Security Operations Center (SOC) teams are facing a fundamentally new challenge — traditional cybersecurity tools are failing to detect advanced…
Former subpostmasters who suffered after being blamed for errors in the Post Office’s pre-Horizon software have said progress is being…
In 2025, with cybersecurity threats evolving at an unprecedented pace, effective patch management has never been more critical for organizational…
Security researchers have disclosed three critical vulnerabilities in the Netgear EX6200 Wi-Fi range extender that could allow remote attackers to…
Cybercriminals are having less success targeting end-user technology with zero-day attacks, said Google’s security team this week. While most attacks…
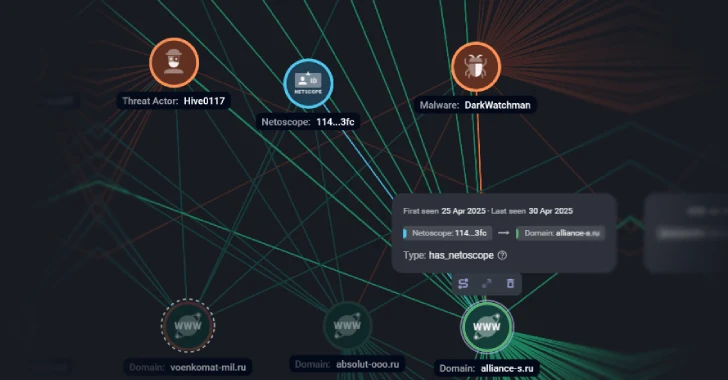
Russian companies have been targeted as part of a large-scale phishing campaign that’s designed to deliver a known malware called…
As the company boosts its investment in infrastructure for artificial intelligence (AI), Meta’s latest earnings call has painted a bleak…
The multi-cloud landscape has transformed enterprise IT, with over 87% of organizations now operating across multiple cloud platforms. This distributed…
For over a decade, application security teams have faced a brutal irony: the more advanced the detection tools became, the…
The need to find efficiencies, drive staff productivity and boost the in-store customer experience – not to mention ongoing efforts…
Security experts revealed a critical vulnerability in Ruby on Rails that allows attackers to bypass Cross-Site Request Forgery (CSRF) protections….
For decades, our digital world has relied on cryptography to keep secrets safe. From the passwords we type into banking…