Cybersecurity researchers are raising alarms as hackers increasingly weaponize email input fields to execute cross-site scripting (XSS) and server-side request forgery (SSRF) attacks. These…
Regular User Access Reviews are required for regulatory compliance with standards such as SOX, HIPAA, GLBA, PCI, NYDFS, NYSDOH, and…
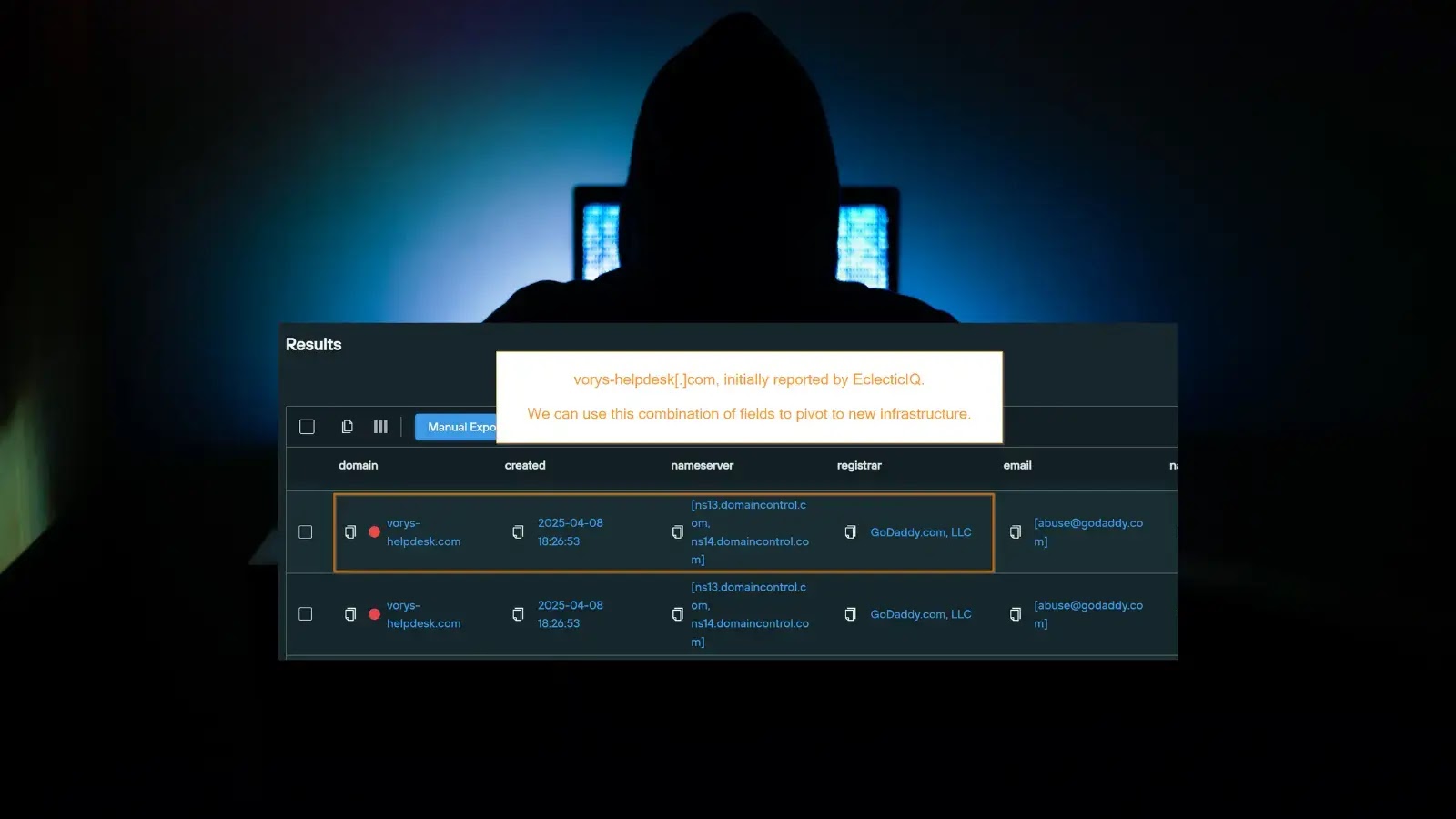
A recent investigation by cybersecurity firm EclecticIQ, in collaboration with threat hunters, has exposed a surge in malicious activity tied…
May 2, 2025 – Passwords are becoming things of the past. Passkeys are more secure, easier to manage, and speed…
A critical new attack chain, dubbed “SonicBoom,” that enables remote attackers to bypass authentication and seize administrative control over enterprise…
A researcher has unveiled a novel integration between AI-powered Copilot and Microsoft’s WinDbg, dramatically simplifying Windows crash dump analysis. For…
