National Cyber Security Centre (NCSC) has issued technical guidance following a series of cyber attacks targeting UK retailers. These incidents…
In this Help Net Security interview, Stuart Clarke, CEO at Blackdot Solutions, discusses the strategic use of open-source intelligence (OSINT)…
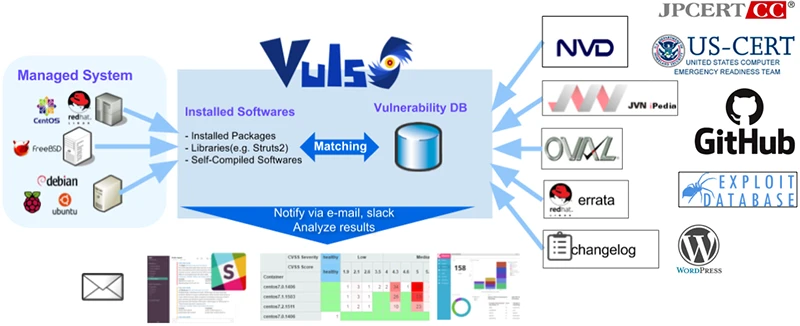
Vuls is an open-source tool that helps users find and manage security vulnerabilities. It was created to solve the daily…
90% of IT and security leaders said their organization experienced a cyberattack within the last year, according to a report…
04 May Global Ransomware Damage Costs Predicted To Exceed $275 Billion By 2031 Posted at 22:09h in Blogs, Videos by…
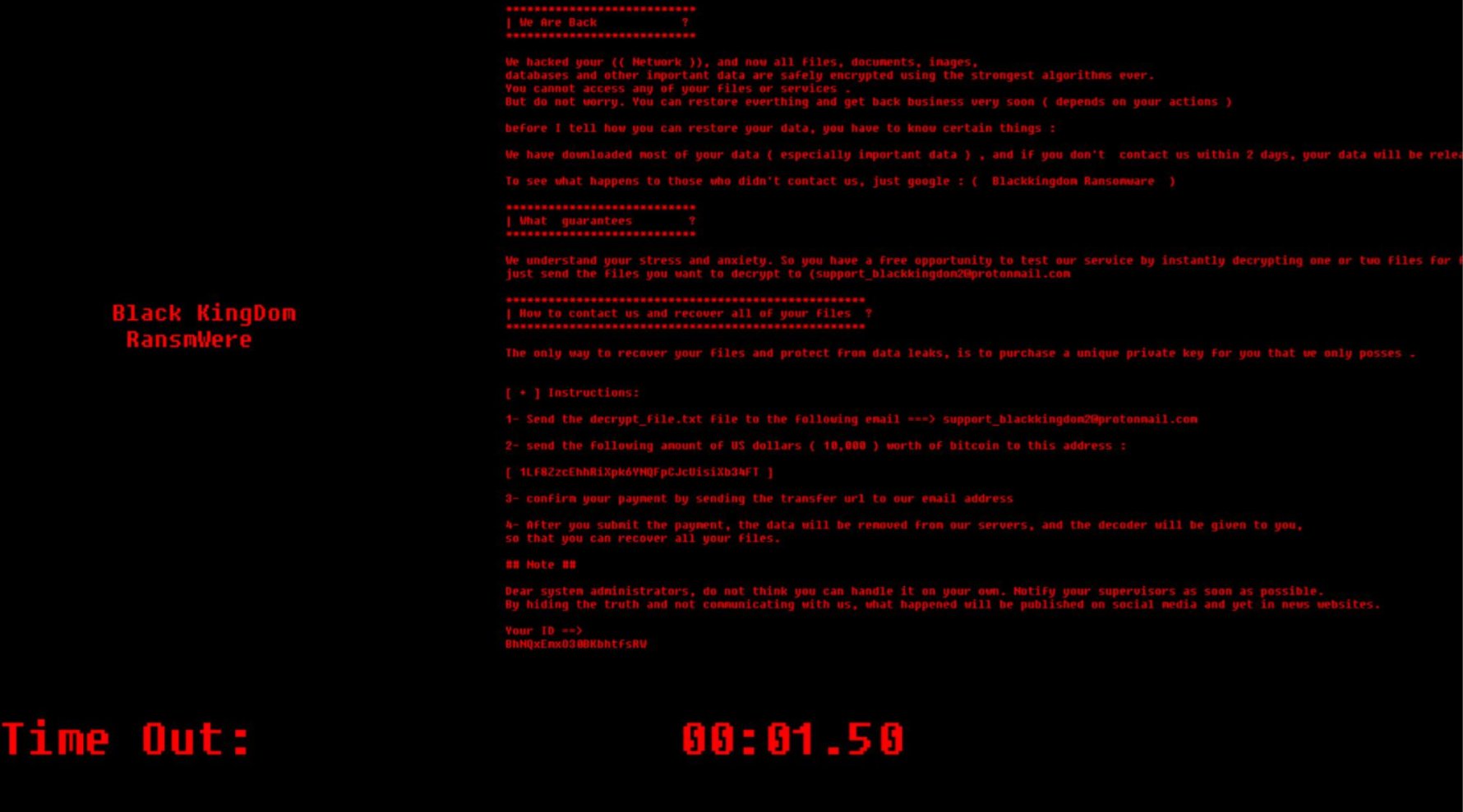
US authorities have indicted Black Kingdom ransomware admin Pierluigi Paganini May 05, 2025 A 36-year-old Yemeni man behind Black Kingdom…
Apple is partnering with Amazon-backed startup Anthropic on a new “vibe-coding” software platform that will use artificial intelligence to write,…
A US government-created artificial intelligence program that aims to predict the supply and price of critical minerals has been transferred…
Airservices Australia has consolidated technology functions into a newly formed division led by chief information security officer Anthony Kitzelmann. The…
The ACT has ended its seven-year run of supplying Lenovo Chromebooks to public schools, opting instead for devices from ASUS…
OpenAI admitted that it can be confusing for users to choose between all the different models, but the company has…
The creators of StealC, a widely-used information stealer and malware downloader, have released its second major version, bringing multiple stealth…