Cybersecurity company SentinelOne has revealed that a China-nexus threat cluster dubbed PurpleHaze conducted reconnaissance attempts against its infrastructure and some…
The U.S. Cybersecurity & Infrastructure Security Agency (CISA) is warning of Broadcom Brocade Fabric OS, Commvault web servers, and Qualitia…
A severe vulnerability, identified as CVE-2025-2783, has been discovered in Google Chrome, specifically targeting the Mojo inter-process communication (IPC) component…
According to the Center for Strategic & International Studies’ (CSIS) 2025 Space Threat Assessment, space systems’ susceptibility to cyberattacks has…
The Cybersecurity and Infrastructure Security Agency (CISA) has added three new flaws to its Known Exploited Vulnerabilities catalog on Monday,…
A University of Edinburgh report into the NHS AI Lab has identified “promising financial and patient care benefits” while also…
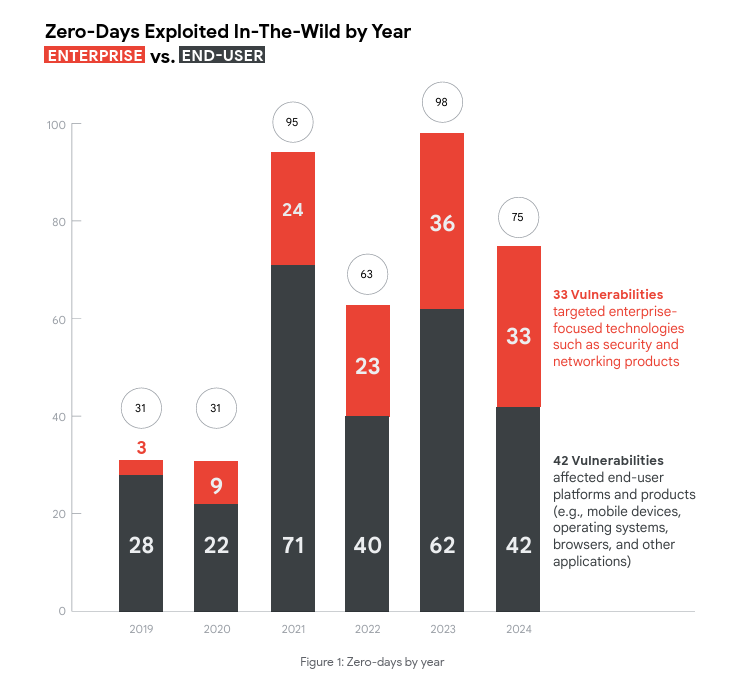
Google Threat Intelligence Group (GTIG) tracked 75 actively exploited zero-day flaws in 2024 Pierluigi Paganini April 29, 2025 Google tracked…
Apple’s AirPlay feature enables iPhones and Macbooks to seamlessly play music or show photos and videos on other Apple devices…
Europol has announced the launch of a powerful new Operational Taskforce (OTF), codenamed GRIMM, to confront the alarming rise of “violence-as-a-service”…
Apr 29, 2025Ravie LakshmananEnterprise Security / Vulnerability Google has revealed that it observed 75 zero-day vulnerabilities exploited in the wild…
Jobs requiring technically skilled professionals have more stability than other roles due to their high demand for skills, according to…
A previously undocumented remote access trojan (RAT) named ResolverRAT has surfaced, specifically targeting healthcare and pharmaceutical organizations worldwide. First observed…