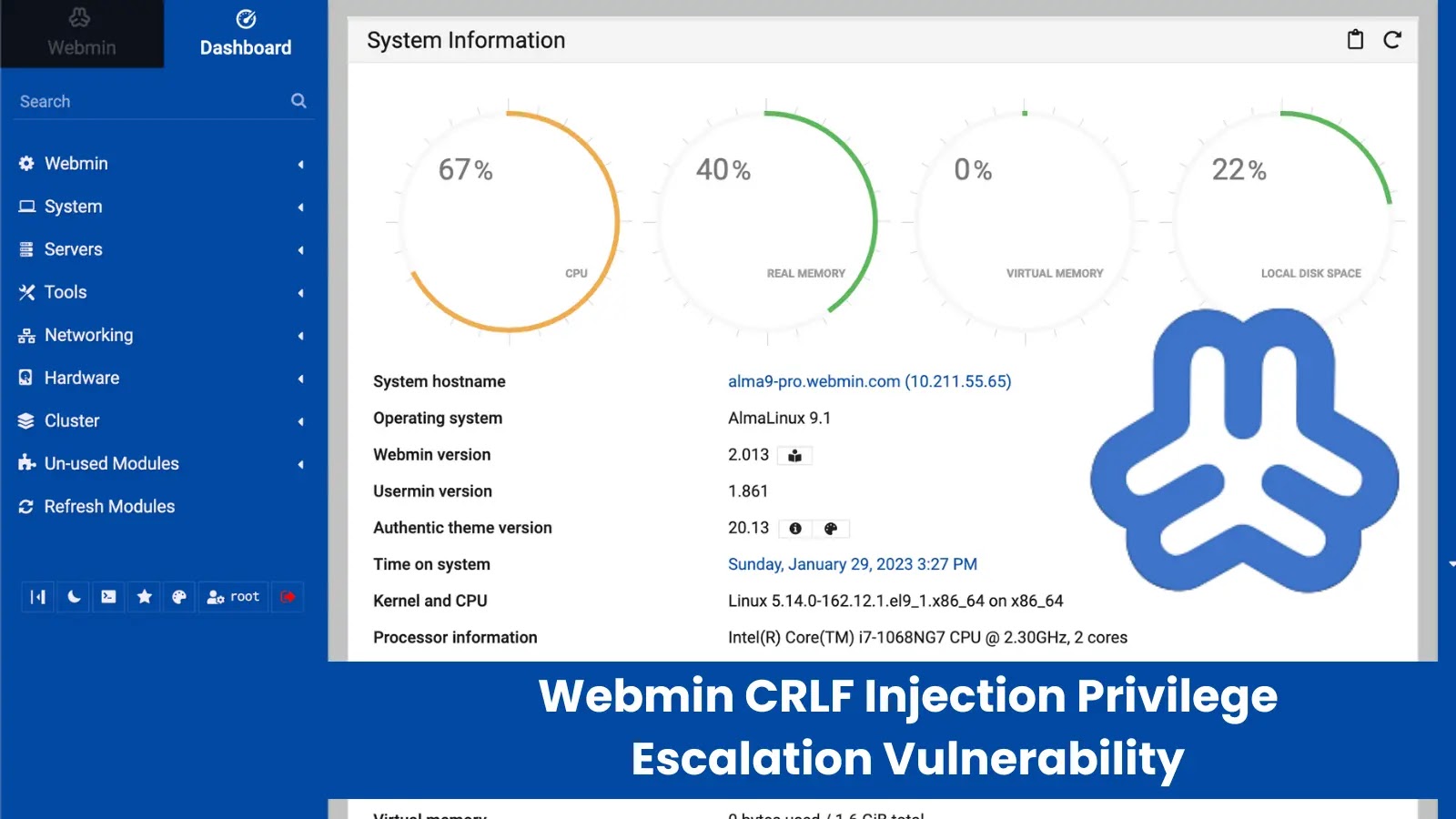
A critical security vulnerability in Webmin, a widely-used web-based system administration tool, has been discovered, allowing remote attackers to escalate…
Cybersecurity researchers have uncovered a dangerous new exploitation technique, dubbed the “SonicBoom Attack Chain,” which allows hackers to bypass authentication…
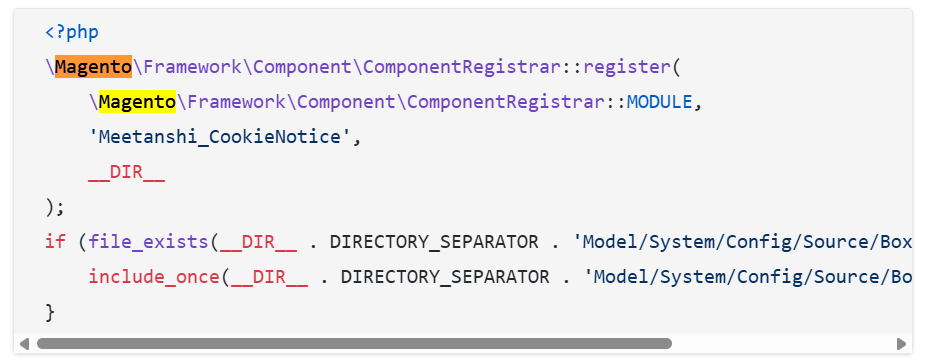
Sansec uncovered a supply chain attack via 21 backdoored Magento extensions Pierluigi Paganini May 05, 2025 Supply chain attack via…
In a notable development that will affect numerous businesses globally, Microsoft has announced that it will commence the rejection of…
Over the past two weeks, media outlets have been rife with speculations about a significant cyber attack affecting three major…
Effective Vulnerability Management offers a view of a key part of cybersecurity, showing how practices, tools, and processes can help…