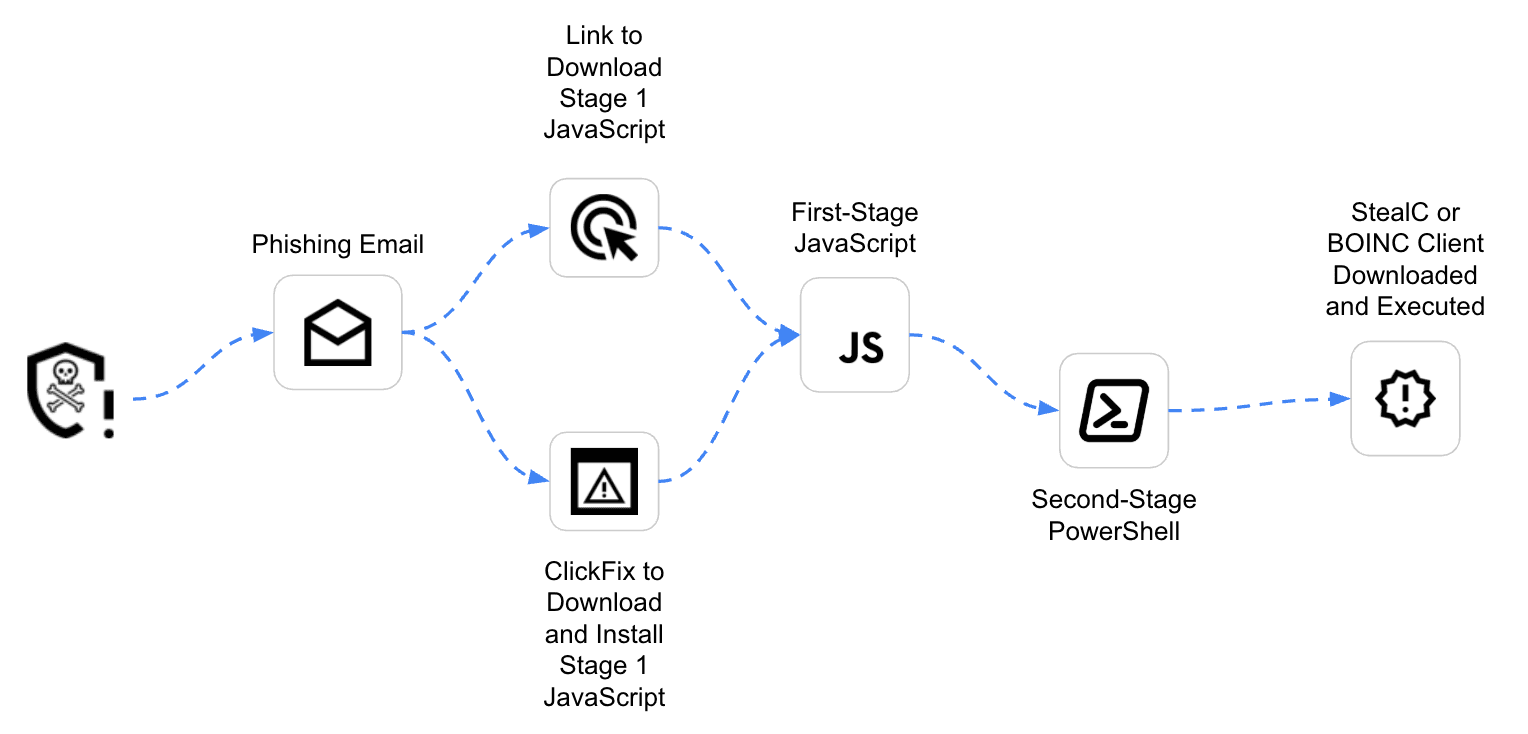
Experts shared up-to-date C2 domains and other artifacts related to recent MintsLoader attacks Pierluigi Paganini May 05, 2025 MintsLoader is…
Microsoft has silently fixed an issue that broke Start Menu jump lists for all apps on systems running Windows 10,…
Cloudflare’s Q1 2025 DDoS Threat Report: DDoS attacks surged 358% YoY to 20.5M. Germany hit hardest; gaming and telecom were…
Artem Stryzhak, a Ukrainian national, has been extradited from Spain to the United States to face charges related to a…
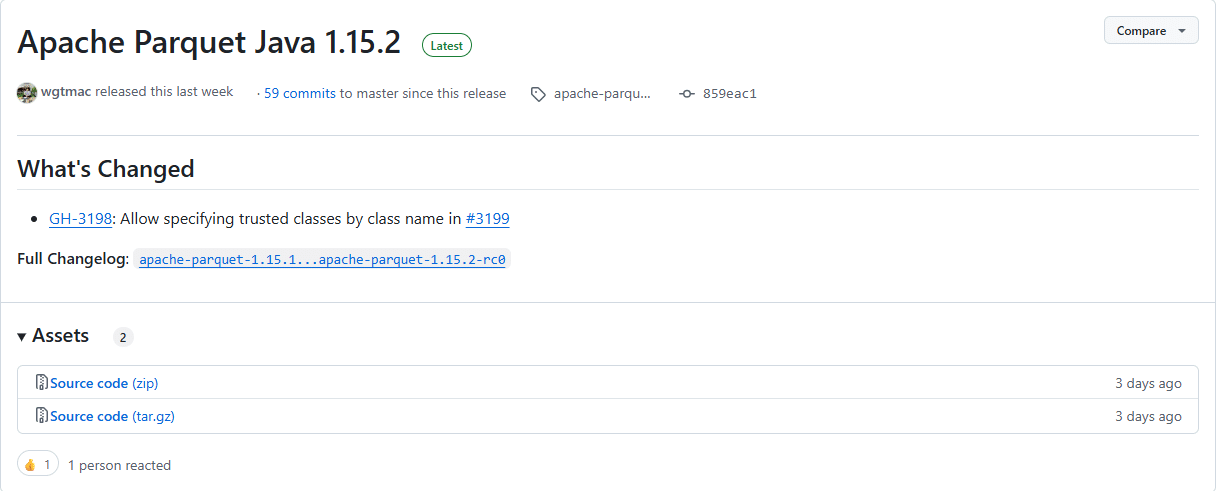
A vulnerability has been identified in Apache Parquet Java, which could leave systems exposed to remote code execution (RCE) attacks….
Microsoft announced over the weekend that the Windows 11 24H2 update is ready to roll out to all compatible PCs,…
A high-severity vulnerability (CVE-2025-46762) has been discovered in Apache Parquet Java, exposing systems using the parquet-avro module to remote code…