Cisco Talos has uncovered a sophisticated and destructive cyberattack targeting a critical infrastructure entity in Ukraine, deploying a previously unknown…
Play ransomware group hit 900 organizations since 2022 Pierluigi Paganini June 06, 2025 A joint advisory from the US and…
The widespread text-sharing website Paste.ee has been used as a weapon by bad actors to spread powerful malware strains like…
Ransomware breaches continue to rise even as fewer victims pay, according to a Delinea report. 69% of organizations globally have…
The U.S. government has seized approximately 145 domains associated with the BidenCash marketplace and other criminal marketplaces, effectively dismantling one…
A critical memory leak vulnerability in Apache Tomcat’s HTTP/2 implementation (CVE-2025-31650) has been weaponized, enabling unauthenticated denial-of-service attacks through malformed…
Microsoft has been busy releasing more out-of-band (OOB) patches than usual throughout May. The May Patch Tuesday release of updates…
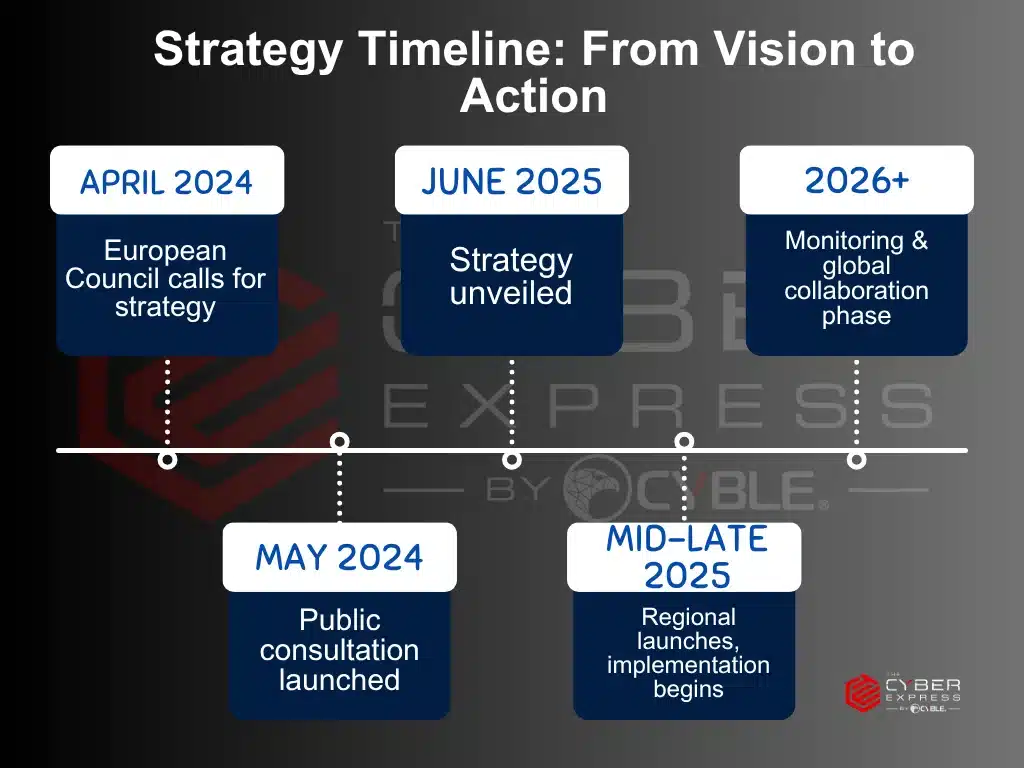
The European Commission and the High Representative for Foreign Affairs and Security Policy have jointly launched the European Union’s International…
In this Help Net Security interview, Benny Porat, CEO at Twine Security, discusses applying AI agents to security decisions. He…
Woolworths’ chief security officer Pieter van der Merwe will join Optus from later this year, coinciding with a change in…
Patient data is often stored or processed outside the country where it was collected. When that happens, the data falls…
Innovations of Secure AI We speak with Phil Tee, Zscaler, EVP, Head of AI Innovations at Zenith World 2025 in…